Exam Details
Exam Code
:312-39Exam Name
:EC-Council Certified SOC Analyst (CSA)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:100 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-39 Questions & Answers
-
Question 81:
Which of the following Windows features is used to enable Security Auditing in Windows?
A. Bitlocker
B. Windows Firewall
C. Local Group Policy Editor
D. Windows Defender
-
Question 82:
Which of the following is a report writing tool that will help incident handlers to generate efficient reports on detected incidents during incident response process?
A. threat_note
B. MagicTree
C. IntelMQ
D. Malstrom
-
Question 83:
An organization is implementing and deploying the SIEM with following capabilities.
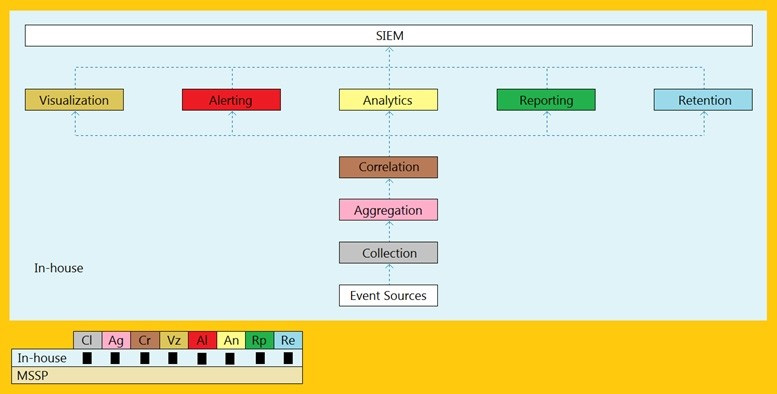
What kind of SIEM deployment architecture the organization is planning to implement?
A. Cloud, MSSP Managed
B. Self-hosted, Jointly Managed C. Self-hosted, Self-Managed
D. Self-hosted, MSSP Managed
-
Question 84:
What is the process of monitoring and capturing all data packets passing through a given network using different tools?
A. Network Scanning
B. DNS Footprinting
C. Network Sniffing
D. Port Scanning
-
Question 85:
Juliea a SOC analyst, while monitoring logs, noticed large TXT, NULL payloads. What does this indicate?
A. Concurrent VPN Connections Attempt
B. DNS Exfiltration Attempt
C. Covering Tracks Attempt
D. DHCP Starvation Attempt
-
Question 86:
Which of the following formula is used to calculate the EPS of the organization?
A. EPS = average number of correlated events / time in seconds
B. EPS = number of normalized events / time in seconds
C. EPS = number of security events / time in seconds
D. EPS = number of correlated events / time in seconds
-
Question 87:
Which of the following technique involves scanning the headers of IP packets leaving a network to make sure that the unauthorized or malicious traffic never leaves the internal network?
A. Egress Filtering
B. Throttling
C. Rate Limiting
D. Ingress Filtering
-
Question 88:
Which of the following command is used to view iptables logs on Ubuntu and Debian distributions?
A. $ tailf /var/log/sys/kern.log
B. $ tailf /var/log/kern.log
C. # tailf /var/log/messages
D. # tailf /var/log/sys/messages
-
Question 89:
According to the Risk Matrix table, what will be the risk level when the probability of an attack is very low and the impact of that attack is major?
A. High
B. Extreme
C. Low
D. Medium
-
Question 90:
The Syslog message severity levels are labelled from level 0 to level 7. What does level 0 indicate?
A. Alert
B. Notification
C. Emergency
D. Debugging
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-39 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.