Exam Details
Exam Code
:350-501Exam Name
:Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)Certification
:CCNP Service ProviderVendor
:CiscoTotal Questions
:509 Q&AsLast Updated
:Apr 10, 2025
Cisco CCNP Service Provider 350-501 Questions & Answers
-
Question 161:
A network engineer is testing an automation platform that interacts with Cisco networking devices via NETCONF over SSH. In accordance with internal security requirements:
1.
NETCONF sessions are permitted only from trusted sources in the 172.16.20.0/24 subnet.
2.
CLI SSH access is permitted from any source.
Which configuration must the engineer apply on R1?
A. configure terminalhostname R1 ip domain-name mydomain.comcrypto key generate rsaip ssh version 1access-list 1 permit 172.16.20.0 0.0.0.255netconf ssh acl 1 line vty 0 4transport input sshend
B. configure terminalhostname R1 ip domain-name mydomain.comcrypto key generate rsaip ssh version 2access-list 1 permit 172.16.20.0 0.0.0.255access-list 1 permit anynetconf ssh line vty 0 4access-class 1 in transport input sshend
C. configure terminalhostname R1 ip domain-name mydomain.comcrypto key generate rsaip ssh version 1
access-list 1 permit 172.16.20.0 0.0.0.255
access-list 2 permit any
netconf ssh
line vty 0 4
access-class 2 in
transport input ssh
end
D. configure terminalhostname R1 ip domain-name mydomain.comcrypto key generate rsaip ssh version 2access-list 1 permit 172.16.20.0 0.0.0.255netconf ssh acl 1 line vty 0 4transport input sshend
-
Question 162:
What are two features of stateful NAT64? (Choose two.)
A. It uses address overloading.
B. It provides 1:N translations, so it supports an unlimited number of endpoints.
C. It requires IPv4-translatable IPv6 address assignments.
D. It requires the IPv6 hosts to use either DHCPv6-based address assignments or manual address assignments.
E. It provides 1:1 translation, so it supports a limited number of endpoints.
-
Question 163:
Refer to the exhibit.
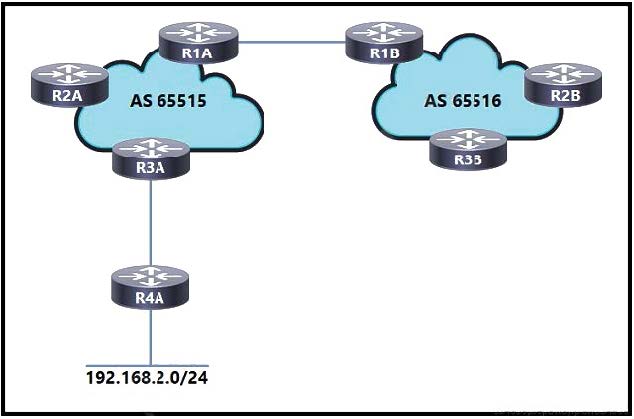
An engineer working for a private telecommunication company with an employee id: 3414:81:713 is implementing this network, in which:
1.
Routers R1A and R1B are eBGP neighbors.
2.
iBGP is configured within AS 65515 and AS 65516.
3.
Network 192.168.2.0/24 is shared with AS 65516.
4.
Router R3A has an iBGP relationship with router R2A only.
5.
Router R2A has an iBGP relationship with routers R1A and R3A.
Which additional task must the engineer perform to complete the configuration?
A. Configure router R2A to use the next-hop-self attribute when advertising the learned route to router R1A.
B. Configure router R3A to redistribute route 192.168.2.0/24 into the configured IGP to advertise the prefix to router R1A.
C. Configure router R2A as a route reflector to advertise the iBGP learned prefix from router R3A to R1A.
D. Configure router R1A with a static route to 192.168.2.0/24 that is redistributed into BGP.
-
Question 164:
Refer to the exhibit.
