Exam Details
Exam Code
:350-701Exam Name
:Implementing and Operating Cisco Security Core Technologies (SCOR)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:753 Q&AsLast Updated
:Mar 27, 2025
Cisco CCNP Security 350-701 Questions & Answers
-
Question 11:
Refer to the exhibit.
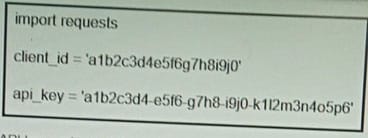
Which command results in these messages when attempting to troubleshoot an IPsec VPN connection?
A. debug crypto isakmp connection
B. debug crypto ipsec
C. debug crypto ipsec endpoint
D. debug crypto isakmp
-
Question 12:
Refer to the exhibit.

An engineer must enable secure SSH protocols and enters this configuration. What are two results of running this set of commands on a Cisco router? (Choose two.)
A. generates RSA key pairs on the router
B. enables SSHv1 on the router
C. uses the FQDN with the label command
D. labels the key pairs to be used for SSH
E. generates AES key pairs on the router
-
Question 13:
A security audit recently revealed that an administrator is using the same password of C1$c0448845217 for his personal account across multiple systems. What must be implemented by the company to reduce the chances of this happening again?
A. centralized user authentication
B. role based access control
C. security awareness training
D. strict password policies
-
Question 14:
Which solution is more secure than the traditional use of a username and password and encompasses at least two of the methods of authentication?
A. RADIUS/LDAP authentication
B. single-sign on
C. Kerberos security solution
D. multifactor authentication
-
Question 15:
Which Cisco Umbrella package supports selective proxy for inspection of traffic from risky domains?
A. DNS Security Advantage
B. SIG Essentials
C. DNS Security Essentials
D. SIG Advantage
-
Question 16:
What are the two distribution methods available to an administrator when performing a fresh rollout of the Cisco AnyConnect Secure Mobility Client? (Choose two.)
A. web deploy
B. SFTP
C. TFTP
D. cloud update
E. predeploy
-
Question 17:
Which Cisco network security device supports contextual awareness?
A. ISE
B. Cisco IOS
C. Cisco ASA
D. Firepower
-
Question 18:
An organization is moving toward the zero-trust model. Which Cisco solution enables administrators to deploy and control microsegmentation of endpoints that are connected to a Cisco Data Center Virtual Edge, Cisco Application Virtual Switch, Microsoft vSwitch, and VMware vSphere Distributed Switch?
A. Cisco Titration
B. Cisco DCNM
C. Cisco Stealthwatch
D. Cisco ACI
-
Question 19:
In which two customer environments is the Cisco WSAv connector traffic direction method selected? (Choose two.)
A. Customer owns ASA Appliance and Virtual Form Factor is required.
B. Customer does not own Cisco hardware and needs Explicit Proxy.
C. Customer owns ASA Appliance and SSL Tunneling is required.
D. Customer needs to support roaming users.
E. Customer does not own Cisco hardware and needs Transparent Redirection (WCCP).
-
Question 20:
Which two VPN tunneling protocols support the use of IPsec to provide data integrity, authentication, and data encryption? (Choose two.)
A. Secure Socket Tunneling Protocol
B. OpenVPN
C. Generic Routing Encapsulation Protocol
D. Layer 2 Tunneling Protocol
E. Point-to-Point Tunneling Protocol
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-701 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.