Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 241:
Harold is the senior security analyst for a small state agency in New York. He has no other security professionals that work under him, so he has to do all the security-related tasks for the agency. Coming from a computer hardware background, Harold does not have a lot of experience with security methodologies and technologies, but he was the only one who applied for the position.
Harold is currently trying to run a Sniffer on the agency's network to get an idea of what kind of traffic is being passed around but the program he is using does not seem to be capturing anything. He pours through the sniffer's manual but can't find anything that directly relates to his problem. Harold decides to ask the network administrator if the has any thoughts on the problem. Harold is told that the sniffer was not working because the agency's network is a switched network, which can't be sniffed by some programs without some tweaking.
What technique could Harold use to sniff agency's switched network?
A. ARP spoof the default gateway
B. Conduct MiTM against the switch
C. Launch smurf attack against the switch
D. Flood switch with ICMP packets
-
Question 242:
Ethernet switches can be adversely affected by rapidly bombarding them with spoofed ARP responses. He port to MAC Address table (CAM Table) overflows on the switch and rather than failing completely, moves into broadcast mode, then the hacker can sniff all of the packets on the network.
Which of the following tool achieves this?
A. ./macof
B. ./sniffof
C. ./dnsiff
D. ./switchsnarf
-
Question 243:
Daryl is a network administrator working for Dayton Technologies. Since Daryl's background is in web application development, many of the programs and applications his company uses are web-based. Daryl sets up a simple forms-based logon screen for all the applications he creates so they are secure.
The problem Daryl is having is that his users are forgetting their passwords quite often and sometimes he does not have the time to get into his applications and change the passwords for them. Daryl wants a tool or program that can monitor web-based passwords and notify him when a password has been changed so he can use that tool whenever a user calls him and he can give them their password right then.
What tool would work best for Daryl's needs?
A. Password sniffer
B. L0phtcrack
C. John the Ripper
D. WinHttrack
-
Question 244:
You are sniffing as unprotected WiFi network located in a JonDonalds Cybercafe with Ethereal to capture hotmail e-mail traffic. You see lots of people using their laptops browsing the web while snipping brewed coffee from JonDonalds. You want to sniff their email message traversing the unprotected WiFi network.
Which of the following ethereal filters will you configure to display only the packets with the hotmail messages?
A. (http contains "hotmail") andand ( http contains "Reply-To")
B. (http contains "e-mail" ) andand (http contains "hotmail")
C. (http = "login.passport.com" ) andand (http contains "SMTP")
D. (http = "login.passport.com" ) andand (http contains "POP3")
-
Question 245:
Exhibit:
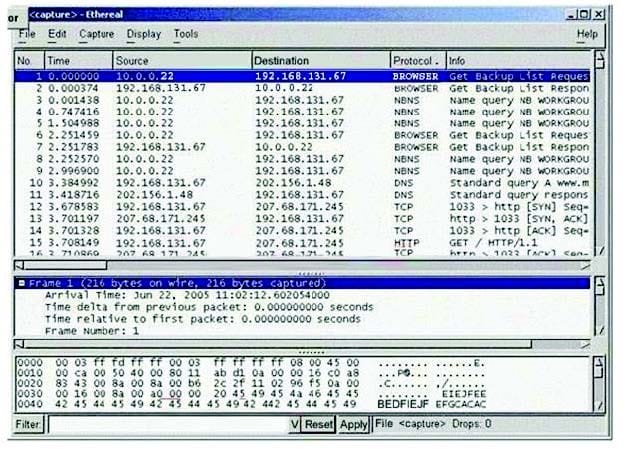
You have captured some packets in Ethereal. You want to view only packets sent from 10.0.0.22. What filter will you apply?
A. ip = 10.0.0.22
B. ip.src == 10.0.0.22
C. ip.equals 10.0.0.22
D. ip.address = 10.0.0.22
-
Question 246:
How would you describe a simple yet very effective mechanism for sending and receiving unauthorized information or data between machines without alerting any firewalls and IDS's on a network?
A. Covert Channel
B. Crafted Channel
C. Bounce Channel
D. Deceptive Channel
-
Question 247:
ARP poisoning is achieved in _____ steps
A. 1
B. 2
C. 3
D. 4
-
Question 248:
What is the command used to create a binary log file using tcpdump?
A. tcpdump -r log
B. tcpdump -w ./log
C. tcpdump -vde -r log
D. tcpdump -l /var/log/
-
Question 249:
Which of the following is not considered to be a part of active sniffing?
A. MAC Flooding
B. ARP Spoofing
C. SMAC Fueling
D. MAC Duplicating
-
Question 250:
What port number is used by Kerberos protocol?
A. 44
B. 88
C. 419
D. 487
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.