Exam Details
Exam Code
:312-49V9Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:531 Q&AsLast Updated
:Apr 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V9 Questions & Answers
-
Question 91:
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
A. ICMP ping sweep
B. Ping trace
C. Tracert
D. Smurf scan
-
Question 92:
In a computer forensics investigation, what describes the route that evidence takes from the time you find it until the case is closed or goes to court?
A. Policy of separation
B. Chain of custody
C. Rules of evidence
D. Law of probability
-
Question 93:
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd.
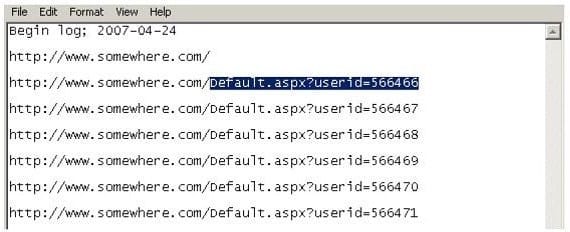
From the log, the investigator can see where the person in question went on the Internet. From the log, it
appears that the user was manually typing in different user ID numbers.
What technique this user was trying?
A. Parameter tampering
B. Cross site scripting
C. SQL injection
D. Cookie Poisoning
-
Question 94:
E-mail logs contain which of the following information to help you in your investigation? (Select up to 4)
A. user account that was used to send the account
B. attachments sent with the e-mail message
C. unique message identifier
D. contents of the e-mail message
E. date and time the message was sent
-
Question 95:
Lance wants to place a honeypot on his network. Which of the following would be your recommendations?
A. Use a system that has a dynamic addressing on the network
B. Use a system that is not directly interacing with the router
C. Use it on a system in an external DMZ in front of the firewall
D. It doesn't matter as all replies are faked
-
Question 96:
Before performing a logical or physical search of a drive in Encase, what must be added to the program?
A. File signatures
B. Keywords
C. Hash sets
D. Bookmarks
-
Question 97:
Melanie was newly assigned to an investigation and asked to make a copy of all the evidence from the compromised system. Melanie did a DOS copy of all the files on the system. What would be the primary reason for you to recommend a disk imaging tool?
A. A disk imaging tool would check for CRC32s for internal self checking and validation and have MD5 checksum
B. Evidence file format will contain case data entered by the examiner and encrypted at the beginning of the evidence file
C. A simple DOS copy will not include deleted files, file slack and other information
D. There is no case for an imaging tool as it will use a closed, proprietary format that if compared to the original will not match up sector for sector
-
Question 98:
If you see the files Zer0.tar.gz and copy.tar.gz on a Linux system while doing an investigation, what can you conclude?
A. The system has been compromised using a t0rnrootkit
B. The system administrator has created an incremental backup
C. The system files have been copied by a remote attacker
D. Nothing in particular as these can be operational files
-
Question 99:
As a CHFI professional, which of the following is the most important to your professional reputation?
A. Your Certifications
B. The correct, successful management of each and every case
C. The free that you charge
D. The friendship of local law enforcement officers
-
Question 100:
You are a security analyst performing a penetration tests for a company in the Midwest. After some initial reconnaissance, you discover the IP addresses of some Cisco routers used by the company. You type in the following URL that includes the IP address of one of the routers:
http://172.168.4.131/level/99/exec/show/config
After typing in this URL, you are presented with the entire configuration file for that router. What have you discovered?
A. URL Obfuscation Arbitrary Administrative Access Vulnerability
B. HTML Configuration Arbitrary Administrative Access Vulnerability
C. Cisco IOS Arbitrary Administrative Access Online Vulnerability
D. HTTP Configuration Arbitrary Administrative Access Vulnerability
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V9 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.