Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 181:
A security analyst is reviewing the output of tcpdump to analyze the type of activity on a packet capture:
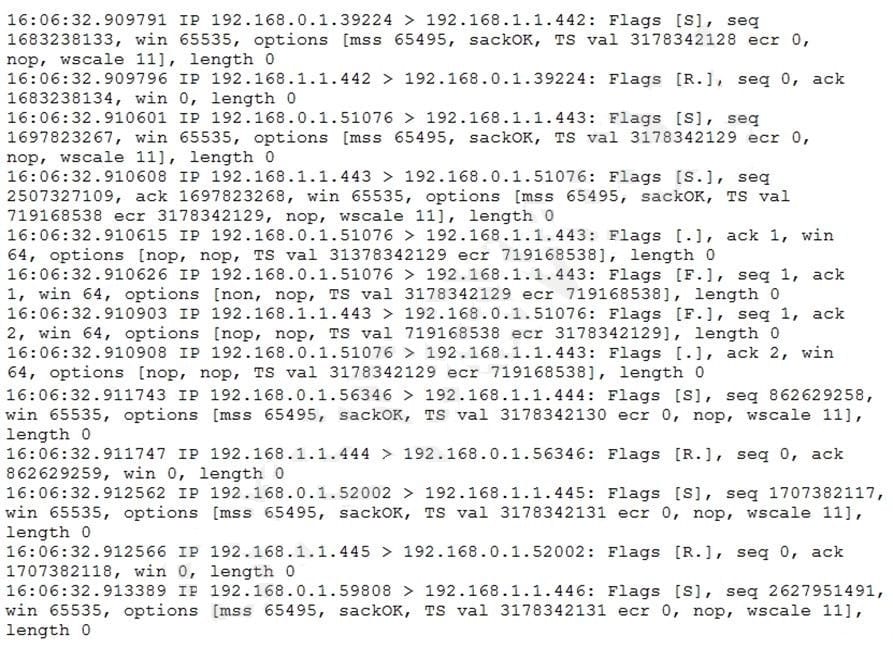
Which of the following generated the above output?
A. A port scan
B. A TLS connection
C. A vulnerability scan
D. A ping sweep
-
Question 182:
A network appliance manufacturer is building a new generation of devices and would like to include chipset security improvements. Management wants the security team to implement a method to prevent security weaknesses that could be reintroduced by downgrading the firmware version on the chipset. Which of the following would meet this objective?
A. UEFI
B. A hardware security module
C. eFUSE
D. Certificate signed updates
-
Question 183:
Which of the following assessment methods should be used to analyze how specialized software performs during heavy loads?
A. Stress test
B. API compatibility lest
C. Code review
D. User acceptance test
E. Input validation
-
Question 184:
Which of the following are considered PII by themselves? (Choose two.)
A. Government ID
B. Job title
C. Employment start date
D. Birth certificate
E. Credit card
F. Mother's maiden name
-
Question 185:
A security analyst identified some potentially malicious processes after capturing the contents of memory from a machine during incident response. Which of the following procedures is the NEXT step for further investigation?
A. Data carving
B. Timeline construction
C. File cloning
D. Reverse engineering
-
Question 186:
Law enforcement has notified an organization that one of its internal servers is suspected of being a command-and-control server for a malicious botnet. The organization's security analyst has been tasked with analyzing the internal server for indications of compromise. During the investigation, the analyst reviews the processes running on the server and sees the following:
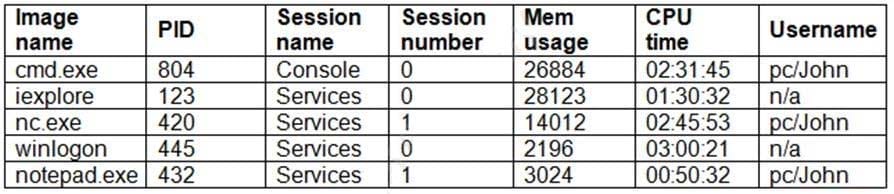
Which of the following processes warrants further investigation?
A. cmd.exe
B. iexplore
C. nc.exe
D. notepad.exe
-
Question 187:
A security analyst needs to develop a brief that will include the latest incidents and the attack phases of the incidents. The goal is to support threat intelligence and identify whether or not the incidents are linked. Which of the following methods would be MOST appropriate to use?
A. The Cyber Kill Chain
B. The MITRE ATTandCK framework
C. An adversary capability model
D. The Diamond Model of Intrusion Analysis
-
Question 188:
A small organization has proprietary software that is used internally. The system has not been well maintained and cannot be updated with the rest of the environment. Which of the following is the BEST solution?
A. Virtualize the system and decommission the physical machine.
B. Remove it from the network and require air gapping.
C. Implement privileged access management for identity access.
D. Implement MFA on the specific system.
-
Question 189:
A computer hardware manufacturer is developing a new SoC that will be used by mobile devices. The SoC should not allow users or the process to downgrade from a newer firmware to an older one. Which of the following can the hardware manufacturer implement to prevent firmware downgrades?
A. Encryption
B. eFuse
C. Secure Enclave
D. Trusted execution
-
Question 190:
A security analyst needs to acquire an image of a whole partition from a server in order to perform a forensic analysis. The server must be available while this is being performed. Which of the following procedures will acquire the image and ensure server availability?
A. Unplug the server's hard drive and then plug it into a forensic station to perform the full disk-cloning procedure.
B. Store the evidence that is collected on the server's hard drive until it can be transferred to a NAS.
C. Run robocopy to copy the partition contents to a USB drive
D. Run dd to send the output through the network using netcat to a remote station.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.