Exam Details
Exam Code
:350-901Exam Name
:Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)Certification
:Cisco Certified DevNet ProfessionalVendor
:CiscoTotal Questions
:414 Q&AsLast Updated
:Mar 29, 2025
Cisco Cisco Certified DevNet Professional 350-901 Questions & Answers
-
Question 291:
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?
A. Embed them directly in the code.
B. Store them in a hidden file.
C. Store them inside the source tree of the application.
D. Change them periodically.
-
Question 292:
Refer to the exhibit , The command docker build -tag=friendlyhello . is run to build a docker image from the given Dockerfile, requirements,txt, and app.py, Then the command docker run -p 4000:80 friendlyhello is executed to run the
application.
Which URL is entered in the web browser to see the content served by the application?
A. http://localhost:4000
B. http ://localhost:80
C. http ://127.0.0.1:80
D. http:///4000:80
-
Question 293:
Which security approach should be used for developing a REST API?
A. Use custom security relevant HTTP response codes
B. Utilise TLS for end to end encryption
C. Add an API key to each URL string
D. Utilize CORS headers
-
Question 294:
Refer to the exhibit.

A. B. C. D.
-
Question 295:
Refer to the exhibit.

The YAML represented is using the ios_vrf module. As part of the Ansible playbook workflow, what is the result when this task is run?
A. VRFs not defined in the host_vars file are removed from the device.
B. VRFs not defined in the host_vars file are added to the device, and any other VRFs on the device remain.
C. VRFs defined in the host_vars file are removed from the device.
D. VRFs are added to the device from the host_vars file, and any other VRFs on the device are removed.
-
Question 296:
Which two types of organization are subject to GDPR? (Choose two.)
A. only organizations that operate outside the EU
B. any organization that offers goods or services to customers in the EU
C. only organizations that have offices in countries that are part of the EU
D. any organization that operates within the EU
E. only organizations that physically reside in the EU
-
Question 297:
Refer to the exhibit.
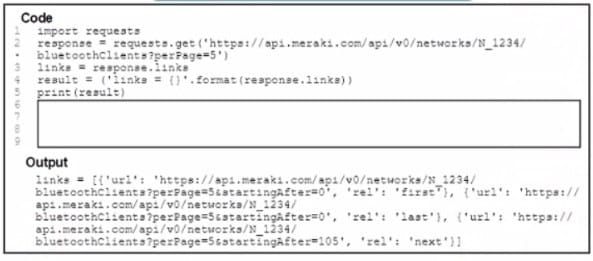
A Python script has these requirements
Retrieve a list of Bluetooth clients seen by the access pants on a network. Print the content of the response Retrieve the next page only if it is available in the response headers
What must be added where the code is missing to get the remaining pages by using the next link from the link response header of the last request?

A. B. C. D.
-
Question 298:
Which Git command enables the developer to revert back to f414f31 commit to discard changes in the current working tree?
A. git reset-hard f414f31
B. git reset checkout-hard f414f31
C. git reset-soft f414f31
D. git checkout f414f31
-
Question 299:
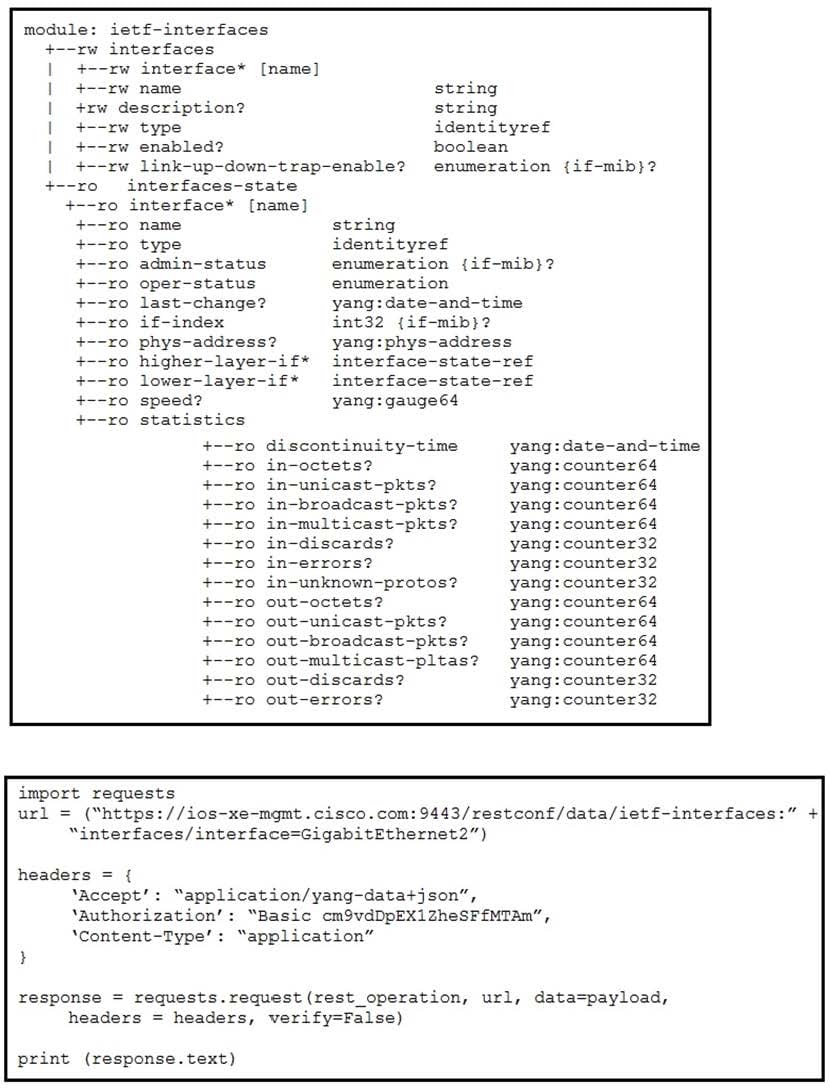
Refer to the exhibits. An interface named "GigabitEthernet2" has been configured on a Cisco IOS XE device. Using RESTCONF APIs as defined by the ietf-interfaces@2014-05- 08.yang model, which two combinations of "rest_operation" and "payload" must be added to the Python script to set the "description" to "Configured by RESTCONF"? (Choose two.)

A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
-
Question 300:
A team of developers created their own CA and started signing certificates for all of their loT devices. Which action will make the browser accept these certificates?
A. Set the private keys 1024-bit RSA.
B. Preload the developer CA on the trusted CA list of the browser.
C. Enable HTTPS or port 443 on the browser.
D. install a TLS instead of SSL certificate on the loT devices.
Related Exams:
300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-535
Automating and Programming Cisco Service Provider Solutions (SPAUTO)300-635
Automating and Programming Cisco Data Center Solutions (DCAUTO)300-735
Automating and Programming Cisco Security Solutions (SAUTO)300-835
Automating Cisco Collaboration Solutions (CLAUTO)300-910
Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)350-901
Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-901 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.