Exam Details
Exam Code
:C2180-279Exam Name
:IBM Worklight V6.0 Mobile System AdministrationCertification
:IBM Certified Mobile System AdministratorVendor
:IBMTotal Questions
:126 Q&AsLast Updated
:Apr 12, 2025
IBM IBM Certified Mobile System Administrator C2180-279 Questions & Answers
-
Question 71:
Once a Shell developer completes developing her Shell components, what is the proper way to distribute it to inner application developers?
A. Zipping the Worklight project and emailing it to inner application developers
B. Committing the Worklight project to a Source Control Management system and telling inner application developers to use source code from it
C. The Shell developer should not distribute the Shell component to inner application developers. They should send their inner applications to her in order to build them
D. Sending the .wlshell Shell bundle file to inner application developers
-
Question 72:
Which authenticators are supported out of the box? (Choose three)
A. Header authentication
B. Persistent cookie authentication
C. Form-based authentication
D. Kerberos authentication
-
Question 73:
A developer is preparing a Worklight mobile application for deployment to a production environment where the Worklight Server core database is stored on DB2 and must be accessed using the WorklightDS data source.
Which database properly settings must the developer specify in the application's worklight. properties file to properly configure it for deployment to the production environment?
A. wl.db.type=DB2 wl.dta.url=jdtac:db2:WorklightDS
B. wl.db.type=DB2 wl. db. j ndi.name=j dbc/WorklightDS
C. wl.db.driver=com.ibm.db2.jcc.DB2Driver wl. db. j ndi.neune=jdbc/WorklightDS
D. wl.db.driver=com.ibm.db2.jcc.DB2Driver wl.db.url=jdbc:db2:WorklightDS
-
Question 74:
Which three components must be implemented when defining an authentication realm? (Choose three.)
A. Authenticator
B. Login module
C. Identity validator
D. Challenge handler
E. Security certificate
F. Encryption module
G. Secure connection
-
Question 75:
A developer is debugging a form-based authentication and at a point the issue is narrowed down to the challengeHandler object. The following implementation describes the challenge handler:
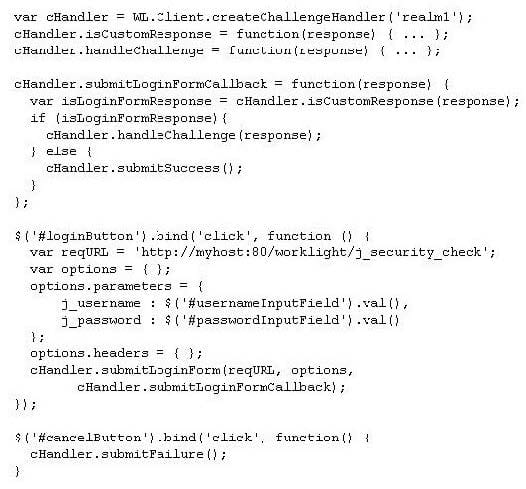
What is the problem with this challenge handler?
A. The user is not implementing the mandatory challenge handler functions submitFailure() and submitSuccess().
B. The user credentials should be sent to the server using a secured protocol. The correct definition is:var reqURL = 'https://myhost:80/worklight/j_security_check';.
C. The variable reqURL cannot include the hostname and port. The correct definition is:var reqURL = '/ j_security_check';.
D. The function createChallengeHandler() is not properly invoked, it also takes the security test. The correct definition is:var cHandler = WL.Client.createChallengeHandler('test1', 'realm1');.
-
Question 76:
Which Worklight pre-defined authentication methods can be used to secure an application that does not require the user to login interactively?
A. Form-based authentication
B. LDAP-based authentication
C. Header-based authentication
D. Adapter-based authentication
-
Question 77:
An application needs to log into an existing backend with the fields username, password, pin code and account number. Which set of actions does the developer need to take in addition to creating a custom Java Authenticator?
A. - Use the auth.js as is to display the login form- Configure the authenticationConfig.xml- Create client-side authentication components
B. - Configure the authenticationConfig.xml- Configure the worklight.properties- Create client-side authentication components
C. - Configure the authenticationConfig.xml- Create a custom Java Login Module- Create client-side authentication components
D. - Configure the authenticationConfig.xml- Create a custom Java Login Module- Use the auth.js as is to display the login form
-
Question 78:
A developer is debugging a Worklight Adapter procedure that has been configured with the following securityTest property in the adapter configuration file:
When the adapter procedure getSecureFeed is invoked by the client, the developer has noted that the Worklight Server responds with HTML content rather than the expected JSON content from getSecuredFeed function.
Which assertion is correct?
A. The Worklight Server is returning a dynamically generated HTML form indicating that the request is authenticated.
B. The Adapter procedure is protected by either Form-based authenticator or Java-based (using custom Login Module).
C. The Adapter procedure is protected by Adapter-based authenticator and the Worklight Server has rejected the authentication.
D. The Adapter procedure is protected by Form-based authenticator and the Worklight Server is responding to an unauthenticated request.
-
Question 79:
Which Worklight pre-defined authenticators can be used to secure an application that requires the user to login with a user ID and password?
A. Form-based authenticator or Header-based authenticator
B. Form-based authenticator or Adapter-based authenticator
C. Adapter-based authenticator or Header-based authenticator
D. Form-based authenticator, Adapter-based authenticator or Header-based authenticator
-
Question 80:
A developer wants to implement an adapter authentication solution. The developer created the following challenge handler:

What should be placed in the "to be filled" parameter?
A. realm name
B. module name
C. procedure name D. security test name
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only IBM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your C2180-279 exam preparations and IBM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.