Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Apr 15, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 351:
Which of the following represent weak password? (Select 2 answers)
A. Passwords that contain letters,special characters,and numbers ExamplE. ap1$%##f@52
B. Passwords that contain only numbers ExamplE. 23698217
C. Passwords that contain only special characters ExamplE. and*#@!(%)
D. Passwords that contain letters and numbers ExamplE. meerdfget123
E. Passwords that contain only letters ExamplE. QWERTYKLRTY
F. Passwords that contain only special characters and numbers ExamplE. 123@$45
G. Passwords that contain only letters and special characters ExamplE. bob@andba
H. Passwords that contain Uppercase/Lowercase from a dictionary list ExamplE. OrAnGe
-
Question 352:
After a client sends a connection request (SYN) packet to the server, the server will respond (SYN-ACK) with a sequence number of its choosing, which then must be acknowledged (ACK) by the client. This sequence number is predictable; the attack connects to a service first with its own IP address, records the sequence number chosen, and then opens a second connection from a forged IP address. The attack doesn't see the SYN-ACK (or any other packet) from the server, but can guess the correct responses. If the source IP address is used for authentication, then the attacker can use the one-sided communication to break into the server.
What attacks can you successfully launch against a server using the above technique?
A. Denial of Service attacks
B. Session Hijacking attacks
C. Web page defacement attacks
D. IP spoofing attacks
-
Question 353:
Neil is an IT security consultant working on contract for Davidson Avionics. Neil has been hired to audit the network of Davidson Avionics. He has been given permission to perform any tests necessary. Neil has created a fake company ID badge and uniform. Neil waits by one of the company's entrance doors and follows an employee into the office after they use their valid access card to gain entrance.
What type of social engineering attack has Neil employed here?
A. Neil has used a tailgating social engineering attack to gain access to the offices
B. He has used a piggybacking technique to gain unauthorized access
C. This type of social engineering attack is called man trapping
D. Neil is using the technique of reverse social engineering to gain access to the offices of Davidson Avionics
-
Question 354:
You are the security administrator for a large network. You want to prevent attackers from running any sort of traceroute into your DMZ and discovering the internal structure of publicly accessible areas of the network.
How can you achieve this?
A. There is no way to completely block tracerouting into this area
B. Block UDP at the firewall
C. Block TCP at the firewall
D. Block ICMP at the firewall
-
Question 355:
Here is the ASCII Sheet.

You want to guess the DBO username juggyboy (8 characters) using Blind SQL Injection technique. What is the correct syntax?
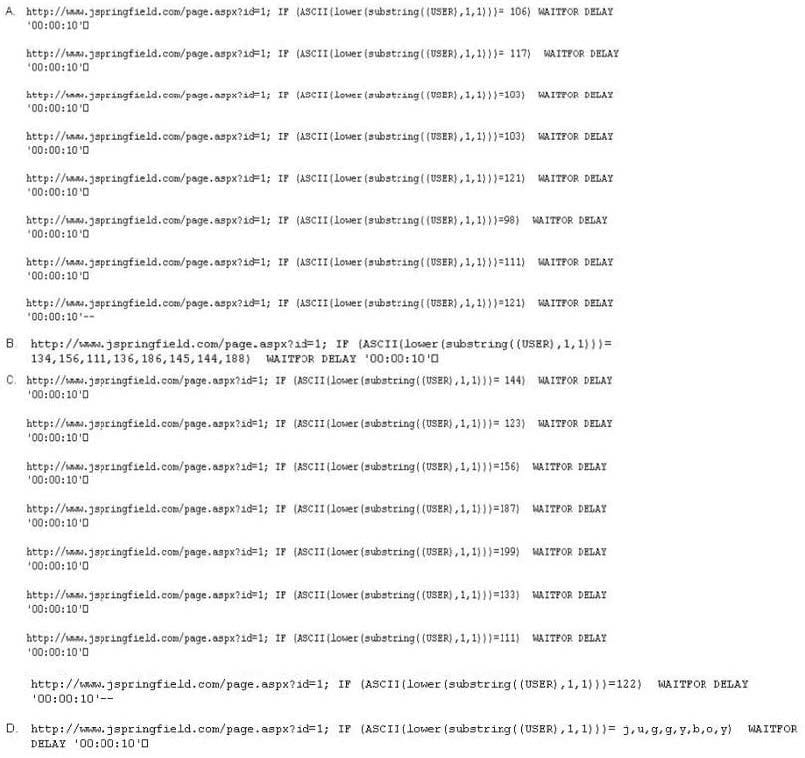
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 356:
How do you defend against ARP Poisoning attack? (Select 2 answers)
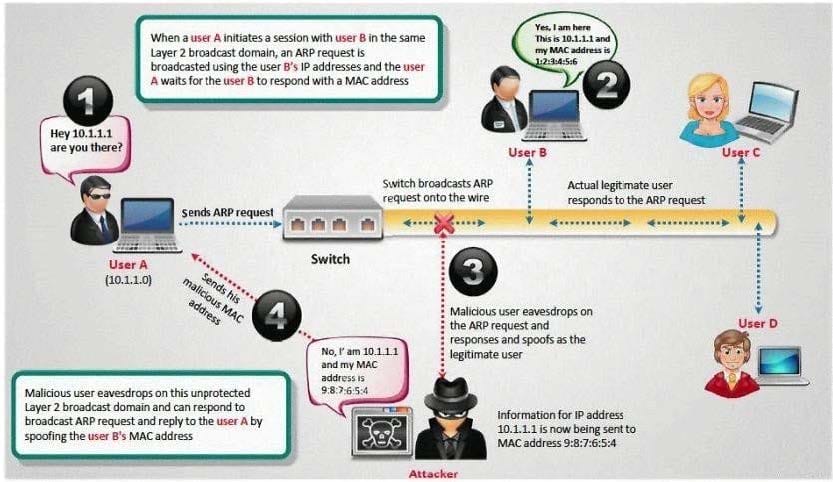
A. Enable DHCP Snooping Binding Table
B. Restrict ARP Duplicates
C. Enable Dynamic ARP Inspection
D. Enable MAC snooping Table
-
Question 357:
What type of port scan is shown below?

