Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Apr 15, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 181:
Jimmy, an attacker, knows that he can take advantage of poorly designed input validation routines to create or alter SQL commands to gain access to private data or execute commands in the database.
What technique does Jimmy use to compromise a database?
A. Jimmy can submit user input that executes an operating system command to compromise a target system
B. Jimmy can gain control of system to flood the target system with requests,preventing legitimate users from gaining access
C. Jimmy can utilize an incorrect configuration that leads to access with higher-than expected privilege of the database
D. Jimmy can utilize this particular database threat that is an SQL injection technique to penetrate a target system
-
Question 182:
Which of the following countermeasure can specifically protect against both the MAC Flood and MAC Spoofing attacks?
A. Configure Port Security on the switch
B. Configure Port Recon on the switch
C. Configure Switch Mapping
D. Configure Multiple Recognition on the switch
-
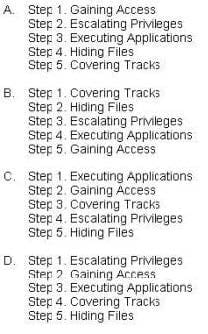
Question 183:
What is the correct order of steps in CEH System Hacking Cycle?
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 184:
Identify SQL injection attack from the HTTP requests shown below:
A. http://www.myserver.c0m/search.asp? lname=smith%27%3bupdate%20usertable%20set%20passwd%3d%27hAx0r%27%3b--%00
B. http://www.myserver.c0m/script.php?mydata=%3cscript%20src=%22
C. http%3a%2f%2fwww.yourserver.c0m%2fbadscript.js%22%3e%3c%2fscript%3e
D. http://www.victim.com/example accountnumber=67891andcreditamount=999999999
-
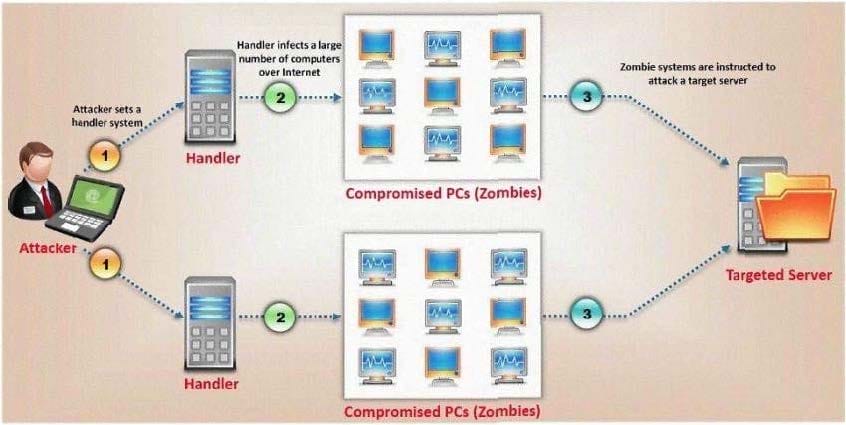
Question 185:
What type of attack is shown here?
A. Bandwidth exhaust Attack
B. Denial of Service Attack
C. Cluster Service Attack
D. Distributed Denial of Service Attack
-
Question 186:
Joseph has just been hired on to a contractor company of the Department of Defense as their Senior Security Analyst. Joseph has been instructed on the company's strict security policies that have been implemented, and the policies that have yet to be put in place. Per the Department of Defense, all DoD users and the users of their contractors must use two-factor authentication to access their networks. Joseph has been delegated the task of researching and implementing the best two-factor authentication method for his company.
Joseph's supervisor has told him that they would like to use some type of hardware device in tandem with a security or identifying pin number. Joseph's company has already researched using smart cards and all the resources needed to implement them, but found the smart cards to not be cost effective.
What type of device should Joseph use for two-factor authentication?
A. Biometric device
B. OTP
C. Proximity cards
D. Security token
-
Question 187:
Which definition below best describes a covert channel?
A. A server program using a port that is not well known
B. Making use of a protocol in a way it was not intended to be used
C. It is the multiplexing taking place on a communication link
D. It is one of the weak channels used by WEP that makes it insecure
-
Question 188:
In which step Steganography fits in CEH System Hacking Cycle (SHC)
A. Step 2: Crack the password
B. Step 1: Enumerate users
C. Step 3: Escalate privileges
D. Step 4: Execute applications
E. Step 5: Hide files
F. Step 6: Cover your tracks
-
Question 189:
Buffer X in an Accounting application module for Brownies Inc. can contain 200 characters.
The programmer makes an assumption that 200 characters are more than enough.
Because there were no proper boundary checks being conducted, Bob decided to insert 400 characters
into the 200-character buffer. (Overflows the buffer).
Below is the code snippet:

How can you protect/fix the problem of your application as shown above?
A. Because the counter starts with 0,we would stop when the counter is less than 200
B. Because the counter starts with 0,we would stop when the counter is more than 200
C. Add a separate statement to signify that if we have written less than 200 characters to the buffer,the stack should stop because it cannot hold any more data
D. Add a separate statement to signify that if we have written 200 characters to the buffer,the stack should stop because it cannot hold any more data
-
Question 190:
Which of the following encryption is NOT based on block cipher?
A. DES
B. Blowfish
C. AES (Rijndael)
D. RC4
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.