Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Apr 15, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 341:
Jeremy is web security consultant for Information Securitas. Jeremy has just been hired to perform contract work for a large state agency in Michigan. Jeremy's first task is to scan all the company's external websites. Jeremy comes upon a login page which appears to allow employees access to sensitive areas on the website. James types in the following statement in the username field:
SELECT * from Users where username='admin' ?AND password='' AND email like '%@testers.com%'
What will the SQL statement accomplish?
A. If the page is susceptible to SQL injection,it will look in the Users table for usernames of admin
B. This statement will look for users with the name of admin,blank passwords,and email addresses that end in @testers.com
C. This Select SQL statement will log James in if there are any users with NULL passwords
D. James will be able to see if there are any default user accounts in the SQL database
-
Question 342:
A majority of attacks come from insiders, people who have direct access to a company's computer system as part of their job function or a business relationship.
Who is considered an insider?
A. A competitor to the company because they can directly benefit from the publicity generated by making such an attack
B. Disgruntled employee,customers,suppliers,vendors,business partners,contractors,temps,and consultants
C. The CEO of the company because he has access to all of the computer systems
D. A government agency since they know the company's computer system strengths and weaknesses
-
Question 343:
Kevin is an IT security analyst working for Emerson Time Makers, a watch manufacturing company in Miami. Kevin and his girlfriend Katy recently broke up after a big fight. Kevin believes that she was seeing another person. Kevin, who has an online email account that he uses for most of his mail, knows that Katy has an account with that same company.
Kevin logs into his email account online and gets the following URL after successfully logged in: http:// www.youremailhere.com/mail.asp? mailbox=KevinandSmith=121%22 Kevin changes the URL to:
http://www.youremailhere.com/mail.asp?mailbox=KatyandSanchez=121%22 Kevin is trying to access her email account to see if he can find out any information.
What is Kevin attempting here to gain access to Katy's mailbox?
A. This type of attempt is called URL obfuscation when someone manually changes a URL to try and gain unauthorized access
B. By changing the mailbox's name in the URL,Kevin is attempting directory transversal
C. Kevin is trying to utilize query string manipulation to gain access to her email account
D. He is attempting a path-string attack to gain access to her mailbox
-
Question 344:
You want to perform advanced SQL Injection attack against a vulnerable website. You are unable to perform command shell hacks on this server.
What must be enabled in SQL Server to launch these attacks?
A. System services
B. EXEC master access
C. xp_cmdshell
D. RDC
-
Question 345:
Blake is in charge of securing all 20 of his company's servers. He has enabled hardware and software firewalls, hardened the operating systems, and disabled all unnecessary services on all the servers. Unfortunately, there is proprietary AS400 emulation software that must run on one of the servers that requires the telnet service to function properly.
Blake is especially concerned about this since telnet can be a very large security risk in an organization. Blake is concerned about how this particular server might look to an outside attacker so he decides to perform some footprinting, scanning, and penetration tests on the server. Blake telnets into the server using Port 80 and types in the following command: HEAD / HTTP/1.0
After pressing enter twice, Blake gets the following results: What has Blake just accomplished?
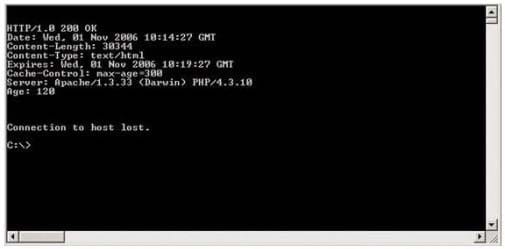
A. Downloaded a file to his local computer
B. Submitted a remote command to crash the server
C. Poisoned the local DNS cache of the server
D. Grabbed the Operating System banner
-
Question 346:
John is the network administrator of XSECURITY systems. His network was recently compromised. He analyzes the log files to investigate the attack. Take a look at the following Linux log file snippet. The hacker compromised and "owned" a Linux machine.
What is the hacker trying to accomplish here?
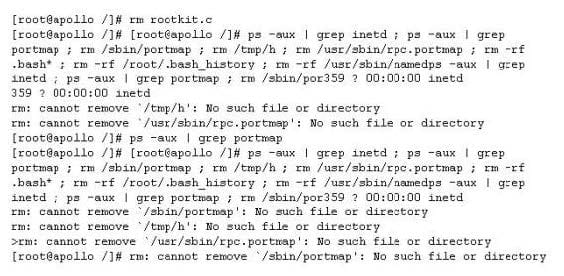
A. The hacker is attempting to compromise more machines on the network
B. The hacker is planting a rootkit
C. The hacker is running a buffer overflow exploit to lock down the system
D. The hacker is trying to cover his tracks
-
Question 347:
You ping a target IP to check if the host is up. You do not get a response. You suspect ICMP is blocked at the firewall. Next you use hping2 tool to ping the target host and you get a response.
Why does the host respond to hping2 and not ping packet?
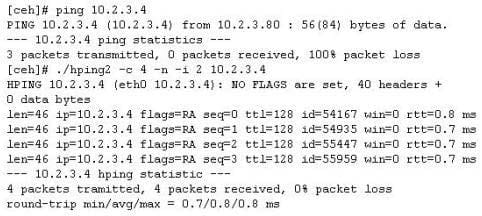
A. Ping packets cannot bypass firewalls
B. You must use ping 10.2.3.4 switch
C. Hping2 uses stealth TCP packets to connect
D. Hping2 uses TCP instead of ICMP by default
-
Question 348:
You are performing a port scan with nmap. You are in hurry and conducting the scans at the fastest possible speed. However, you don't want to sacrifice reliability for speed. If stealth is not an issue, what type of scan should you run to get very reliable results?
A. Stealth scan
B. Connect scan
C. Fragmented packet scan
D. XMAS scan
-
Question 349:
Blane is a security analyst for a law firm. One of the lawyers needs to send out an email to a client but he wants to know if the email is forwarded on to any other recipients. The client is explicitly asked not to resend the email since that would be a violation of the lawyer's and client's agreement for this particular case.
What can Blane use to accomplish this?
A. He can use a split-DNS service to ensure the email is not forwarded on.
B. A service such as HTTrack would accomplish this.
C. Blane could use MetaGoofil tracking tool.
D. Blane can use a service such as ReadNotify tracking tool.
-
Question 350:
Harold just got home from working at Henderson LLC where he works as an IT technician.
He was able to get off early because they were not too busy. When he walks into his home office, he notices his teenage daughter on the computer, apparently chatting with someone online. As soon as she hears Harold enter the room, she closes all her windows and tries to act like she was playing a game. When Harold asks her what she was doing, she acts very nervous and does not give him a straight answer. Harold is very concerned because he does not want his daughter to fall victim to online predators and the sort. Harold doesn't necessarily want to install any programs that will restrict the sites his daughter goes to, because he doesn't want to alert her to his trying to figure out what she is doing. Harold wants to use some kind of program that will track her activities online, and send Harold an email of her activity once a day so he can see what she has been up to.
What kind of software could Harold use to accomplish this?
A. Install hardware Keylogger on her computer
B. Install screen capturing Spyware on her computer
C. Enable Remote Desktop on her computer
D. Install VNC on her computer
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.