Exam Details
Exam Code
:312-49V10Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1006 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V10 Questions & Answers
-
Question 351:
What binary coding is used most often for e-mail purposes?
A. SMTP
B. Uuencode
C. IMAP
D. MIME
-
Question 352:
When investigating a computer forensics case where Microsoft Exchange and Blackberry Enterprise server are used, where would investigator need to search to find email sent from a Blackberry device?
A. RIM Messaging center
B. Blackberry Enterprise server
C. Microsoft Exchange server
D. Blackberry desktop redirector
-
Question 353:
When obtaining a warrant it is important to:
A. particularly describe the place to be searched and particularly describe the items to be seized
B. generally describe the place to be searched and particularly describe the items to be seized
C. generally describe the place to be searched and generally describe the items to be seized
D. particularly describe the place to be searched and generally describe the items to be seized
-
Question 354:
Kimberly is studying to be an IT security analyst at a vocational school in her town. The school offers many different programming as well as networking languages. What networking protocol language should she learn that routers utilize?
A. BPG
B. ATM
C. OSPF
D. UDP
-
Question 355:
On Linux/Unix based Web servers, what privilege should the daemon service be run under?
A. Something other than root
B. Root
C. Guest
D. You cannot determine what privilege runs the daemon service
-
Question 356:
Jim performed a vulnerability analysis on his network and found no potential problems. He runs another utility that executes exploits against his system to verify the results of the vulnerability test. The second utility executes five known exploits against his network in which the vulnerability analysis said were not exploitable. What kind of results did Jim receive from his vulnerability analysis?
A. False negatives
B. True negatives
C. True positives
D. False positives
-
Question 357:
E-mail logs contain which of the following information to help you in your investigation? (Select up to 4)
A. user account that was used to send the account
B. attachments sent with the e-mail message
C. unique message identifier
D. contents of the e-mail message
E. date and time the message was sent
-
Question 358:
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd.
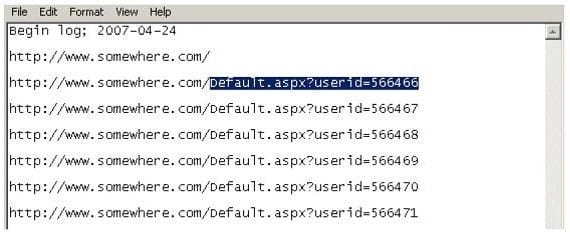
From the log, the investigator can see where the person in question went on the Internet. From the log, it
appears that the user was manually typing in different user ID numbers.
What technique this user was trying?
A. Parameter tampering
B. Cross site scripting
C. SQL injection
D. Cookie Poisoning
-
Question 359:
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
A. ICMP ping sweep
B. Ping trace
C. Tracert
D. Smurf scan
-
Question 360:
In a computer forensics investigation, what describes the route that evidence takes from the time you find it until the case is closed or goes to court?
A. Policy of separation
B. Chain of custody
C. Rules of evidence
D. Law of probability
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.