Exam Details
Exam Code
:412-79V8Exam Name
:EC-Council Certified Security Analyst (ECSA)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:200 Q&AsLast Updated
:Mar 31, 2025
EC-COUNCIL EC-COUNCIL Certifications 412-79V8 Questions & Answers
-
Question 111:
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
A. AES
B. DES (ECB mode)
C. MD5
D. RC5
-
Question 112:
Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and NTLMv2 value as 128 bits?
A. Hash Key Length
B. C/R Value Length
C. C/R Key Length
D. Hash Value Length
-
Question 113:
Traceroute is a computer network diagnostic tool for displaying the route (path) and measuring transit delays of packets across an Internet Protocol (IP) network. It sends a sequence of three Internet Control Message Protocol (ICMP) echo request packets addressed to a destination host. The time-to-live (TTL) value, also known as hop limit, is used in determining the intermediate routers being traversed towards the destination.
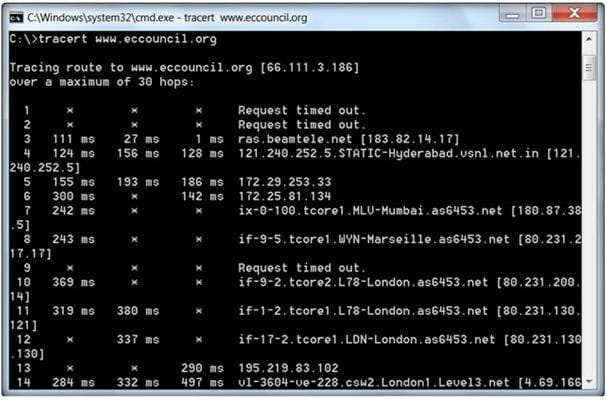
During routing, each router reduces packets' TTL value by
A. 3
B. 1
C. 4
D. 2
-
Question 114:
Which of the following is NOT generally included in a quote for penetration testing services?
A. Type of testing carried out
B. Type of testers involved
C. Budget required
D. Expected timescale required to finish the project
-
Question 115:
SQL injection attack consists of insertion or "injection" of either a partial or complete SQL query via the
data input or transmitted from the client (browser) to the web application.
A successful SQL injection attack can:
i)Read sensitive data from the database
iii)Modify database data (insert/update/delete)
iii)Execute administration operations on the database (such as shutdown the DBMS)
iV)Recover the content of a given file existing on the DBMS file system or write files into the file system
v)Issue commands to the operating system
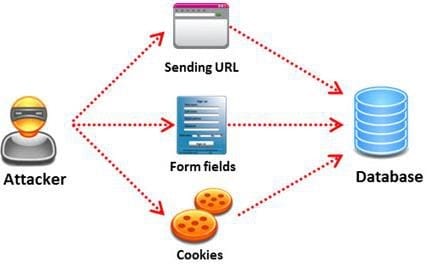
Pen tester needs to perform various tests to detect SQL injection vulnerability. He has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error.
In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
A. Automated Testing
B. Function Testing
C. Dynamic Testing
D. Static Testing
-
Question 116:
If a web application sends HTTP cookies as its method for transmitting session tokens, it may be vulnerable which of the following attacks?
A. Parameter tampering Attack
B. Sql injection attack
C. Session Hijacking
D. Cross-site request attack
-
Question 117:
Which of the following scan option is able to identify the SSL services?
A. sS
B. sV C. sU
D. sT
-
Question 118:
The amount of data stored in organizational databases has increased rapidly in recent years due to the rapid advancement of information technologies. A high percentage of these data is sensitive, private and critical to the organizations, their clients and partners.
Therefore, databases are usually installed behind internal firewalls, protected with intrusion detection mechanisms and accessed only by applications. To access a database, users have to connect to one of these applications and submit queries through them to the database. The threat to databases arises when these applications do not behave properly and construct these queries without sanitizing user inputs first. Identify the injection attack represented in the diagram below:
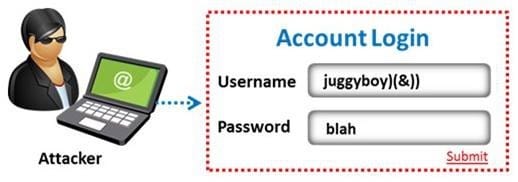
A. Frame Injection Attack
B. LDAP Injection Attack
C. XPath Injection Attack
D. SOAP Injection Attack
-
Question 119:
Which of the following protocol's traffic is captured by using the filter tcp.port==3389 in the Wireshark tool?
A. Reverse Gossip Transport Protocol (RGTP)
B. Real-time Transport Protocol (RTP)
C. Remote Desktop Protocol (RDP)
D. Session Initiation Protocol (SIP)
-
Question 120:
In the process of hacking a web application, attackers manipulate the HTTP requests to subvert the application authorization schemes by modifying input fields that relate to the user ID, username, access group, cost, file names, file identifiers, etc. They first access the web application using a low privileged account and then escalate privileges to access protected resources. What attack has been carried out?
A. XPath Injection Attack
B. Authorization Attack
C. Authentication Attack
D. Frame Injection Attack
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 412-79V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.