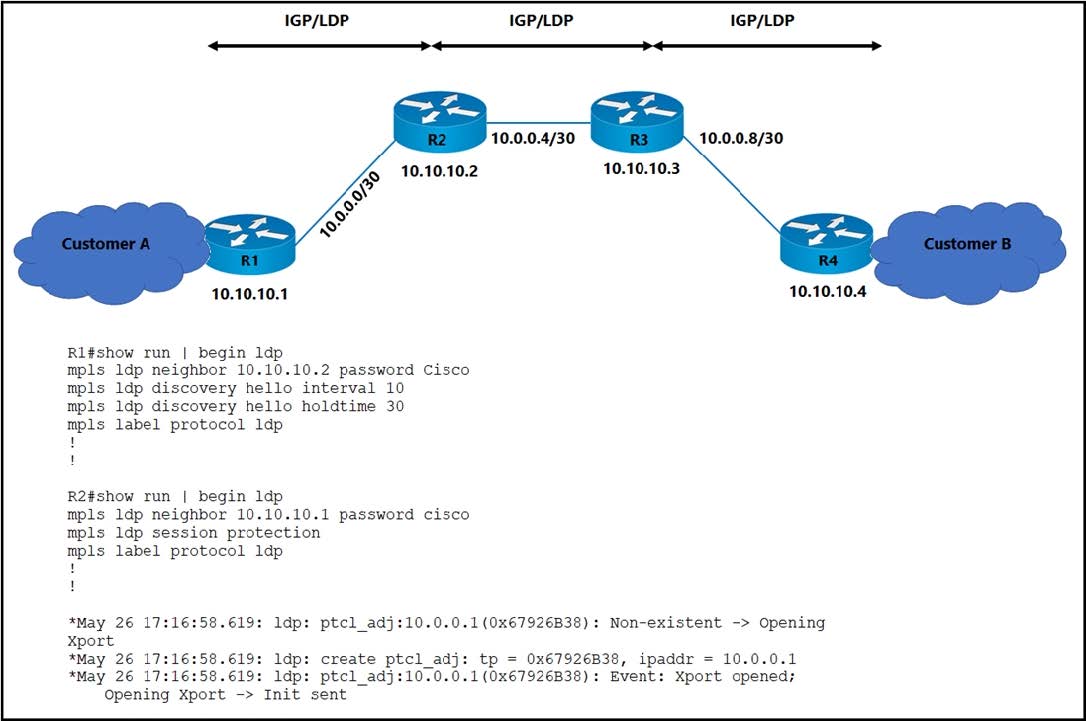
The operations team is implementing an LDP-based configuration in the service provider core network with these requirements:
1.
R1 must establish LDP peering with the loopback IP address as its Router-ID.
2.
Session protection must be enabled on R2.
How must the team update the network configuration to successfully enable LDP peering between R1 and R2?
A. Change the LDP password on R2 to Cisco.
B. Configure mpls ldp router-id loopback0 on R1 and R2.
C. Configure LDP session protection on R1.
D. Change the discover hello hold time and interval to their default values.
-
Question 165:
Refer to the exhibit.
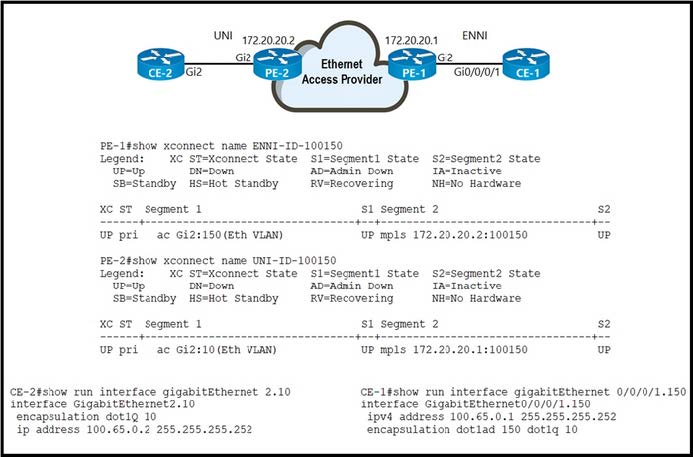
An Ethernet access provider is configuring routers PE-1 and PE-2 to provide E-Access EVPL service between UNI and ENNI. ENNI service multiplexing is based on 802.1ad tag 150, and service-multiplexed UNI is based on 802.1q tag 10. Which EFP configurations must the provider implement on PE-1 and PE-2 to establish end-to-end connectivity between CE-1 and CE-2?
A. On PE-1:
interface GigabitEthernet2
service instance 100 ethernet
encapsulation dot1ad 150
rewrite ingress tag pop 1 symmetric
On PE-2:
interface GigabitEthernet2
service instance 2 ethernet
encapsulation dot1q 10
B. On PE-1:
interface GigabitEthernet2
service instance 100 ethernet
encapsulation dot1q 150
rewrite ingress tag pop 1 symmetric
On PE-2:
interface GigabitEthernet2
service instance 2 ethernet
encapsulation dot1q 10
C. On PE-1:
interface GigabitEthernet2
service instance 100 ethernet
encapsulation dot1ad 150 dot1q 10
rewrite ingress tag pop 2 symmetric
On PE-2:
interface GigabitEthernet2
service instance 2 ethernet
encapsulation dot1q 10
D. On PE-1:
interface GigabitEthernet2
service instance 100 ethernet
encapsulation dot1ad 150
rewrite ingress tag pop 1 symmetric
On PE-2:
interface GigabitEthernet2
service instance 2 ethernet
encapsulation dot1q 10
rewrite ingress tag pop 1 symmetric
-
Question 166:
Refer to the exhibit.
