Exam Details
Exam Code
:350-401Exam Name
:Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)Certification
:CCNP EnterpriseVendor
:CiscoTotal Questions
:1407 Q&AsLast Updated
:Mar 28, 2025
Cisco CCNP Enterprise 350-401 Questions & Answers
-
Question 21:
An engineer is implementing a new SSID on a Cisco Catalyst 9800 Series WLC that must be broadcast on 6 GHz radios. Users will be required to use EAP-TLS to authenticate. Which wireless Layer 2 security method is required?
A. WPA2 Enterprise
B. WPA2 Personal
C. WPA3 Enterprise
D. WPA3 Personal
-
Question 22:
Refer to the exhibit.
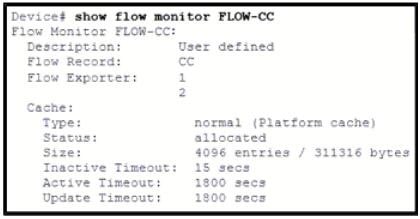
What can be determined from the output?
A. Flow record CC is configured with two separate exporters.
B. Flow record CC is configured with a single exporter.
C. Flow monitor FLOW-CC is configured with two separate flow records to a single exporter.
D. Flow monitor FLOW-CC is configured to two separate exporters.
-
Question 23:

Refer to the exhibit. What is output by this code?
A. -1 -2 -3 -4
B. 8 7 6 5
C. 4 5 6 7
D. -4 -5 -6 -7
-
Question 24:
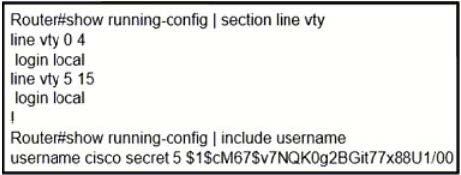
Refer to the exhibit. Which action automatically enables privilege exec mode when logging in via SSH?
A. Configure a password under the line configuration.
B. Configure the enable secret to be the same as the secret for user "Cisco".
C. Configure privilege level 15 under the line configuration.
D. Configure user "cisco" with privilege level 15.
-
Question 25:
Which security actions must be implemented to prevent an API injection attack?
A. Log and monitor failed attempts.
B. Use password hash with biometric authentication.
C. Validate, filter, and sanitize all incoming data.
D. Use short-lived access tokens and authenticate the apps.
-
Question 26:
Refer to the exhibit.
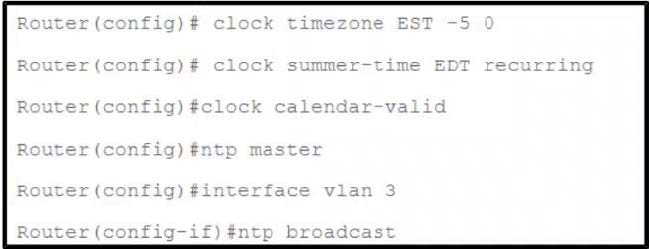
What are two results of the NTP configuration? (Choose two.)
A. It uses other systems as an authoritative time source.
B. It distributes the time via NTP broadcast and multicast packets.
C. It distributes the time via NTP broadcast packets.
D. It forms a peer association with another system.
E. It uses the hardware clock as an authoritative time source.
-
Question 27:
Which feature allows clients to perform Layer 2 roaming between wireless controllers?
A. mobility groups
B. N+1 high availability
C. RF grouping
D. SSO
-
Question 28:
How are control traffic, client authentication and data traffic handled in a mobility express environment?
A. Control traffic and client authentication is handled centrally by the controller. Data traffic is switched centrally by the controller.
B. Control traffic and client authentication is handled centrally by the controller. Data traffic is switched locally by the access points.
C. Control traffic and client authentication is handled locally by each access point. Data traffic is switched locally by the access points.
D. Control traffic and client authentication is handled locally by each access point. Data traffic is switched centrally by the controller.
-
Question 29:
Which Cisco DNA Center Assurance feature verifies host reachability?
A. path trace
B. application experience
C. detail information
D. network time travel
-
Question 30:
Which feature is offered by the Cisco Advanced Malware Protection for Endpoints solution?
A. File Sandboxing
B. NetFlow
C. TrustSec
D. DNS Protection
Related Exams:
300-410
Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)300-415
Implementing Cisco SD-WAN Solutions (ENSDWI)300-420
Designing Cisco Enterprise Networks (ENSLD)300-425
Designing Cisco Enterprise Wireless Networks (ENWLSD)300-430
Implementing Cisco Enterprise Wireless Networks (ENWLSI)300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-440
Designing and Implementing Cloud Connectivity (ENCC)350-401
Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-401 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.