Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 201:
A security analyst's daily review of system logs and SIEM showed fluctuating patterns of latency. During the analysis, the analyst discovered recent attempts of intrusion related to malware that overwrites the MBR. The facilities manager informed the analyst that a nearby construction project damaged the primary power lines, impacting the analyst's support systems. The electric company has temporarily restored power, but the area may experience temporary outages.
Which of the following issues the analyst focus on to continue operations?
A. Updating the ACL
B. Conducting backups
C. Virus scanning
D. Additional log analysis
-
Question 202:
An organization has been conducting penetration testing to identify possible network vulnerabilities. One of the security policies states that web servers and database servers must not be co-located on the same server unless one of them runs on a non-standard. The penetration tester has received the following outputs from the latest set of scans:
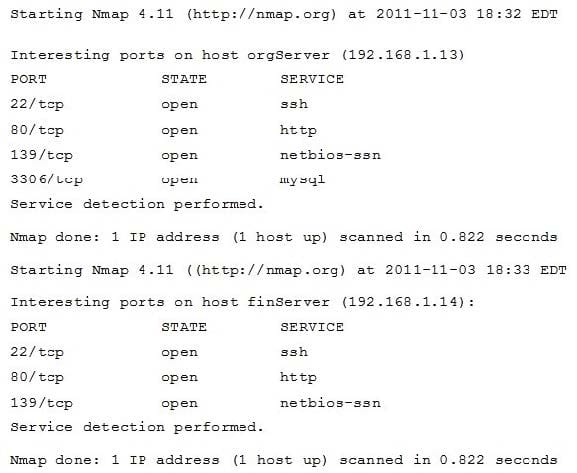
Which of the following servers is out of compliance?
A. finServer
B. adminServer
C. orgServer
D. opsServer
-
Question 203:
A security analyst receives a mobile device with symptoms of a virus infection. The virus is morphing whenever it is from sandbox to sandbox to analyze. Which of the following will help to identify the number of variations through the analysis life cycle?
A. Journaling
B. Hashing utilities
C. Log viewers
D. OS and process analysis
-
Question 204:
A security engineer has been asked to reduce the attack surface on an organization's production environment. To limit access, direct VPN access to all systems must be terminated, and users must utilize multifactor authentication to access a constrained VPN connection and then pivot to other production systems form a bastion host. The MOST appropriate way to implement the stated requirement is through the use of a:
A. sinkhole.
B. multitenant platform.
C. single-tenant platform.
D. jump box
-
Question 205:
Which of the following BEST describes why vulnerabilities found in ICS and SCADA can be difficult to remediate?
A. ICS/SCADA systems are not supported by the CVE publications.
B. ICS/SCADA systems rarely have full security functionality.
C. ICS/SCADA systems do not allow remote connections.
D. ICS/SCADA systems use encrypted traffic to communicate between devices.
-
Question 206:
In reviewing service desk requests, management has requested that the security analyst investigate the requests submitted by the new human resources manager. The requests consist of "unlocking" files that belonged to the previous human manager. The security analyst has uncovered a tool that is used to display five-level passwords. This tool is being used by several members of the service desk to unlock files. The content of these particular files is highly sensitive information pertaining to personnel. Which of the following BEST describes this scenario?
A. Unauthorized data exfiltration
B. Unauthorized data masking
C. Unauthorized access
D. Unauthorized software
E. Unauthorized controls
-
Question 207:
Which of the following systems or services is MOST likely to exhibit issues stemming from the Heartbleed vulnerability (Choose two.)
A. SSH daemons
B. Web servers
C. Modbus devices
D. TLS VPN services
E. IPSec VPN concentrators
F. SMB service
-
Question 208:
An analyst was investigating the attack that took place on the network. A user was able to access the system without proper authentication. Which of the following will the analyst recommend, related to management approaches, in order to control access? (Choose three.)
A. RBAC
B. LEAP
C. DAC
D. PEAP
E. MAC
F. SCAP
G. BCP
-
Question 209:
A security analyst positively identified the threat, vulnerability, and remediation. The analyst is ready to implement the corrective control. Which of the following would be the MOST inhibiting to applying the fix?
A. Requiring a firewall reboot.
B. Resetting all administrator passwords.
C. Business process interruption.
D. Full desktop backups.
-
Question 210:
A security analyst is assisting in the redesign of a network to make it more secure. The solution should be low cost, and access to the secure segments should be easily monitored, secured, and controlled. Which of the following should be implemented?
A. System isolation
B. Honeyport
C. Jump box
D. Mandatory access control
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.