Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 07, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 101:
What port scanning method involves sending spoofed packets to a target system and then looking for adjustments to the IPID on a zombie system?
A. Blind Port Scanning
B. Idle Scanning
C. Bounce Scanning
D. Stealth Scanning
E. UDP Scanning
-
Question 102:
An Nmap scan shows the following open ports, and nmap also reports that the OS guessing results to match too many signatures hence it cannot reliably be identified:
21 ftp 23 telnet 80 http 443 https
What does this suggest ?
A. This is a Windows Domain Controller
B. The host is not firewalled
C. The host is not a Linux or Solaris system
D. The host is not properly patched
-
Question 103:
John has scanned the web server with NMAP. However, he could not gather enough information to help him identify the operating system running on the remote host accurately. What would you suggest to John to help identify the OS that is being used on the remote web server?
A. Connect to the web server with a browser and look at the web page.
B. Connect to the web server with an FTP client.
C. Telnet to port 8080 on the web server and look at the default page code.
D. Telnet to an open port and grab the banner.
-
Question 104:
You are having problems while retrieving results after performing port scanning during internal testing. You verify that there are no security devices between you and the target system. When both stealth and connect scanning do not work, you decide to perform a NULL scan with NMAP. The first few systems scanned shows all ports open.
Which one of the following statements is probably true?
A. The systems have all ports open.
B. The systems are running a host based IDS.
C. The systems are web servers.
D. The systems are running Windows.
-
Question 105:
What are twp types of ICMP code used when using the ping command?
A. It uses types 0 and 8.
B. It uses types 13 and 14.
C. It uses types 15 and 17.
D. The ping command does not use ICMP but uses UDP.
-
Question 106:
You are scanning into the target network for the first time. You find very few conventional ports open. When you attempt to perform traditional service identification by connecting to the open ports, it yields either unreliable or no results. You are unsure of which protocols are being used. You need to discover as many different protocols as possible.
Which kind of scan would you use to achieve this? (Choose the best answer)
A. Nessus scan with TCP based pings.
B. Nmap scan with the sP (Ping scan) switch.
C. Netcat scan with the u e switches.
D. Nmap with the sO (Raw IP packets) switch.
-
Question 107:
An attacker is attempting to telnet into a corporation's system in the DMZ. The attacker doesn't want to get caught and is spoofing his IP address. After numerous tries he remains unsuccessful in connecting to the system. The attacker rechecks that the target system is actually listening on Port 23 and he verifies it with both nmap and hping2. He is still unable to connect to the target system.
What is the most probable reason?
A. The firewall is blocking port 23 to that system.
B. He cannot spoof his IP and successfully use TCP.
C. He needs to use an automated tool to telnet in.
D. He is attacking an operating system that does not reply to telnet even when open.
-
Question 108:
War dialing is a very old attack and depicted in movies that were made years ago. Why would a modem security tester consider using such an old technique?
A. It is cool, and if it works in the movies it must work in real life.
B. It allows circumvention of protection mechanisms by being on the internal network.
C. It allows circumvention of the company PBX.
D. A good security tester would not use such a derelict technique.
-
Question 109:
What type of port scan is shown below?
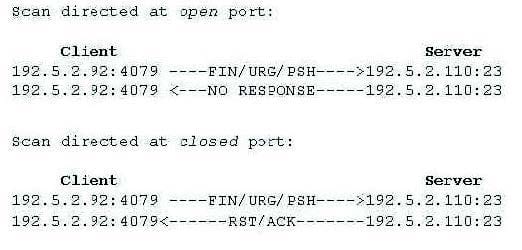
A. Idle Scan
B. Windows Scan
C. XMAS Scan
D. SYN Stealth Scan
-
Question 110:
Ann would like to perform a reliable scan against a remote target. She is not concerned about being stealth at this point. Which of the following type of scans would be the most accurate and reliable option?
A. A half-scan
B. A UDP scan
C. A TCP Connect scan
D. A FIN scan
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.