A. Idle Scan
B. Windows Scan
C. XMAS Scan
D. SYN Stealth Scan
-
Question 358:
Wayne is the senior security analyst for his company. Wayne is examining some traffic logs on a server and came across some inconsistencies. Wayne finds some IP packets from a computer purporting to be on the internal network. The packets originate from 192.168.12.35 with a TTL of
15. The server replied to this computer and received a response from 192.168.12.35 with a TTL of 21.
What can Wayne infer from this traffic log?
A. The initial traffic from 192.168.12.35 was being spoofed.
B. The traffic from 192.168.12.25 is from a Linux computer.
C. The TTL of 21 means that the client computer is on wireless.
D. The client computer at 192.168.12.35 is a zombie computer.
-
Question 359:
Lauren is performing a network audit for her entire company. The entire network is comprised of around
500 computers. Lauren starts an ICMP ping sweep by sending one IP packet to the broadcast address of
the network, but only receives responses from around five hosts.
Why did this ping sweep only produce a few responses?
A. Only Windows systems will reply to this scan.
B. A switched network will not respond to packets sent to the broadcast address.
C. Only Linux and Unix-like (Non-Windows) systems will reply to this scan.
D. Only servers will reply to this scan.
-
Question 360:
Keystroke logging is the action of tracking (or logging) the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored.
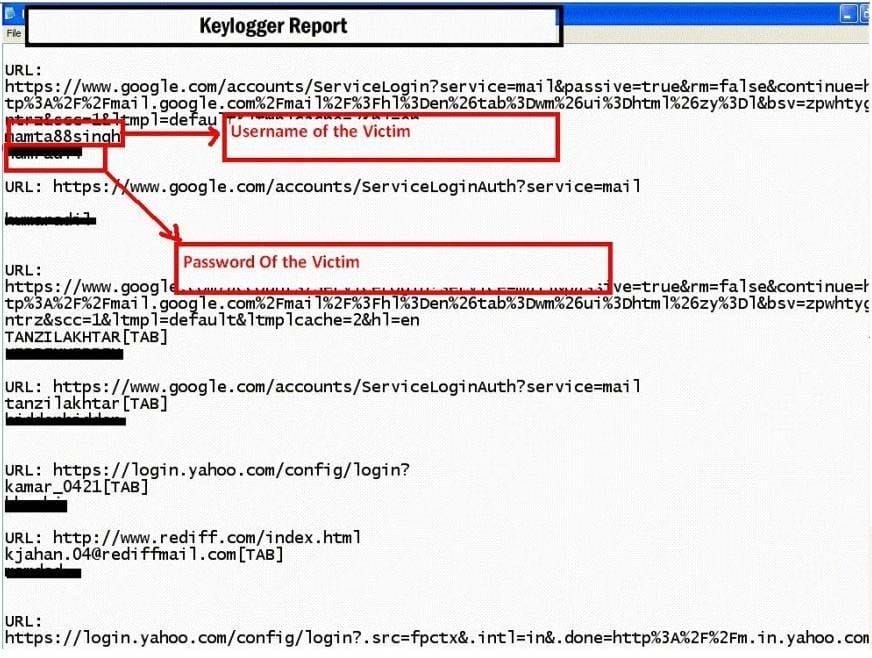
How will you defend against hardware keyloggers when using public computers and Internet Kiosks? (Select 4 answers)
A. Alternate between typing the login credentials and typing characters somewhere else in the focus window
B. Type a wrong password first,later type the correct password on the login page defeating the keylogger recording
C. Type a password beginning with the last letter and then using the mouse to move the cursor for each subsequent letter.
D. The next key typed replaces selected text portion. E.g. if the password is "secret",one could type "s",then some dummy keys "asdfsd". Then these dummies could be selected with mouse,and next character from the password "e" is typed,which replaces the dummies "asdfsd"
E. The next key typed replaces selected text portion. E.g. if the password is "secret",one could type "s",then some dummy keys "asdfsd". Then these dummies could be selected with mouse,and next character from the password "e" is typed,which replaces the dummies "asdfsd"
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.