Exam Details
Exam Code
:350-701Exam Name
:Implementing and Operating Cisco Security Core Technologies (SCOR)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:753 Q&AsLast Updated
:Apr 12, 2025
Cisco CCNP Security 350-701 Questions & Answers
-
Question 471:
Which cloud service model offers an environment for cloud consumers to develop and deploy applications without needing to manage or maintain the underlying cloud infrastructure?
A. PaaS
B. XaaS
C. IaaS
D. SaaS
-
Question 472:
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
A. Enable IP Layer enforcement.
B. Activate the Advanced Malware Protection license
C. Activate SSL decryption.
D. Enable Intelligent Proxy.
-
Question 473:
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal?
A. Port Bounce
B. CoA Terminate
C. CoA Reauth
D. CoA Session Query
-
Question 474:
Which ASA deployment mode can provide separation of management on a shared appliance?
A. DMZ multiple zone mode
B. transparent firewall mode
C. multiple context mode
D. routed mode
-
Question 475:
Refer to the exhibit.
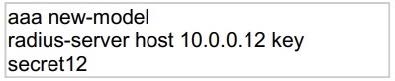
Which statement about the authentication protocol used in the configuration is true?
A. The authentication request contains only a password
B. The authentication request contains only a username
C. The authentication and authorization requests are grouped in a single packet
D. There are separate authentication and authorization request packets
-
Question 476:
Which information is required when adding a device to Firepower Management Center?
A. username and password
B. encryption method
C. device serial number
D. registration key
-
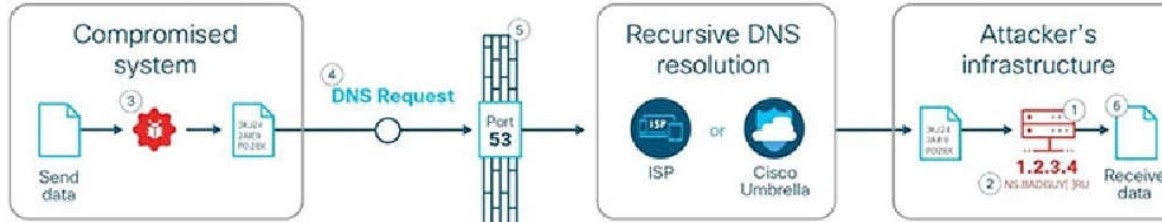
Question 477:
How is DNS tunneling used to exfiltrate data out of a corporate network?
A. It corrupts DNS servers by replacing the actual IP address with a rogue address to collect information or start other attacks.
B. It encodes the payload with random characters that are broken into short strings and the DNS server rebuilds the exfiltrated data.
C. It redirects DNS requests to a malicious server used to steal user credentials, which allows further damage and theft on the network.
D. It leverages the DNS server by permitting recursive lookups to spread the attack to other DNS servers.
-
Question 478:
Where are individual sites specified to be blacklisted in Cisco Umbrella?
A. application settings
B. content categories
C. security settings
D. destination lists
-
Question 479:
Which two are valid suppression types on a Cisco Next Generation Intrusion Prevention System? (Choose two)
A. Port
B. Rule
C. Source
D. Application
E. Protocol
-
Question 480:
Which VPN technology can support a multivendor environment and secure traffic between sites?
A. SSL VPN
B. GET VPN
C. FlexVPN
D. DMVPN
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-701 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.