Exam Details
Exam Code
:312-49V10Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1006 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V10 Questions & Answers
-
Question 191:
Which of the following is a federal law enacted in the US to control the ways that financial institutions deal with the private information of individuals?
A. SOX
B. HIPAA 1996
C. GLBA
D. PCI DSS
-
Question 192:
An investigator enters the command sqlcmd -S WIN-CQQMK62867E -e -s"," -E as part of collecting the primary data file and logs from a database. What does the "WIN-CQQMK62867E” represent?
A. Name of the Database
B. Name of SQL Server
C. Operating system of the system
D. Network credentials of the database
-
Question 193:
In which implementation of RAID will the image of a Hardware RAID volume be different from the image taken separately from the disks?
A. RAID 1
B. The images will always be identical because data is mirrored for redundancy
C. RAID 0
D. It will always be different
-
Question 194:
One technique for hiding information is to change the file extension from the correct one to the one that might not be noticed by an investigator. For example, changing a .jpg extension to a .doc extension so that a picture file appears to be a document. What can an investigator examine to verify that a file has the correct extension?
A. The file header
B. The File Allocation Table
C. The file footer
D. The sector map
-
Question 195:
An attacker has compromised a cloud environment of a company and used the employee information to perform an identity theft attack. Which type of attack is this?
A. Cloud as a subject
B. Cloud as a tool
C. Cloud as an object
D. Cloud as a service
-
Question 196:
Gill is a computer forensics investigator who has been called upon to examine a seized computer. This computer, according to the police, was used by a hacker who gained access to numerous banking institutions to steal customer information. After preliminary investigations, Gill finds in the computer's log files that the hacker was able to gain access to these banks through the use of Trojan horses. The hacker then used these Trojan horses to obtain remote access to the companies’ domain controllers. From this point, Gill found that the hacker pulled off the SAM files from the domain controllers to then attempt and crack network passwords. What is the most likely password cracking technique used by this hacker to break the user passwords from the SAM files?
A. Syllable attack
B. Hybrid attack
C. Brute force attack
D. Dictionary attack
-
Question 197:
Which Event Correlation approach assumes and predicts what an attacker can do next after the attack by studying statistics and probability?
A. Profile/Fingerprint-Based Approach
B. Bayesian Correlation
C. Time (Clock Time) or Role-Based Approach
D. Automated Field Correlation
-
Question 198:
Which of the following stand true for BIOS Parameter Block?
A. The BIOS Partition Block describes the physical layout of a data storage volume
B. The BIOS Partition Block is the first sector of a data storage device
C. The length of BIOS Partition Block remains the same across all the file systems
D. The BIOS Partition Block always refers to the 512-byte boot sector
-
Question 199:
James is dealing with a case regarding a cybercrime that has taken place in Arizona, USA. James needs to lawfully seize the evidence from an electronic device without affecting the user's anonymity. Which of the following law should he comply with, before retrieving the evidence?
A. First Amendment of the U.S. Constitution
B. Fourth Amendment of the U.S. Constitution
C. Third Amendment of the U.S. Constitution
D. Fifth Amendment of the U.S. Constitution
-
Question 200:
What document does the screenshot represent?
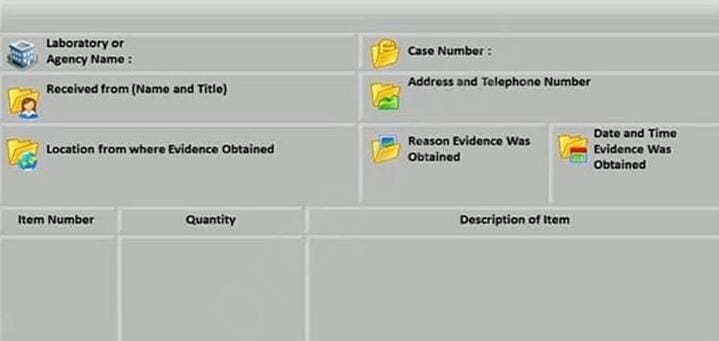
A. Expert witness form
B. Search warrant form
C. Chain of custody form
D. Evidence collection form
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.