Exam Details
Exam Code
:350-701Exam Name
:Implementing and Operating Cisco Security Core Technologies (SCOR)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:753 Q&AsLast Updated
:Apr 04, 2025
Cisco CCNP Security 350-701 Questions & Answers
-
Question 581:
Which technology reduces data loss by identifying sensitive information stored in public computing environments?
A. Cisco SDA
B. Cisco Firepower
C. Cisco HyperFlex
D. Cisco Cloudlock
-
Question 582:
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware? (Choose two)
A. Sophos engine
B. white list
C. RAT
D. outbreak filters
E. DLP
-
Question 583:
In which two ways does a system administrator send web traffic transparently to the Web Security Appliance? (Choose two)
A. configure Active Directory Group Policies to push proxy settings
B. configure policy-based routing on the network infrastructure
C. reference a Proxy Auto Config file
D. configure the proxy IP address in the web-browser settings
E. use Web Cache Communication Protocol
-
Question 584:
Refer to the exhibit.
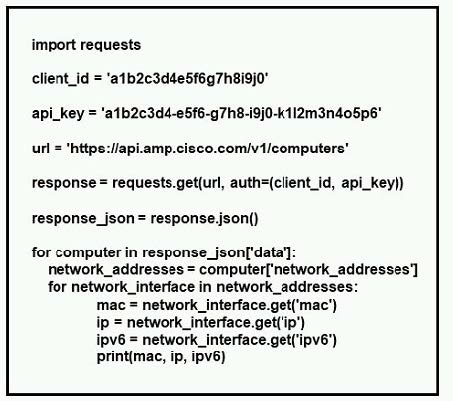
What does the API do when connected to a Cisco security appliance?
A. get the process and PID information from the computers in the network
B. create an SNMP pull mechanism for managing AMP
C. gather network telemetry information from AMP for endpoints
D. gather the network interface information about the computers AMP sees
-
Question 585:
Which two statements about a Cisco WSA configured in Transparent mode are true? (Choose two)
A. It can handle explicit HTTP requests.
B. It requires a PAC file for the client web browser.
C. It requires a proxy for the client web browser.
D. WCCP v2-enabled devices can automatically redirect traffic destined to port 80.
E. Layer 4 switches can automatically redirect traffic destined to port 80.
-
Question 586:
Which two key and block sizes are valid for AES? (Choose two)
A. 64-bit block size, 112-bit key length
B. 64-bit block size, 168-bit key length
C. 128-bit block size, 192-bit key length
D. 128-bit block size, 256-bit key length
E. 192-bit block size, 256-bit key length
-
Question 587:
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two)
A. Patch for cross-site scripting.
B. Perform backups to the private cloud.
C. Protect against input validation and character escapes in the endpoint.
D. Install a spam and virus email filter.
E. Protect systems with an up-to-date antimalware program
-
Question 588:
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
A. transparent
B. redirection
C. forward
D. proxy gateway
-
Question 589:
Which function is the primary function of Cisco AMP threat Grid?
A. automated email encryption
B. applying a real-time URI blacklist
C. automated malware analysis
D. monitoring network traffic
-
Question 590:
Which two probes are configured to gather attributes of connected endpoints using Cisco Identity Services Engine? (Choose two)
A. RADIUS
B. TACACS+
C. DHCP
D. sFlow
E. SMTP
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-701 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.