Exam Details
Exam Code
:350-901Exam Name
:Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)Certification
:Cisco Certified DevNet ProfessionalVendor
:CiscoTotal Questions
:414 Q&AsLast Updated
:Apr 14, 2025
Cisco Cisco Certified DevNet Professional 350-901 Questions & Answers
-
Question 131:
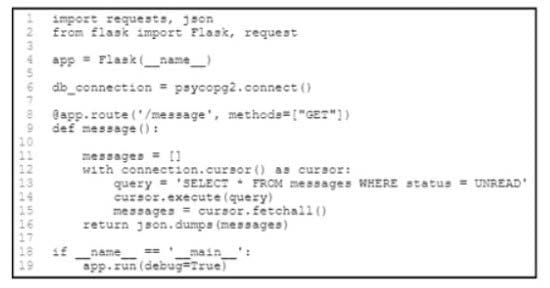
Refer to the exhibit. A Python API server has been deployed. Based on metrics and logs, increased load has been noticed. Which two approaches must be taken to optimize API usage on the server? (Choose two.)
A. Include the ETag header in the API response
B. Include the Last-Modified header in the API response.
C. Change the query to be more efficient.
D. Include the Content-Type header in the API response.
E. Leverage middleware caching and respond with HTTP code 204 in the API response.
-
Question 132:
What is a risk to data privacy during the storage and transmission of data?
A. The risk of exposure is increased when data is shared between applications.
B. The transfer of unencrypted data between storage devices increases the risk of exposure.
C. Data breaches cause ongoing exposure of personal information.
D. The transfer of unencrypted personally identifiable financial information from a storage device increases the risk of a data broach.
-
Question 133:
Which configuration stop must be performed on a Cisco IOS XE device to present collected data in Cisco DNA Center?
A. Create an SNMPv3 user account.
B. Apply a telemetry profile.
C. Synchronize the device and the data collector.
D. Enable Cisco NetFlow collection.
-
Question 134:
Refer to the exhibit.
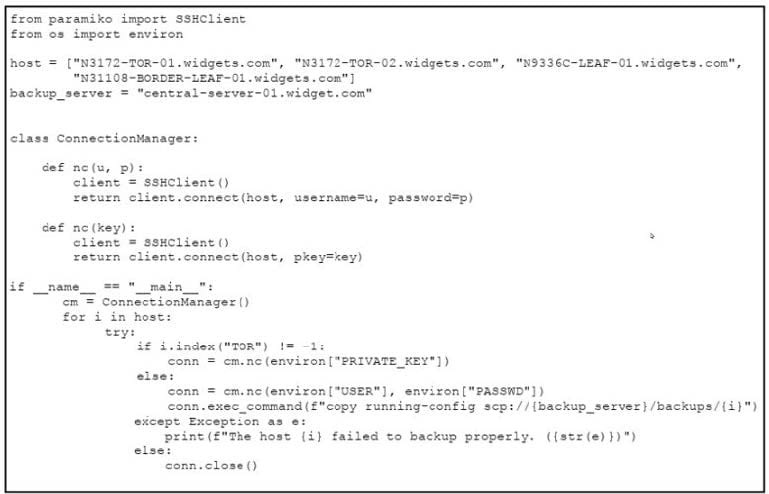
A developer must review an intern's code for a script they wrote to automate backups to the storage server. The script must connect to the network device and copy the running- config to the server.
When considering maintainability, which two changes must be made to the code? (Choose two.)
A. Rename the class to "ArchiveManager".
B. The code is incorrect because the class does not have an__init__() method.
C. The command sent to the network device is incorrect.
D. Refactor the code placing the "for" loop steps inside a single nc method.
E. The intern must use IP addresses because DNS is unreliable.
-
Question 135:
Refer to the exhibit.
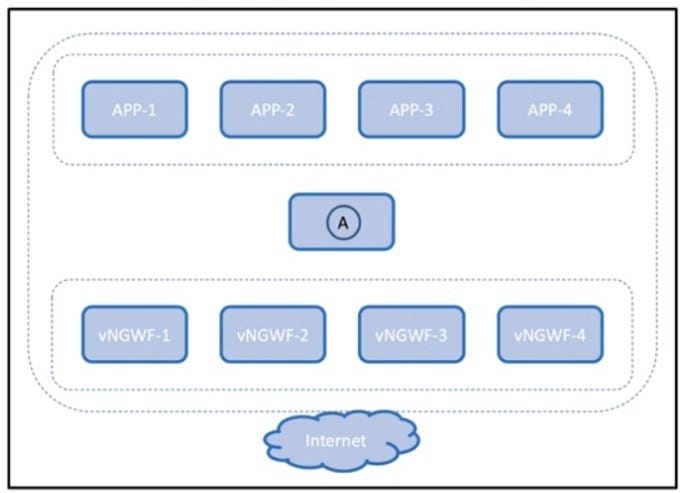
The virtual next-generation firewalls running in the public cloud must be scaled out to meet the throughput requirements of the application layer. Which component is deployed to location A in the diagram?
A. frontend caching server
B. forward proxy
C. backend database
D. internal load balancer
-
Question 136:
An application must be able to print the values of the variables in specific modules. Different message levels will be used for production and for development. Proof of access and activity must be documented. What must be included in the implementation to support these observability requirements?
A. print
B. metrics
C. logging
D. streaming
-
Question 137:
A development team is looking for a tool to automate configurations across the infrastructure. The tool must have these characteristics:
written in Python define playbooks (or intent stateless imperative
Which tool meets these requirements?
