Exam Details
Exam Code
:350-701Exam Name
:Implementing and Operating Cisco Security Core Technologies (SCOR)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:753 Q&AsLast Updated
:Mar 27, 2025
Cisco CCNP Security 350-701 Questions & Answers
-
Question 31:
Which firewall deployment mode allows inspection of traffic between servers in the same IP subnet?
A. routed
B. multicontext
C. virtual
D. transparent
-
Question 32:
In which two ways does the Cisco Advanced Phishing Protection solution protect users? (Choose two.)
A. It prevents use of compromised accounts and social engineering.
B. It prevents all zero-day attacks coming from the Internet.
C. It automatically removes malicious emails from users' inbox.
D. It prevents trojan horse malware using sensors.
E. It secures all passwords that are shared in video conferences.
-
Question 33:
With regard to RFC 5176 compliance, how many IETF attributes are supported by the RADIUS CoA feature?
A. 3
B. 5
C. 10
D. 12
-
Question 34:
Which action must be taken in the AMP for Endpoints console to detect specific MD5 signatures on endpoints and then quarantine the files?
A. Configure an advanced custom detection list.
B. Configure an IP Block and Allow custom detection list
C. Configure an application custom detection list
D. Configure a simple custom detection list
-
Question 35:
Why should organizations migrate to a multifactor authentication strategy?
A. Multifactor authentication methods of authentication are never compromised
B. Biometrics authentication leads to the need for multifactor authentication due to its ability to be hacked easily
C. Multifactor authentication does not require any piece of evidence for an authentication mechanism
D. Single methods of authentication can be compromised more easily than multifactor authentication
-
Question 36:
Which two capabilities of Integration APIs are utilized with Cisco DNA Center? (Choose two.)
A. Upgrade software on switches and routers
B. Third party reporting
C. Connect to ITSM platforms
D. Create new SSIDs on a wireless LAN controller
E. Automatically deploy new virtual routers
-
Question 37:
Which feature is used in a push model to allow for session identification, host reauthentication, and session termination?
A. AAA attributes
B. CoA request
C. AV pair
D. carrier-grade NAT
-
Question 38:
An organization is implementing AAA for their users. They need to ensure that authorization is verified for every command that is being entered by the network administrator. Which protocol must be configured in order to provide this capability?
A. EAPOL
B. SSH
C. RADIUS
D. TACACS+
-
Question 39:
Which two configurations must be made on Cisco ISE and on Cisco TrustSec devices to force a session to be adjusted after a policy change is made? (Choose two)
A. posture assessment
B. aaa authorization exec default local
C. tacacs-server host 10.1.1.250 key password
D. aaa server radius dynamic-author
E. CoA
-
Question 40:
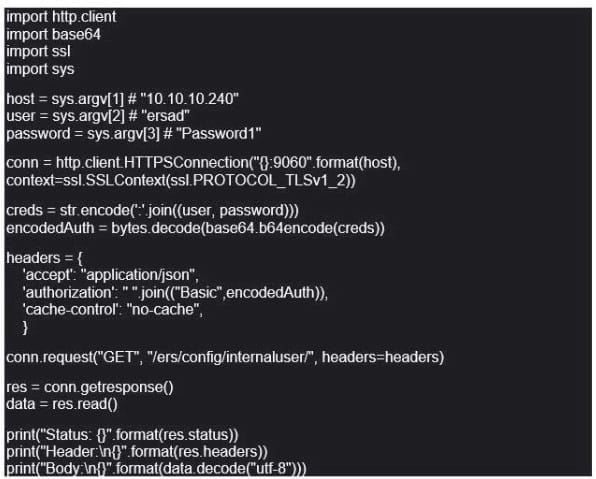
Refer to the exhibit When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZjnside zone once the configuration is deployed?
A. All traffic from any zone to the DMZ_inside zone will be permitted with no further inspection
B. No traffic will be allowed through to the DMZ_inside zone regardless of if it's trusted or not
C. All traffic from any zone will be allowed to the DMZ_inside zone only after inspection
D. No traffic will be allowed through to the DMZ_inside zone unless it's already trusted
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-701 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.