Exam Details
Exam Code
:350-901Exam Name
:Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)Certification
:Cisco Certified DevNet ProfessionalVendor
:CiscoTotal Questions
:414 Q&AsLast Updated
:Apr 14, 2025
Cisco Cisco Certified DevNet Professional 350-901 Questions & Answers
-
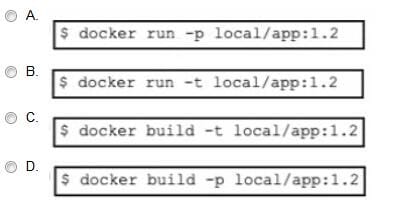
Question 161:
A developer needs to build a new Docker image and has created a tag by using the command:
$ docker tag 32df423320458 local/app.1.2
Which command must be executed next to build the Docker image using the tag?
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 162:
A developer creates an application for a Cisco Catalyst 9000 switch in a Docker container. Which action must be taken to host the application on the switch?
A. Copy the application code to a NETCONF file and upload the file to the switch
B. Connect the switch to Cisco DNA Center and push the application through the platform.
C. Use the Cisco IOxClient tool to export the application to a ZIP file and push the file to the switch
D. Export the application as a TAR file and import the file to the switch
-
Question 163:
A developer is working in a branch to develop a new feature named `newfeat404880077'. A file named `devcoreg13642911.jpg' has accidentally been staged. This needs to be removed so that the commit is performed and branches merged. Which git command must be used to unstage the file?
A. git delete HEAD devcoreg13642911.jpg
B. git remove HEAD devcoreg13642911.jpg
C. git reset HEAD devcoreg13642911.jpg
D. git revert HEAD devcoreg13642911.jpg
-
Question 164:
Which scenario is an example of the pseudonymization of sensitive data that meets GDPR requirements?
A. encrypting sensitive data at rest by using native cloud services and data in transit by using SSL/TLS transport
B. implementing XFowarded For at the frontend of a web app to enable the source IP addresses of headers to change
C. leveraging an application load balancer at the frontend of a web app for SSL/TLS decryption to inspect data in transit
D. separating the sensitive data into its own dedicated secured data store and using tokens in its place
-
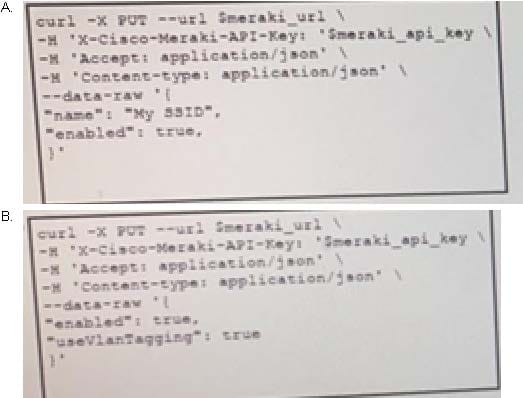
Question 165:
The Meraki API URL https://api.meraki.com/api/v0/networks/123456789/ssids/2 has been stored in the environment variable meraki_url and the API key has been stored in meraki_api_key. Which snippet presents the API call to configure, secure and enable an SSID using the Meraki API?
A. B.

C. D.
-
Question 166:
Refer to the exhibit.
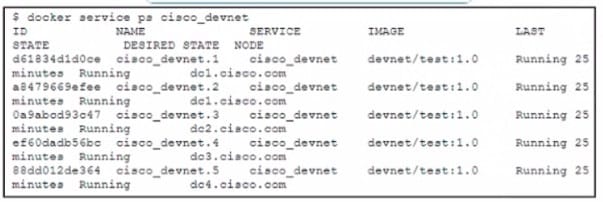
The cisco_devnet Docker swarm service runs across five replicas The development team tags and imports a new image named devnet'test 1 1 and requests that the image be upgraded on each container There must be no service outages
during the upgrade process.
Which two design approaches must be used? (Choose two.)
A. Implement rolling upgrades by using the docker service update command.
B. Enable parallel upgrades by using the docker service update command.
C. Ensure that the service is hosted behind a VIP with no session persistence.
D. Update the restart policy of the containers to restart upon failure.
E. Ensure that the service replicas are set to a minimum of 5.
-
Question 167:
What is a characteristic of event-driven architecture?
A. separates the models for the reading and writing of data
B. allows for loose coupling between software components
C. breaks a solution into parts according to business capability
D. provides a single point of reference for mastering data
-
Question 168:
Which command is used 10 enable application hosting on a Cisco IOS XE device?
A. iox
B. iox-service
C. application -honing
D. app- hosting
-
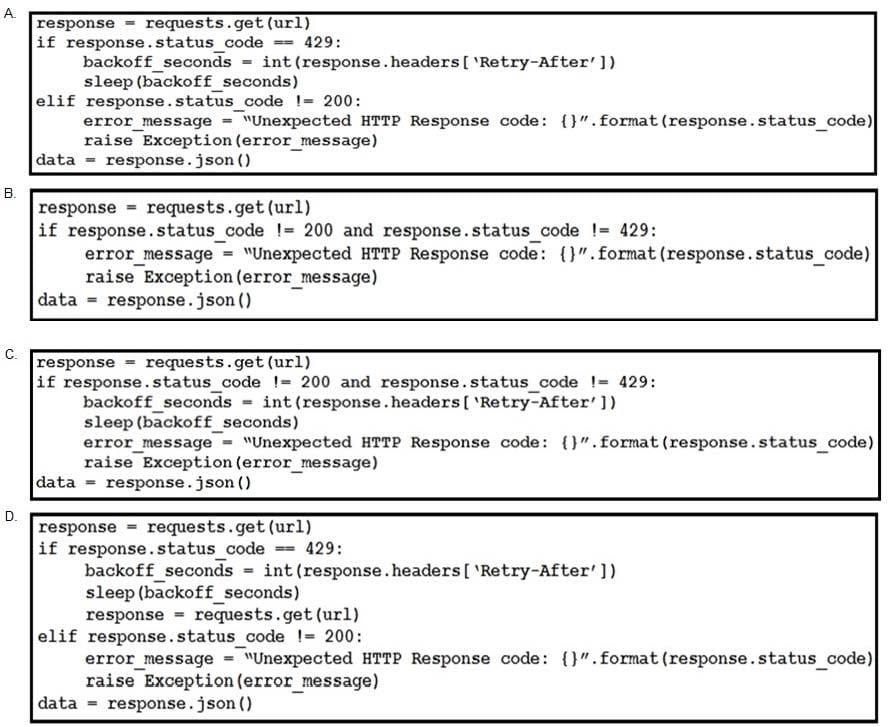
Question 169:
Refer to the exhibit.

This snippet of a script has recently started exiting abnormally with an exception stating "Unexpected HTTP Response code: 429". Which solution handles rate limiting by the remote API?
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 170:
While developing an application following the 12-factor app methodology, which approach should be used in the application for logging?
A. Write a log to a file in the application directory.
B. Write a log to a file in /var/log.
C. Write the logs buffered to stdout.
D. Write the logs unbuffered to stdout.
Related Exams:
300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-535
Automating and Programming Cisco Service Provider Solutions (SPAUTO)300-635
Automating and Programming Cisco Data Center Solutions (DCAUTO)300-735
Automating and Programming Cisco Security Solutions (SAUTO)300-835
Automating Cisco Collaboration Solutions (CLAUTO)300-910
Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)350-901
Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-901 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.