Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Apr 15, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 141:
Syslog is a standard for logging program messages. It allows separation of the software that generates
messages from the system that stores them and the software that reports and analyzes them. It also provides devices, which would otherwise be unable to communicate a means to notify administrators of problems or performance.
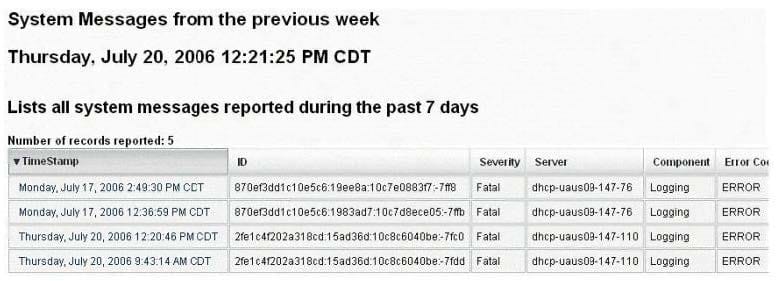
What default port Syslog daemon listens on?
A. 242
B. 312
C. 416
D. 514
-
Question 142:
How many bits encryption does SHA-1 use?
A. 64 bits
B. 128 bits
C. 256 bits
D. 160 bits
-
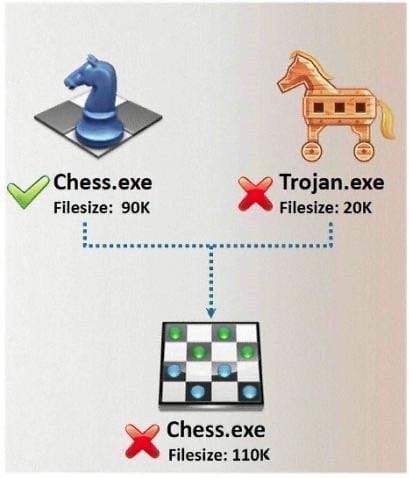
Question 143:
In Trojan terminology, what is required to create the executable file chess.exe as shown below?
A. Mixer
B. Converter
C. Wrapper
D. Zipper
-
Question 144:
Peter extracts the SID list from Windows 2008 Server machine using the hacking tool "SIDExtracter". Here is the output of the SIDs:
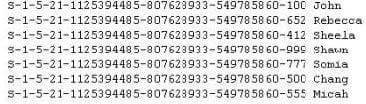
From the above list identify the user account with System Administrator privileges?
A. John
B. Rebecca
C. Sheela
D. Shawn
E. Somia
F. Chang
G. Micah
-
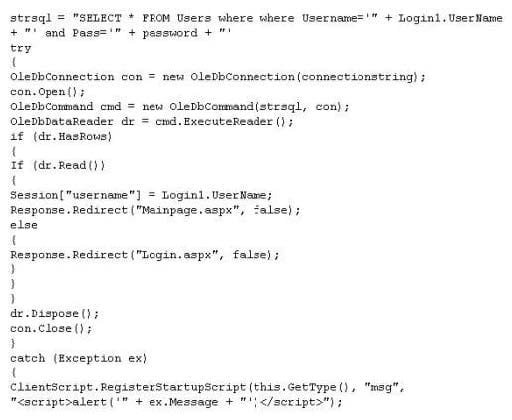
Question 145:
What is the problem with this ASP script (login.asp)?
A. The ASP script is vulnerable to Cross Site Scripting attack
B. The ASP script is vulnerable to Session Splice attack
C. The ASP script is vulnerable to XSS attack
D. The ASP script is vulnerable to SQL Injection attack
-
Question 146:
Google uses a unique cookie for each browser used by an individual user on a computer.
This cookie contains information that allows Google to identify records about that user on its database.
This cookie is submitted every time a user launches a Google search, visits a site using AdSense etc. The
information stored in Google's database, identified by the cookie, includes.
How would you prevent Google from storing your search keywords?
A. Block Google Cookie by applying Privacy and Security settings in your web browser
B. Disable the Google cookie using Google Advanced Search settings on Google Search page
C. Do not use Google but use another search engine Bing which will not collect and store your search keywords
D. Use MAC OS X instead of Windows 7. Mac OS has higher level of privacy controls by default.
-
Question 147:
Jayden is a network administrator for her company. Jayden wants to prevent MAC spoofing on all the Cisco switches in the network.
How can she accomplish this?
A. Jayden can use the commanD. ip binding set.
B. Jayden can use the commanD. no ip spoofing.
C. She should use the commanD. no dhcp spoofing.
D. She can use the commanD. ip dhcp snooping binding.
-
Question 148:
In TCP communications there are 8 flags; FIN, SYN, RST, PSH, ACK, URG, ECE, CWR.
These flags have decimal numbers assigned to them:
FIN = 1
SYN = 2
RST = 4
PSH = 8
ACK = 16
URG = 32
ECE = 64
CWR = 128 Jason is the security administrator of ASPEN Communications. He analyzes some traffic using Wireshark and has enabled the following filters.
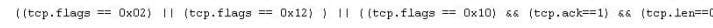
What is Jason trying to accomplish here?
A. SYN,FIN,URG and PSH
B. SYN,SYN/ACK,ACK
C. RST,PSH/URG,FIN
D. ACK,ACK,SYN,URG
-
Question 149:
Neil is a network administrator working in Istanbul. Neil wants to setup a protocol analyzer on his network that will receive a copy of every packet that passes through the main office switch.
What type of port will Neil need to setup in order to accomplish this?
A. Neil will have to configure a Bridged port that will copy all packets to the protocol analyzer.
B. Neil will need to setup SPAN port that will copy all network traffic to the protocol analyzer.
C. He will have to setup an Ether channel port to get a copy of all network traffic to the analyzer.
D. He should setup a MODS port which will copy all network traffic.
-
Question 150:
What type of port scan is shown below?

A. Idle Scan
B. FIN Scan
C. XMAS Scan
D. Windows Scan
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.