Exam Details
Exam Code
:350-701Exam Name
:Implementing and Operating Cisco Security Core Technologies (SCOR)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:753 Q&AsLast Updated
:Apr 12, 2025
Cisco CCNP Security 350-701 Questions & Answers
-
Question 321:
Refer to the exhibit.
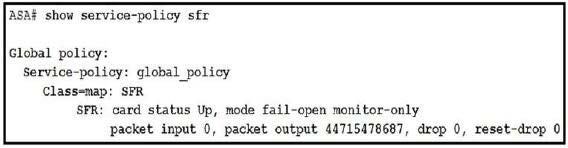
What are two indications of the Cisco Firepower Services Module configuration? (Choose two.)
A. The module is operating in IDS mode.
B. The module fails to receive redirected traffic
C. Traffic is blocked if the module fails.
D. Traffic continues to flow if the module fails.
E. The module is operating in IPS mode.
-
Question 322:
Which benefit does DMVPN provide over GETVPN?
A. DMVPN supports QoS, multicast, and routing, and GETVPN supports only QoS.
B. DMVPN is a tunnel-less VPN, and GETVPN is tunnel-based.
C. DMVPN supports non-IP protocols, and GETVPN supports only IP protocols.
D. DMVPN can be used over the public Internet, and GETVPN requires a private network.
-
Question 323:
Which two actions does the Cisco identity Services Engine posture module provide that ensures endpoint security?(Choose two.)
A. The latest antivirus updates are applied before access is allowed.
B. Assignments to endpoint groups are made dynamically, based on endpoint attributes.
C. Patch management remediation is performed.
D. A centralized management solution is deployed.
E. Endpoint supplicant configuration is deployed.
-
Question 324:
Refer to the exhibit.
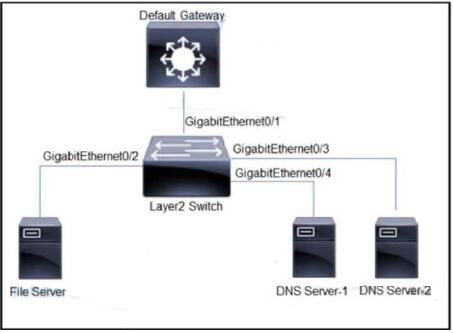
All servers are in the same VLAN/Subnet. DNS Server-1 and DNS Server-2 must communicate with each other, and all servers must communicate with default gateway multilayer switch. Which type of private VLAN ports should be configured to prevent communication between DNS servers and the file server?
A. Configure GigabitEthernet0/1 as community port, GigabitEthernet0/2 as isolated port, and GigabitEthernet0/3 and GigabitEthernet0/4 as promiscuous ports.
B. Configure GigabitEthernet0/1 as community port, GigabitEthernet0/2 as promiscuous port, Gigabit Ethernet0/3 and GigabitEthernet0/4 as isolated ports.
C. Configure GigabitEthernet0/1 as promiscuous port, GigabitEthernet0/2 as isolated port and GigabitEthernet0/3 and GrgabitEthernet0/4 as community ports
D. Configure GigabitEthernet0/1 as promiscuous port, GigabitEthernet0/2 as community port, and GigabitEthernet0/3 and GrgabitEthernet0/4 as isolated ports.
-
Question 325:
A company discovered an attack propagating through their network via a file. A custom file policy was created in order to track this in the future and ensure no other endpoints execute the infected file. In addition, it was discovered during testing that the scans are not detecting the file as an indicator of compromise. What must be done in order to ensure that the created is functioning as it should?
A. Create an IP block list for the website from which the file was downloaded
B. Block the application that the file was using to open
C. Upload the hash for the file into the policy
D. Send the file to Cisco Threat Grid for dynamic analysis
-
Question 326:
Which method of attack is used by a hacker to send malicious code through a web application to an unsuspecting user to request that the victim's web browser executes the code?
A. buffer overflow
B. browser WGET
C. SQL injection
D. cross-site scripting
-
Question 327:
Refer to the exhibit.
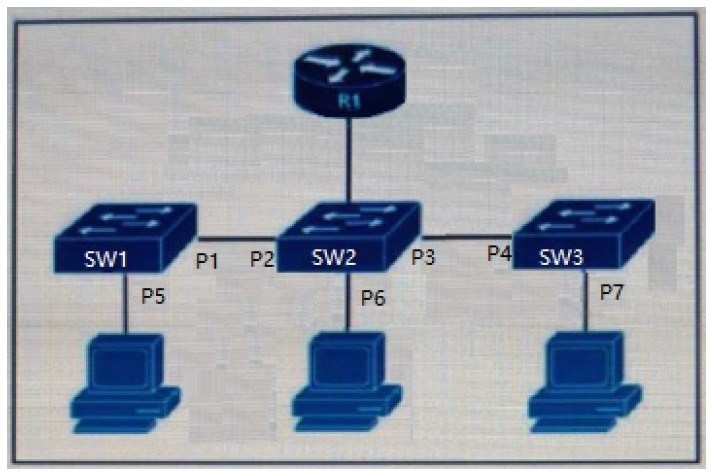
The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
A. P2 and P3 only
B. P5, P6, and P7 only
C. P1, P2, P3, and P4 only
D. P2, P3, and P6 only
-
Question 328:
Which type of data exfiltration technique encodes data in outbound DNS requests to specific servers and can be stopped by Cisco Umbrella?
A. DNS tunneling
B. DNS flood attack
C. cache poisoning
D. DNS hijacking
-
Question 329:
An engineer is configuring device-hardening on a router in order to prevent credentials from being seen if the router configuration was compromised. Which command should be used?
A. service password-encryption
B. username
privilege 15 password C. service password-recovery
D. username < username> password
-
Question 330:
Which two capabilities of Integration APIs are utilized with Cisco DNA center? (Choose two)
A. Automatically deploy new virtual routers
B. Upgrade software on switches and routers
C. Application monitors for power utilization of devices and IoT sensors
D. Connect to Information Technology Service Management Platforms
E. Create new SSIDs on a wireless LAN controller
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-701 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.