Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 261:
A cyber-incident response team is responding to a network intrusion incident on a hospital network. Which of the following must the team prepare to allow the data to be used in court as evidence?
A. Computer forensics form
B. HIPAA response form
C. Chain of custody form
D. Incident form
-
Question 262:
Malicious users utilized brute force to access a system. An analyst is investigating these attacks and recommends methods to management that would help secure the system. Which of the following controls should the analyst recommend? (Choose three.)
A. Multifactor authentication
B. Network segmentation
C. Single sign-on
D. Encryption
E. Complexity policy
F. Biometrics
G. Obfuscation
-
Question 263:
A suite of three production servers that were originally configured identically underwent the same vulnerability scans. However, recent results revealed the three servers has different critical vulnerabilities. The servers are not accessible by the Internet, and AV programs have not detected any malware. The servers' syslog files do not show any unusual traffic since they were installed and are physically isolated in an off-site datacenter. Checksum testing of random executables does not reveal tampering. Which of the following scenarios is MOST likely?
A. Servers have not been scanned with the latest vulnerability signature
B. Servers have been attacked by outsiders using zero-day vulnerabilities
C. Servers were made by different manufacturers
D. Servers have received different levels of attention during previous patch management events
-
Question 264:
A cybersecurity analyst was asked to review several results of web vulnerability scan logs. Given the following snippet of code:
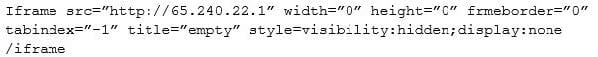
Which of the following BEST describes the situation and recommendations to be made?
A. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. The code should include the domain name. Recommend the entry be updated with the domain name.
B. The security analyst has discovered an embedded iframe that is hidden from users accessing the web page. This code is correct. This is a design preference, and no vulnerabilities are present.
C. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. The link is hidden and suspicious. Recommend the entry be removed from the web page.
D. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. Recommend making the iframe visible. Fixing the code will correct the issue.
-
Question 265:
A security analyst is running a routine vulnerability scan against a web farm. The farm consists of a single server acting as a load-balancing reverse proxy and offloads cryptographic processes to the backend servers. The backend servers consist of four servers that process the inquiries for the front end.
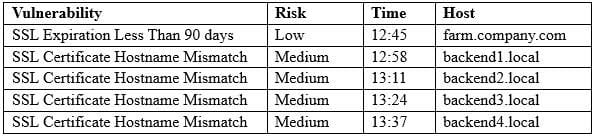
A web service SSL query of each server responds with the same output:
Connected (0x000003) depth=0 /0=farm.company.com/CN=farm.company.com/OU=Domain Control Validated Which of the following results BEST addresses these findings?
A. Advise the application development team that the SSL certificates on the backend servers should be revoked and reissued to match their hostnames
B. Notify the application development team of the findings and advise management of the results
C. Create an exception in the vulnerability scanner, as the results and false positives and can be ignored safely
D. Require that the application development team renews the farm certificate and includes a wildcard for the `local' domain in the certificate SAN field
-
Question 266:
An analyst suspects a large database that contains customer information and credit card data was exfiltrated to a known hacker group in a foreign country. Which of the following incident response steps should the analyst take FIRST?
A. Immediately notify law enforcement, as they may be able to help track down the hacker group before customer information is disseminated.
B. Draft and publish a notice on the company's website about the incident, as PCI regulations require immediate disclosure in the case of a breach of PII or card data.
C. Isolate the server, restore the database to a time before the vulnerability occurred, and ensure the database is encrypted.
D. Document and verify all evidence and immediately notify the company's Chief Information Security Officer (CISO) to better understand the next steps.
-
Question 267:
A company's IDP/DLP solution triggered the following alerts:
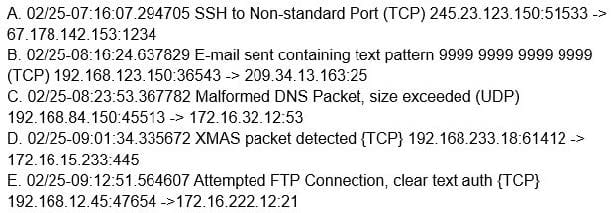
Which of the following alerts should a security analyst investigate FIRST?
A. A
B. B
C. C
D. D
E. E
-
Question 268:
Employees at a manufacturing plant have been victims of spear phishing, but security solutions prevented further intrusions into the network. Which of the following is the MOST appropriate solution in this scenario?
A. Continue to monitor security devices
B. Update antivirus and malware definitions
C. Provide security awareness training
D. Migrate email services to a hosted environment
-
Question 269:
A new security manager was hired to establish a vulnerability management program. The manager asked for a corporate strategic plan and risk register that the project management office developed. The manager conducted a tools and skill sets inventory to document the plan. Which of the following is a critical task for the establishment of a successful program?
A. Establish continuous monitoring
B. Update vulnerability feed
C. Perform information classification
D. Establish corporate policy
-
Question 270:
A threat intelligence analyst who works for an oil and gas company has received the following email from a superior:
"We will be connecting our IT network with our ICS. Our IT security has historically been top of the line, and this convergence will make the ICS easier to manage and troubleshoot. Can you please perform a risk/vulnerability assessment on this decision?"
Which of the following is MOST accurate regarding ICS in this scenario?
A. Convergence decreases attack vectors
B. Integrating increases the attack surface
C. IT networks cannot be connected to ICS infrastructure
D. Combined networks decrease efficiency
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.