A. Puppet
B. Netmiko
C. Ansible
D. NCM
-
Question 138:
Refer to the exhibit.
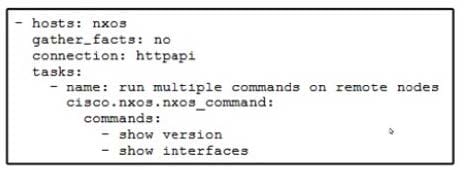
A network administrator copies SSL certificates to a Cisco NX-OS switch. An Ansible playbook is created to enable NX-API, which will use the new certificate. In the group_vars/vars.yml file, which code snippet must be used to define the properly formatted variables?
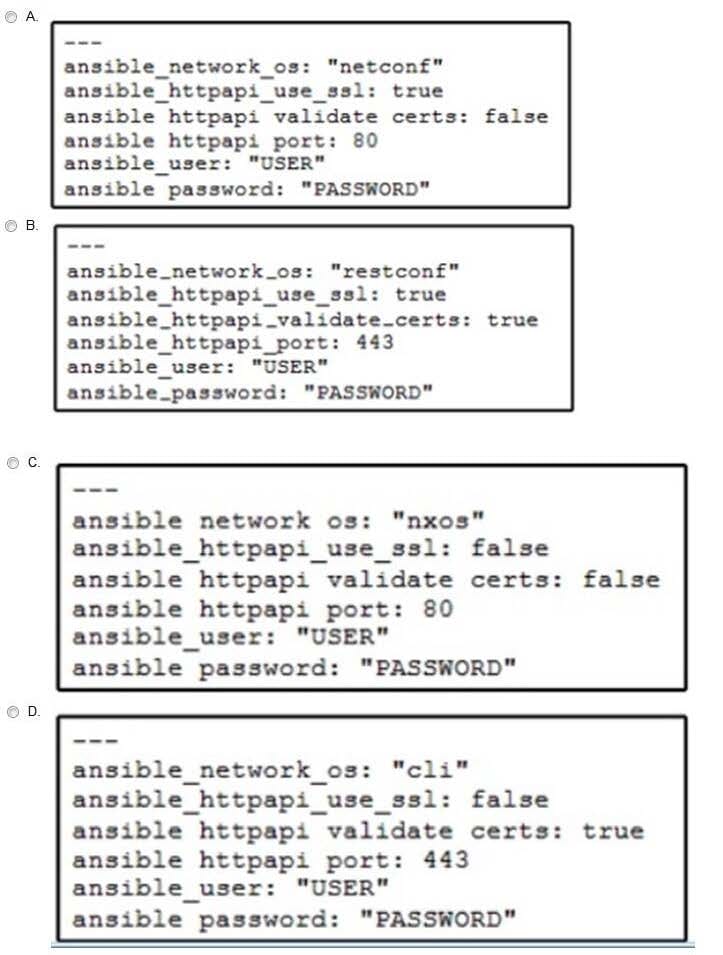
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 139:
Refer to the exhibit.
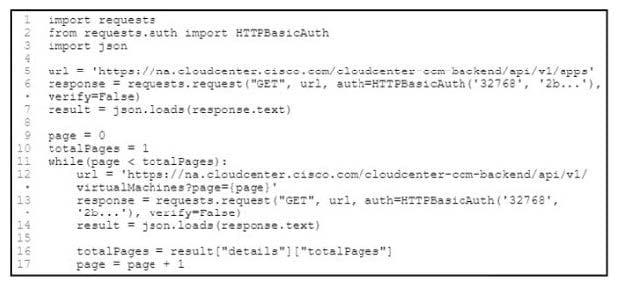
An application has been created to serve a whole enterprise. Based on use and department requirements, changes are requested on a quarterly basis. When evaluating the application design, which two actions improve code maintainability?
A. Replace the requests library with the http client library in the code.
B. Place all import statements on a single line at the top of the code.
C. Cache responses to API calls for later reuse on other code.
D. Parameterize similar code blocks inside functions and reuse within the code.
E. Add comments in appropriate locations to aid in understanding the code.
-
Question 140:
Refer to the exhibit.
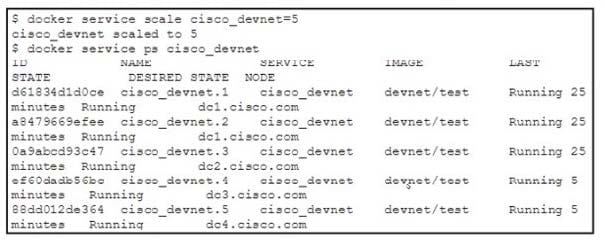
A developer runs the docker service scale command to increase the number of replicas for the cisco_devnet service. The swarm cluster is using a private IP address subnet. The service has these design requirements:
It must be hosted behind a virtual IP address that is reachable from the Internet. For security reasons, the Docker swarm cluster subnet must not be reachable from the Internet.
Which design approach is used to fulfill the requirements?
A. Create an overlay network by using a globally roulable subnet and enable a routing mesh within the swarm cluster.
B. Create a bridge network by using a globally routable subnet and enable a routing mesh within the swarm cluster.
C. Configure an external load balancer to route requests to the swarm service by using VPN.
D. Configure an external load balancer to route requests to the swarm service by using NAT.
Related Exams:
300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-535
Automating and Programming Cisco Service Provider Solutions (SPAUTO)300-635
Automating and Programming Cisco Data Center Solutions (DCAUTO)300-735
Automating and Programming Cisco Security Solutions (SAUTO)300-835
Automating Cisco Collaboration Solutions (CLAUTO)300-910
Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)350-901
Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-901 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.