Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 241:
Which of the following describes why it is important for an organization's incident response team and legal department to meet and discuss communication processes during the incident response process?
A. To comply with existing organization policies and procedures on interacting with internal and external parties
B. To ensure all parties know their roles and effective lines of communication are established
C. To identify which group will communicate details to law enforcement in the event of a security incident
D. To predetermine what details should or should not be shared with internal or external parties in the event of an incident
-
Question 242:
The security team has determined that the current incident response resources cannot meet management's objective to secure a forensic image for all serious security incidents within 24 hours. Which of the following compensating controls can be used to help meet management's expectations?
A. Separation of duties
B. Scheduled reviews
C. Dual control
D. Outsourcing
-
Question 243:
When reviewing the system logs, the cybersecurity analyst noticed a suspicious log entry:
wmic /node: HRDepartment1 computersystem get username
Which of the following combinations describes what occurred, and what action should be taken in this situation?
A. A rogue user has queried for users logged in remotely. Disable local access to network shares.
B. A rogue user has queried for the administrator logged into the system. Attempt to determine who executed the command.
C. A rogue user has queried for the administrator logged into the system. Disable local access to use cmd prompt.
D. A rogue user has queried for users logged into in remotely. Attempt to determine who executed the command.
-
Question 244:
A cybersecurity analyst is currently auditing a new Active Directory server for compliance. The analyst uses Nessus to do the initial scan, and Nessus reports the following: Which of the following critical vulnerabilities has the analyst discovered?
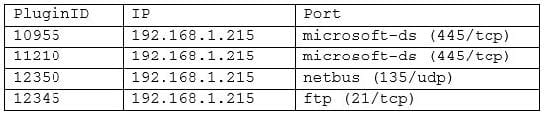
A. Known backdoor
B. Zero-day
C. Path disclosure
D. User enumeration
-
Question 245:
A threat intelligence analyst who is working on the SOC floor has been forwarded an email that was sent to one of the executives in business development. The executive mentions the email was from the Chief Executive Officer (CEO), who was requesting an emergency wire transfer. This request was unprecedented. Which of the following threats MOST accurately aligns with this behavior?
A. Phishing
B. Whaling
C. Spam
D. Ransomware
-
Question 246:
An organization has two environments: development and production. Development is where applications are developed with unit testing. The development environment has many configuration differences from the production environment. All applications are hosted on virtual machines. Vulnerability scans are performed against all systems before and after any application or configuration changes to any environment. Lately, vulnerability remediation activity has caused production applications to crash and behave unpredictably. Which of the following changes should be made to the current vulnerability management process?
A. Create a third environment between development and production that mirrors production and tests all changes before deployment to the users
B. Refine testing in the development environment to include fuzzing and user acceptance testing so applications are more stable before they migrate to production
C. Create a second production environment by cloning the virtual machines, and if any stability problems occur, migrate users to the alternate production environment
D. Refine testing in the production environment to include more exhaustive application stability testing while continuing to maintain the robust vulnerability remediation activities
-
Question 247:
The human resources division is moving all of its applications to an IaaS cloud. The Chief Information Officer (CIO) has asked the security architect to design the environment securely to prevent the IaaS provider from accessing its data-atrest and data-in-transit within the infrastructure. Which of the following security controls should the security architect recommend?
A. Implement a non-data breach agreement
B. Ensure all backups are remote outside the control of the IaaS provider
C. Ensure all of the IaaS provider's workforce passes stringent background checks
D. Render data unreadable through the use of appropriate tools and techniques
-
Question 248:
Which of the following command line utilities would an analyst use on an end-user PC to determine the ports it is listening on?
A. tracert
B. ping
C. nslookup
D. netstat
-
Question 249:
A cybersecurity analyst is currently using Nessus to scan several FTP servers. Upon receiving the results of the scan, the analyst needs to further test to verify that the vulnerability found exists. The analyst uses the following snippet of code:
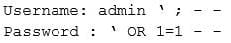
Which of the following vulnerabilities is the analyst checking for?
A. Buffer overflow
B. SQL injection
C. Default passwords
D. Format string attack
-
Question 250:
During a quarterly review of user accounts and activity, a security analyst noticed that after a password reset the head of human resources has been logging in from multiple external locations, including several overseas. Further review of the account showed access rights to a number of corporate applications, including a sensitive accounting application used for employee bonuses. Which of the following security methods could be used to mitigate this risk?
A. RADIUS identity management
B. Context-based authentication
C. Privilege escalation restrictions
D. Elimination of self-service password resets
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.