Exam Details
Exam Code
:500-420Exam Name
:Cisco AppDynamics Associate Performance Analyst (CAAPA)Certification
:AppDynamicsVendor
:CiscoTotal Questions
:64 Q&AsLast Updated
:Jul 10, 2025
Cisco AppDynamics 500-420 Questions & Answers
-
Question 11:
A development team responsible for the front-end shopping application has asked to receive an email every time the Java container thread count exceeds 25. Which alert and response capabilities settings will provide the email?
A. Node Health-JMX Thread Pools (> Specific Value) + Notification Action (Send an Email)
B. Node Health-Thread Pools (> Specific Value) + Notification Action (Send an Email)
C. Node Health-Thread Pools (> Specific Value) + Notification Action (Custom Action)
D. Node Health-JMX Thread Pools (> Baseline) + Notification Action (Send an Email)
-
Question 12:
Refer to the exhibit.
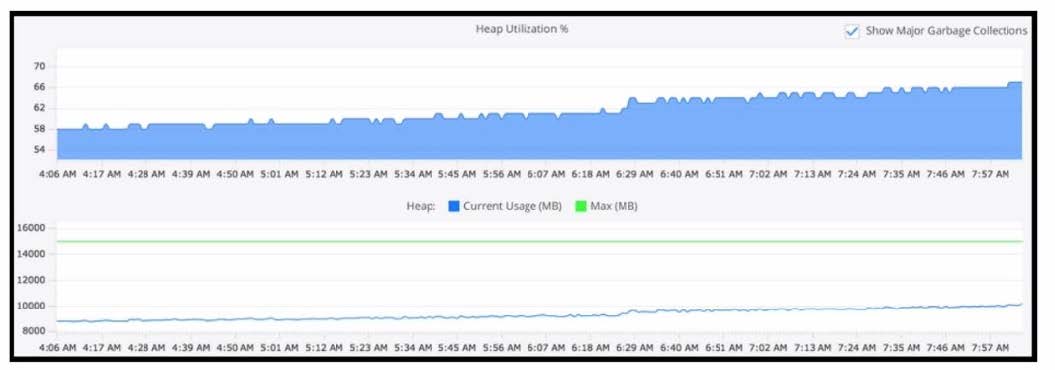
Using this heap utilization graph, which method is used to confirm if a memory leak is occurring during a certain time frame?
A. In metric browser go through Application Infrastructure > Hardware Resources and select Memory Total (MB) and Used (MB)
B. Refer to the Tiers and Nodes section and into the Memory tab and visualize Heap Utilization (%) and Heap Current Usage (MB) Vs Max (MB)
C. Refer to the Tiers and Nodes section and into the JMX tab and select JVM > Memory > Heap > Max Available (MB) and Current usage (MB)
D. In metric browser go through Application Infrastructure > Hardware Resources > Memory Total (MB) and Swap Used (MB)
-
Question 13:
Which two Key Performance Indicators (KPIs) accurately provide insight into server level resource consumption? (Choose two.)
A. Calls per Minute
B. Availability
C. Average Response Time
D. Application Restarts
E. CPU %Busy
F. Memory Used%
-
Question 14:
Which two statements are correct about creating Information Points? (Choose two.)
A. A wildcard can be used to select multiple methods for an Information Point.
B. A wildcard can be used to select multiple classes for an Information Point.
C. An Information Point can be created on the same class and method as a Custom Exit Point.
D. An Information Point can be created on a class and method that is executed before the Business Transaction entry point.
-
Question 15:
What AppDynamics Alert Action does a Performance Analyst need to select to post an AppDynamics event to a third-party collaboration tool?
A. Make an HTTP Request
B. Take a thread dump
C. Create or Update a JIRA Ticket
D. Run a script or executable on problematic nodes
-
Question 16:
How does a Performance Analyst identify if automatic remediation has been taken for a health rule violation?
A. Expand on the "Description" field to display "Actions Executed".
B. Review the "Application Dashboard" and review "Actions Executed"
C. Right-click on "view details" and click on the "Actions Executed" button.
D. Click on the link inside the Health Rule field and look for the "Affects" tab to display the Executed Actions.
-
Question 17:
Which feature can be used to determine if a given Java class is visible in AppDynamics?
A. Tools in Business Transaction Discovery Session
B. Preview Business transactions in Business Transaction Discovery Session
C. Use the thread dump feature on the node agent
D. Use the object instance tracking feature in memory
-
Question 18:
A Performance Analyst is reviewing Business Transactions with an Application team. The Application team would like to increase the Application Business Transaction limit because they need to have visibility into all the different transactions. What should the Performance Analyst do?
A. Do nothing since the limit is not important during configuration
B. Increase the limit to the requested value
C. Increase the limit half way between the current level and the requested value
D. Focus on the Business Transactions exceeding the limit and why
-
Question 19:
Which statement about Service End Points and Business Transactions is true?
A. Service End Points and Business Transactions can both be renamed by right clicking and selecting 'rename'.
B. Service End Points and Business Transactions can both configure data collectors.
C. Service End Points and Business Transactions can both be split.
D. Service End Points and Business Transactions both provide percentile metrics.
-
Question 20:
Which three data points can be located by drilling down into a JDBC exit call for an Oracle backend? (Choose three.)
A. Query type
B. Statement type
C. Query Id
D. Weight %
E. Originating node
F. %Time
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 500-420 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.