Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 481:
If you come across a sheepdip machine at your client's site, what should you do?
A. A sheepdip computer is used only for virus-checking.
B. A sheepdip computer is another name for a honeypot
C. A sheepdip coordinates several honeypots.
D. A sheepdip computers defers a denial of service attack.
-
Question 482:
What is a sheepdip?
A. It is another name for Honeynet
B. It is a machine used to coordinate honeynets
C. It is the process of checking physical media for virus before they are used in a computer
D. None of the above
-
Question 483:
All the web servers in the DMZ respond to ACK scan on port 80. Why is this happening ?
A. They are all Windows based webserver
B. They are all Unix based webserver
C. The company is not using IDS
D. The company is not using a stateful firewall
-
Question 484:
While examining a log report you find out that an intrusion has been attempted by a machine whose IP address is displayed as 0xde.0xad.0xbe.0xef. It looks to you like a hexadecimal number. You perform a ping 0xde.0xad.0xbe.0xef. Which of the following IP addresses will respond to the ping and hence will likely be responsible for the the intrusion ?
A. 192.10.25.9
B. 10.0.3.4
C. 203.20.4.5
D. 222.273.290.239
E. 222.173.290.239
-
Question 485:
You are doing IP spoofing while you scan your target. You find that the target has port 23 open.Anyway you are unable to connect. Why?
A. A firewall is blocking port 23
B. You cannot spoof + TCP
C. You need an automated telnet tool
D. The OS does not reply to telnet even if port 23 is open
-
Question 486:
Statistics from cert.org and other leading security organizations has clearly showed a steady rise in the number of hacking incidents perpetrated against companies. What do you think is the main reason behind the significant increase in hacking attempts over the past years?
A. It is getting more challenging and harder to hack for non technical people.
B. There is a phenomenal increase in processing power.
C. New TCP/IP stack features are constantly being added.
D. The ease with which hacker tools are available on the Internet.
-
Question 487:
When referring to the Domain Name Service, what is denoted by a `zone'?
A. It is the first domain that belongs to a company.
B. It is a collection of resource records.
C. It is the first resource record type in the SOA.
D. It is a collection of domains.
-
Question 488:
The following excerpt is taken from a honeypot log. The log captures activities across three days. There are several intrusion attempts; however, a few are successful. From the options given below choose the one best interprets the following
entry:
Apr 26 06:43:05 [6282] IDS181/nops-x86: 63.226.81.13:1351 -> 172.16.1.107:53
(Note: The objective of this question is to test whether the student can read basic information from log entries and interpret the nature of attack.)
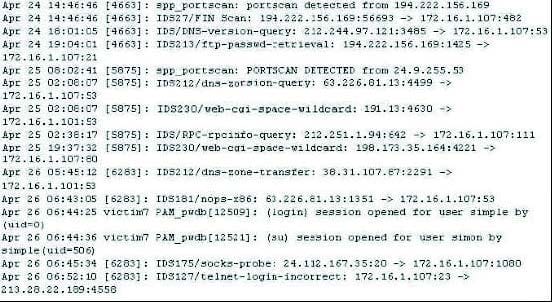
Interpret the following entry:
Apr 26 06:43:05 [6283]: IDS181/nops-x86: 63.226.81.13:1351 -> 172.16.1.107.53
A. An IDS evasion technique
B. A buffer overflow attempt
C. A DNS zone transfer
D. Data being retrieved from 63.226.81.13.
-
Question 489:
Snort is an open source Intrusion Detection system. However, it can also be used for a few other purposes as well. Which of the choices below indicate the other features offered by Snort?
A. IDS, Packet Logger, Sniffer
B. IDS, Firewall, Sniffer
C. IDS, Sniffer, Proxy
D. IDS, Sniffer, content inspector
-
Question 490:
Bill has successfully executed a buffer overflow against a Windows IIS web server. He has been able to spawn an interactive shell and plans to deface the main web page. He first attempts to use the "Echo" command to simply overwrite index.html and remains unsuccessful. He then attempts to delete the page and achieves no progress. Finally, he tries to overwrite it with another page again in vain.
What is the probable cause of Bill's problem?
A. The system is a honeypot.
B. There is a problem with the shell and he needs to run the attack again.
C. You cannot use a buffer overflow to deface a web page.
D. The HTML file has permissions of ready only.
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.