Exam Details
Exam Code
:312-49V10Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1006 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V10 Questions & Answers
-
Question 291:
How many bits is Source Port Number in TCP Header packet?
A. 16
B. 48
C. 32
D. 64
-
Question 292:
One technique for hiding information is to change the file extension from the correct one to one that might not be noticed by an investigator. For example, changing a .jpg extension to a .doc extension so that a picture file appears to be a document. What can an investigator examine to verify that a file has the correct extension?
A. the File Allocation Table
B. the file header
C. the file footer
D. the sector map
-
Question 293:
You are contracted to work as a computer forensics investigator for a regional bank that has four 30 TB storage area networks that store customer data. What method would be most efficient for you to acquire digital evidence from this network?
A. Make a bit-stream disk-to-disk file
B. Make a bit-stream disk-to-image file
C. Create a sparse data copy of a folder or file
D. Create a compressed copy of the file with DoubleSpace
-
Question 294:
Windows identifies which application to open a file with by examining which of the following?
A. The File extension
B. The file attributes
C. The file Signature at the end of the file
D. The file signature at the beginning of the file
-
Question 295:
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.
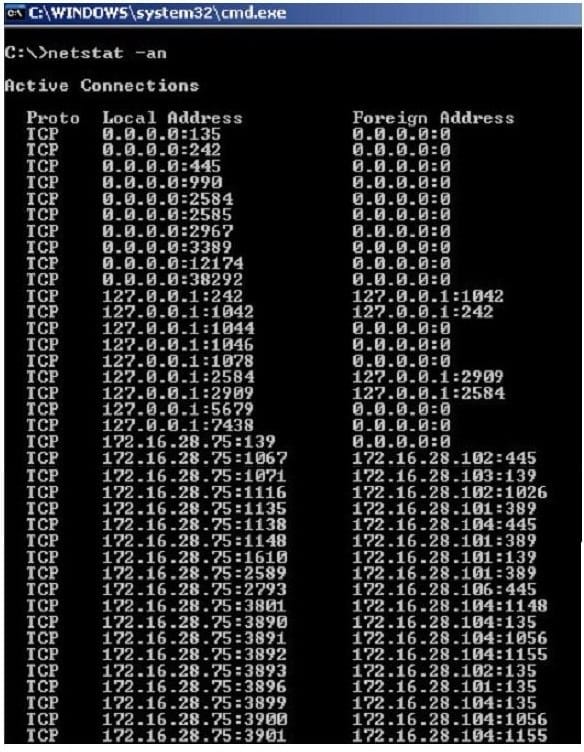
He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?
A. Those connections are established
B. Those connections are in listening mode
C. Those connections are in closed/waiting mode
D. Those connections are in timed out/waiting mode
-
Question 296:
One way to identify the presence of hidden partitions on a suspect hard drive is to:One way to identify the presence of hidden partitions on a suspect? hard drive is to:
A. Add up the total size of all known partitions and compare it to the total size of the hard drive
B. Examine the FAT and identify hidden partitions by noting an ?in the artition Type?fieldExamine the FAT and identify hidden partitions by noting an ??in the ?artition Type?field
C. Examine the LILO and note an ?in the artition Type?fieldExamine the LILO and note an ??in the ? artition Type?field It is not possible to have hidden partitions on a hard drive
-
Question 297:
Julie is a college student majoring in Information Systems and Computer Science. She is currently writing an essay for her computer crimes class. Julie paper focuses on white- collar crimes in America and how forensics investigators investigate the cases. Julie would like to focus the subjectJulie? paper focuses on white-collar crimes in America and how forensics investigators investigate the cases. Julie would like to focus the subject of the essay on the most common type of crime found in corporate America. What crime should Julie focus on?
A. Physical theft
B. Copyright infringement
C. Industrial espionage
D. Denial of Service attacks
-
Question 298:
An "idle" system is also referred to as what?
A. PC not connected to the Internet
B. PC not being used
C. Zombie
D. Bot
-
Question 299:
You are working as an independent computer forensics investigator and receive a call from a systems administrator for a local school system requesting your assistance. One of the students at the local high school is suspected of downloading inappropriate images from the Internet to a PC in the Computer Lab. When you arrive at the school, the systems administrator hands you a hard drive and tells you that he made a implePC in the Computer Lab. When you arrive at the school, the systems administrator hands you a hard drive and tells you that he made a ?imple backup copy?of the hard drive in the PC and put it on this drive and requests that you examine the drive for evidence of the suspected images. You inform him that a imple backup copy?will not provide deleted files or recover file fragments. What type of copy do you need to make toYou inform him that a ?imple backup copy?will not provide deleted files or recover file fragments. What type of copy do you need to make to ensure that the evidence found is complete and admissible in future proceedings?
A. Bit-stream copy
B. Robust copy
C. Full backup copy
D. Incremental backup copy
-
Question 300:
What will the following command produce on a website login page?
SELECT email, passwd, login_id, full_name FROM members
WHERE email = '[email protected]';
DROP TABLE members; --'
A. Retrieves the password for the first user in the members table
B. This command will not produce anything since the syntax is incorrect
C. Deletes the entire members table
D. Inserts the Error! Reference source not found. email address into the members table
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.