Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Apr 16, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 501:
Why would an ethical hacker use the technique of firewalking?
A. It is a technique used to discover wireless network on foot.
B. It is a technique used to map routers on a network link.
C. It is a technique used to discover the nature of rules configured on a gateway.
D. It is a technique used to discover interfaces in promiscuous mode.
-
Question 502:
Which one of the following attacks will pass through a network layer intrusion detection system undetected?
A. A teardrop attack
B. A SYN flood attack
C. A DNS spoofing attack
D. A test.cgi attack
-
Question 503:
Once an intruder has gained access to a remote system with a valid username and password, the attacker will attempt to increase his privileges by escalating the used account to one that has increased privileges. such as that of an administrator. What would be the best countermeasure to protect against escalation of priveges?
A. Give users tokens
B. Give user the least amount of privileges
C. Give users two passwords
D. Give users a strong policy document
-
Question 504:
You are attempting to map out the firewall policy for an organization. You discover your target system is one hop beyond the firewall. Using hping2, you send SYN packets with the exact TTL of the target system starting at port 1 and going up to port 1024. What is this process known as?
A. Footprinting
B. Firewalking
C. Enumeration
D. Idle scanning
-
Question 505:
Exhibit
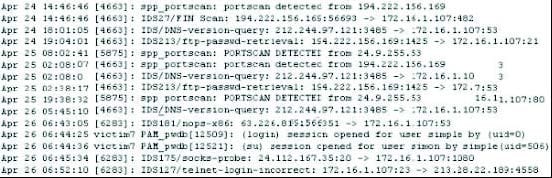
Study the log given in the exhibit,
Precautionary measures to prevent this attack would include writing firewall rules. Of these firewall rules, which among the following would be appropriate?
A. Disallow UDP 53 in from outside to DNS server
B. Allow UDP 53 in from DNS server to outside
C. Disallow TCP 53 in from secondaries or ISP server to DNS server
D. Block all UDP traffic
-
Question 506:
Which programming language is NOT vulnerable to buffer overflow attacks?
A. Java
B. ActiveX
C. C++
D. Assembly Language
-
Question 507:
Buffer X in an Accounting application module for Brownies Inc. can contain 200 characters. The programmer makes an assumption that 200 characters are more than enough. Because there were no proper boundary checks being conducted, Bob decided to insert 400 characters into the 200-character buffer. (Overflows the buffer). Below is the code snippet.
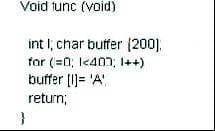
How can you protect/fix the problem of your application as shown above?
A. Because the counter starts with 0, we would stop when the counter is less than 200
B. Because the counter starts with 0, we would stop when the counter is more than 200
C. Add a separate statement to signify that if we have written 200 characters to the buffer, the stack should stop because it can't hold any more data
D. Add a separate statement to signify that if we have written less than 200 characters to the buffer, the stack should stop because it can't hold any more data
-
Question 508:
In Buffer Overflow exploit, which of the following registers gets overwritten with return address of the exploit code?
A. EIP
B. ESP
C. EAP
D. EEP
-
Question 509:
When writing shellcodes, you must avoid _________________ because these will end the string.

A. Null Bytes
B. Root Bytes
C. Char Bytes
D. Unicode Bytes
-
Question 510:
Which of the following built-in C/C++ functions you should avoid to prevent your program from buffer overflow attacks?
A. strcpy()
B. strcat()
C. streadd()
D. strscock()
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.