Exam Details
Exam Code
:350-401Exam Name
:Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)Certification
:CCNP EnterpriseVendor
:CiscoTotal Questions
:1407 Q&AsLast Updated
:Apr 13, 2025
Cisco CCNP Enterprise 350-401 Questions & Answers
-
Question 461:
Which method requires a client to authenticate and has the capability to function without encryption?
A. open
B. WEP
C. WebAuth
D. PSK
-
Question 462:
Which action occurs during a Layer 3 roam?
A. The client receives a new IP adcress after authentication occurs.
B. The client is marked as `'foreign" on the original controller.
C. The client database entry is moved from the old controller to the new controller.
D. Client traffic is tunneled back to the original control after a Layer 3 roam occurs.
-
Question 463:
In a Cisco SD-Access network architecture, which access layer cabling design is optimal for the underlay network?
A. Switches are cross-linked at the same layer and have a single connection to each upstream distribution device.
B. Switches are connected to each upstream distribution and core device.
C. Switches are connected to each upstream distribution device.
D. Switches are cross-linked to devices at the same layer and at the upstream and downstream devices.
-
Question 464:
An engineer must use IP SLA to measure the network performance and record statistics hop-by-hop. Which configuration must be used?

A. Option A
B. Option B
C. Option C
D. Option D
-
Question 465:
Which RF value represents the decline of the RF signal amplitude over a given distance?
A. signal-to-noise ration
B. effective isotropic racketed power
C. free space path loss
D. received signal strength indicator
-
Question 466:
Which technology is the Cisco SD-Access control plane based on?
A. LISP
B. CTS
C. SGT
D. VRF
-
Question 467:
How does policy-based routing function?
A. It schedules traffic using classification
B. It is applied to all ingress unicast traffic received on an interlace
C. It is applied to all egress unicast traffic on an interface
D. It controls traffic using embedded event detectors
-
Question 468:
Refer to the exhibit.
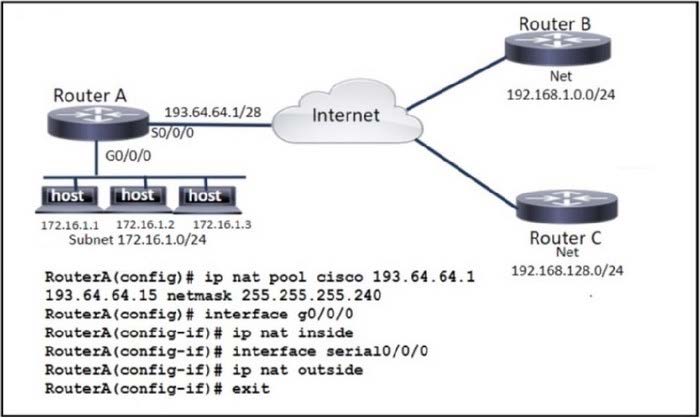
An engineer must configure PAT to provide internet access to all users by using one global address for many local addresses. Which command set completes the configuration?
A. RouterA(config)# ip nat inside source list 1 pool Cisco overload
B. RouterA(config)# ip nat inside source static 172.16.1.1 193.64.64.1
C. RouterA(config)# ip nat inside source static 172.16.1.1 172.16.1.2
D. RouterA(config)# ip nat inside source list 1 pool Cisco
-
Question 469:
Refer to the exhibit.
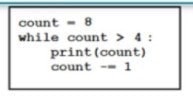
What is output by this code?
A. 8 7 6 5
B. -4 -5 -6 -7
C. -1 -2-3-4
D. 4 5 6 7
-
Question 470:
Refer to the exhibit.
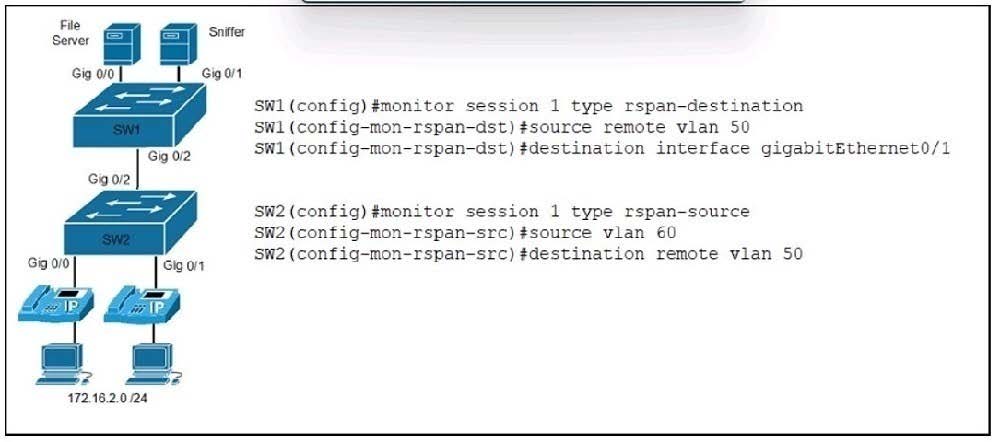
An engineer must send the 172.16.2.0 /24 user traffic to a packet capture tool to troubleshoot an issue. Which action completes the configuration?
A. Encrypt the traffic between the users and the monitoring servers.
B. Disable the spanning tree protocol on the monitoring server VLAN.
C. Enable the Cisco Discovery Protocol on the server interfaces.
D. Define the remote span VLAN on SW1 and SW2.
Related Exams:
300-410
Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)300-415
Implementing Cisco SD-WAN Solutions (ENSDWI)300-420
Designing Cisco Enterprise Networks (ENSLD)300-425
Designing Cisco Enterprise Wireless Networks (ENWLSD)300-430
Implementing Cisco Enterprise Wireless Networks (ENWLSI)300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-440
Designing and Implementing Cloud Connectivity (ENCC)350-401
Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-401 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.