Exam Details
Exam Code
:350-701Exam Name
:Implementing and Operating Cisco Security Core Technologies (SCOR)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:753 Q&AsLast Updated
:Apr 12, 2025
Cisco CCNP Security 350-701 Questions & Answers
-
Question 241:
Which Cisco security solution stops exfiltration using HTTPS?
A. Cisco FTD
B. Cisco AnyConnect
C. Cisco CTA
D. Cisco ASA
-
Question 242:
A network engineer must migrate a Cisco WSA virtual appliance from one physical host to another physical host by using VMware vMotion. What is a requirement for both physical hosts?
A. The hosts must run Cisco AsyncOS 10.0 or greater.
B. The hosts must run different versions of Cisco AsyncOS.
C. The hosts must have access to the same defined network.
D. The hosts must use a different datastore than the virtual appliance.
-
Question 243:
What is a characteristic of an EDR solution and not of an EPP solution?
A. stops all ransomware attacks
B. retrospective analysis
C. decrypts SSL traffic for better visibility
D. performs signature-based detection
-
Question 244:
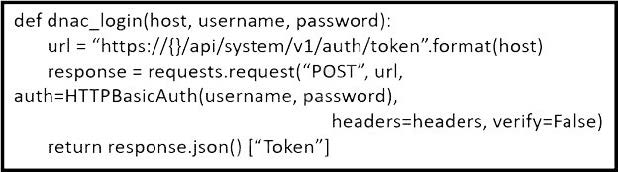
Refer to the exhibit. What is the result of the Python script?
A. It uses the POST HTTP method to obtain a username and password to be used for authentication.
B. It uses the POST HTTP method to obtain a token to be used for authentication.
C. It uses the GET HTTP method to obtain a token to be used for authentication.
D. It uses the GET HTTP method to obtain a username and password to be used for authentication
-
Question 245:
Which configuration method provides the options to prevent physical and virtual endpoint devices that are in the same base EPG or uSeg from being able to communicate with each other with Vmware VDS or Microsoft vSwitch?
A. inter-EPG isolation
B. inter-VLAN security
C. intra-EPG isolation
D. placement in separate EPGs
-
Question 246:
Which system facilitates deploying microsegmentation and multi-tenancy services with a policy-based container?
A. SDLC
B. Docker
C. Lambda
D. Contiv
-
Question 247:
Which API method and required attribute are used to add a device into DNAC with the native API?
A. lastSyncTime and pid
B. POST and name
C. userSudiSerialNos and devicelnfo
D. GET and serialNumber
-
Question 248:
Which Cisco solution integrates Encrypted Traffic Analytics to perform enhanced visibility,promote compliance,shorten response times, and provide administrators with the information needed to provide educated and automated decisions to secure the environment?
A. Cisco DNA Center
B. Cisco SDN
C. Cisco ISE
D. Cisco Security Compiance Solution
-
Question 249:
An organization wants to secure data in a cloud environment. Its security model requires that all users be authenticated and authorized. Security configuration and posture must be continuously validated before access is granted or maintained to applications and data. There is also a need to allow certain application traffic and deny all other traffic by default. Which technology must be used to implement these requirements?
A. Virtual routing and forwarding
B. Microsegmentation
C. Access control policy
D. Virtual LAN
-
Question 250:
What is a benefit of using Cisco Umbrella?
A. DNS queries are resolved faster.
B. Attacks can be mitigated before the application connection occurs.
C. Files are scanned for viruses before they are allowed to run.
D. It prevents malicious inbound traffic.
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-701 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.