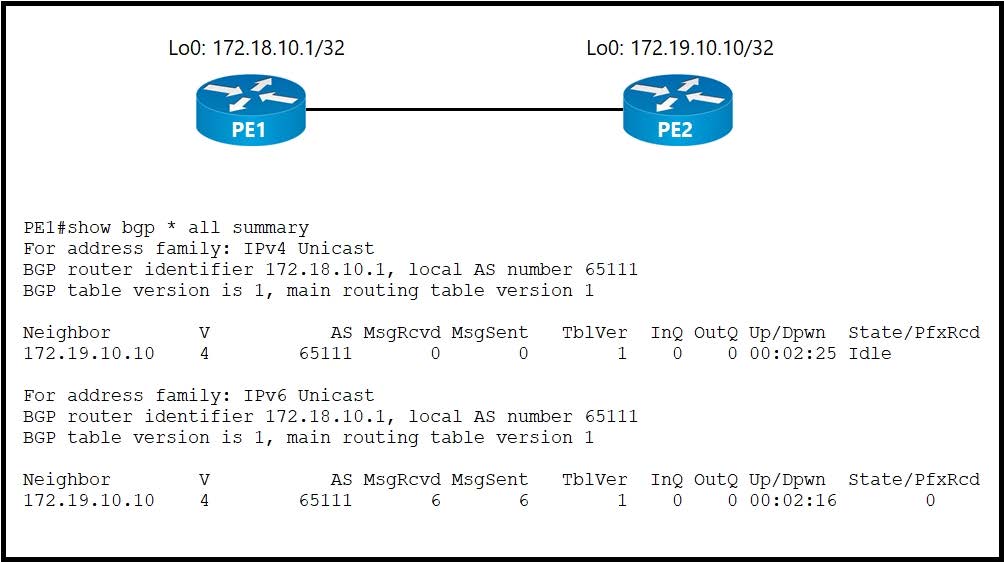
An administrator working for large ISP must connect its two POP sites to provide internet connectivity to its customers. Which configuration must the administrator perform to establish an iBGP session between routers PE1 on POP site 1 and PE2 on POP site 2?
A. PE2#configure terminalPE2(config)#router bgp 65111PE2(config-router)#no neighbor 172.18.10.1 shutdownPE2(config-router)#end
B. PE1#configure terminalPE1(config)#router bgp 65111PE1(config-router)#no neighbor 172.19.10.10 shutdownPE1(config-router)#end
C. PE1#configure terminalPE1(config)#router bgp 65111PE1(config-router)#address-family ipv4 unicastPE1(config-router-af)#neighbor 172.19.10.10 activatePE1(config-router-af)#end
D. PE2#configure terminalPE2(config)#router bgp 65111PE2(config-router)#address-family ipv4 unicastPE2(config-router-af)#neighbor 172.18.10.1 activatePE2(config-router-af)#end
-
Question 167:
Refer to the exhibit.
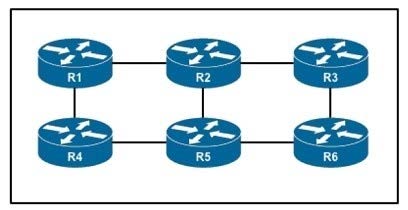
An engineer is configuring an administrative domain in the given multi-vendor environment with PIM-SM. Which feature must the engineer implement so that devices will dynamically learn the RP?
A. Auto-RP
B. BIDIR-PIM
C. SSM
D. BSR
-
Question 168:
Refer to the exhibit.
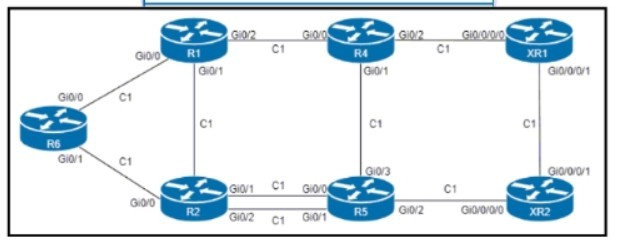
An engineer configured R6 as the headend LSR of an RSVP-TE LSP to router XR2, with the dynamic path signaled as R6-R2-R5-XR2. and set the OSPF cost of all links to 1. MPLS autotunnel backup Is enabled on all routers to protect the LSP.
Which two NNHOP backup tunnels should the engineer use to complete the implementation? (Choose two.)
A. The R6 backup tunnel path R6-R1-R4-R5.
B. The R2 backup tunnel path R2-R5 across the alternate link.
C. The R2 backup tunnel path R2-R1-R4-XR1-XR2.
D. The R6 backup tunnel path R6-R2-R5
E. The R6 backup tunnel path R6-R1-R2.
-
Question 169:
A customer has requested that the service provider use a Cisco MPLS TE tunnel to force the E-line service to take a specific route What is used to send the traffic over the tunnel?
A. static route
B. preferred path
C. forwarding adjacency
D. autoroute destination
-
Question 170:
When Cisco lOS XE REST API uses HTTP request methods what is the purpose of a PUT request?
A. retrieves the specified resource or representation
B. submits data to be processed to the specified resource
C. updates the specified resource with new information
D. creates a new resource
Related Exams:
300-510
Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)300-515
Implementing Cisco Service Provider VPN Services (SVPI)300-535
Automating and Programming Cisco Service Provider Solutions (SPAUTO)350-501
Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-501 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.