Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Apr 15, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 131:
Your computer is infected by E-mail tracking and spying Trojan. This Trojan infects the computer with a single file - emos.sys
Which step would you perform to detect this type of Trojan?
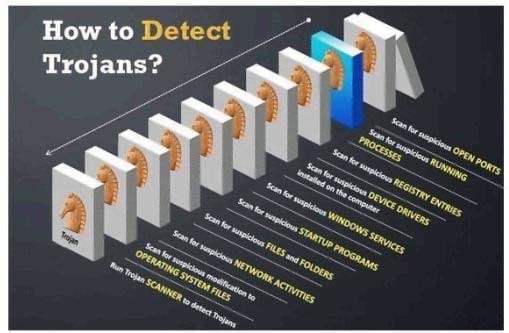
A. Scan for suspicious startup programs using msconfig
B. Scan for suspicious network activities using Wireshark
C. Scan for suspicious device drivers in c:\windows\system32\drivers
D. Scan for suspicious open ports using netstat
-
Question 132:
In the context of Trojans, what is the definition of a Wrapper?
A. An encryption tool to protect the Trojan
B. A tool used to bind the Trojan with a legitimate file
C. A tool used to calculate bandwidth and CPU cycles wasted by the Trojan
D. A tool used to encapsulate packets within a new header and footer
-
Question 133:
You just purchased the latest DELL computer, which comes pre-installed with Windows 7, McAfee antivirus software and a host of other applications. You want to connect Ethernet wire to your cable modem and start using the computer immediately. Windows is dangerously insecure when unpacked from the box, and there are a few things that you must do before you use it.
A. New installation of Windows should be patched by installing the latest service packs and hotfixes
B. Key applications such as Adobe Acrobat,Macromedia Flash,Java,Winzip etc.,must have the latest security patches installed
C. Install a personal firewall and lock down unused ports from connecting to your computer
D. Install the latest signatures for Antivirus software
E. Configure "Windows Update" to automatic
F. Create a non-admin user with a complex password and logon to this account
G. You can start using your computer as vendors such as DELL,HP and IBM would have already installed the latest service packs.
-
Question 134:
You want to hide a secret.txt document inside c:\windows\system32\tcpip.dll kernel library using ADS streams.
How will you accomplish this?
A. copy secret.txt c:\windows\system32\tcpip.dll kernel>secret.txt
B. copy secret.txt c:\windows\system32\tcpip.dll:secret.txt
C. copy secret.txt c:\windows\system32\tcpip.dll |secret.txt
D. copy secret.txt >< c:\windows\system32\tcpip.dll kernel secret.txt
-
Question 135:
SNMP is a connectionless protocol that uses UDP instead of TCP packets (True or False)
A. true
B. false
-
Question 136:
TCP/IP Session Hijacking is carried out in which OSI layer?
A. Datalink layer
B. Transport layer
C. Network layer
D. Physical layer
-
Question 137:
In which part of OSI layer, ARP Poisoning occurs?
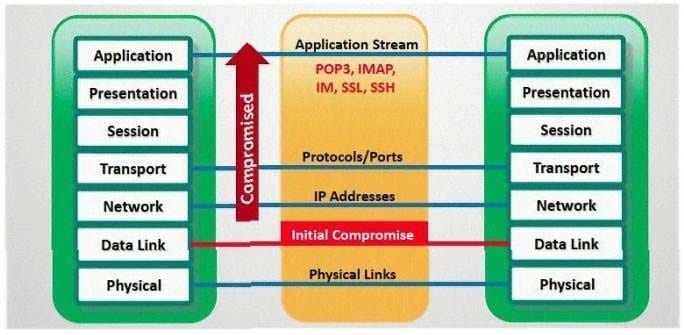
A. Transport Layer
B. Datalink Layer
C. Physical Layer
D. Application layer
-
Question 138:
What is the correct command to run Netcat on a server using port 56 that spawns command shell when connected?
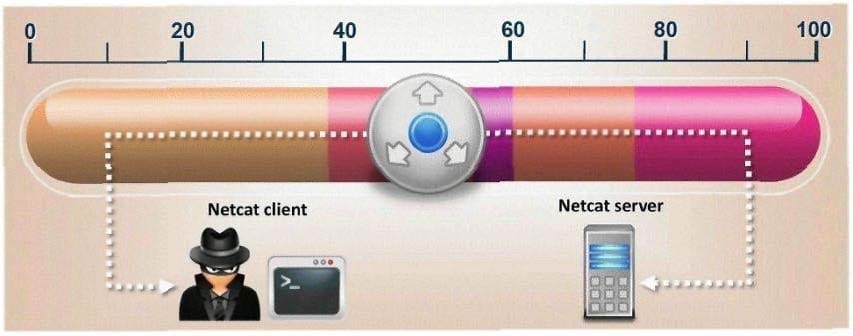
A. nc -port 56 -s cmd.exe
B. nc -p 56 -p -e shell.exe
C. nc -r 56 -c cmd.exe
D. nc -L 56 -t -e cmd.exe
-
Question 139:
This attack uses social engineering techniques to trick users into accessing a fake Web site and divulging personal information. Attackers send a legitimate- looking e-mail asking users to update their information on the company's Web site, but the URLs in the e-mail actually point to a false Web site.
A. Wiresharp attack
B. Switch and bait attack
C. Phishing attack
D. Man-in-the-Middle attack
-
Question 140:
Which of the following statements would NOT be a proper definition for a Trojan Horse?
A. An authorized program that has been designed to capture keyboard keystroke while the user is unaware of such activity being performed
B. An unauthorized program contained within a legitimate program. This unauthorized program performs functions unknown (and probably unwanted) by the user
C. A legitimate program that has been altered by the placement of unauthorized code within it; this code performs functions unknown (and probably unwanted) by the user
D. Any program that appears to perform a desirable and necessary function but that (because of unauthorized code within it that is unknown to the user) performs functions unknown (and definitely unwanted) by the user
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.