Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 291:
A security analyst is making recommendations for securing access to the new forensic workstation and workspace. Which of the following security measures should the analyst recommend to protect access to forensic data?
A. Multifactor authentication Polarized lens protection Physical workspace isolation
B. Secure ID token Security reviews of the system at least yearly Polarized lens protection
C. Bright lightning in all access areas Security reviews of the system at least yearly Multifactor authentication
D. Two-factor authentication into the building Separation of duties Warning signs placed in clear view
-
Question 292:
A company has monthly scheduled windows for patching servers and applying configuration changes. Out-of-window changes can be done, but they are discouraged unless absolutely necessary. The systems administrator is reviewing the weekly vulnerability scan report that was just released. Which of the following vulnerabilities should the administrator fix without waiting for the next scheduled change window?
A. The administrator should fix dns (53/tcp). BIND `NAMED' is an open-source DNS server from ISC.org. The BIND-based NAMED server (or DNS servers) allow remote users to query for version and type information.
B. The administrator should fix smtp (25/tcp). The remote SMTP server is insufficiently protected against relaying. This means spammers might be able to use the company's mail server to send their emails to the world.
C. The administrator should fix http (80/tcp). An information leak occurs on Apache web servers with the UserDir module enabled, allowing an attacker to enumerate accounts by requesting access to home directories and monitoring the response.
D. The administrator should fix http (80/tcp). The `greeting.cgi' script is installed. This CGI has a well-known security flaw that lets anyone execute arbitrary commands with the privileges of the http daemon.
E. The administrator should fix general/tcp. The remote host does not discard TCP SYN packets that have the FIN flag set. Depending on the kind of firewall a company is using, an attacker may use this flaw to bypass its rules.
-
Question 293:
A list of vulnerabilities has been reported in a company's most recent scan of a server. The security analyst must review the vulnerabilities and decide which ones should be remediated in the next change window and which ones can wait or may not need patching. Pending further investigation. Which of the following vulnerabilities should the analyst remediate FIRST?
A. The analyst should remediate https (443/tcp) first. This web server is susceptible to banner grabbing and was fingerprinted as Apache/1.3.27-9 on Linux w/ mod_fastcgi.
B. The analyst should remediate dns (53/tcp) first. The remote BIND 9 DNS server is susceptible to a buffer overflow, which may allow an attacker to gain a shell on this host or disable this server.
C. The analyst should remediate imaps (993/tcp) first. The SSLv2 suite offers five strong ciphers and two weak "export class" ciphers.
D. The analyst should remediate ftp (21/tcp) first. An outdated version of FTP is running on this port. If it is not in use, it should be disabled.
-
Question 294:
A company decides to move three of its business applications to different outsourced cloud providers. After moving the applications, the users report the applications time out too quickly and too much time is spent logging back into the different web-based applications throughout the day. Which of the following should a security architect recommend to improve the end-user experience without lowering the security posture?
A. Configure directory services with a federation provider to manage accounts.
B. Create a group policy to extend the default system lockout period.
C. Configure a web browser to cache the user credentials.
D. Configure user accounts for self-service account management.
-
Question 295:
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has received the following output from the latest scan:
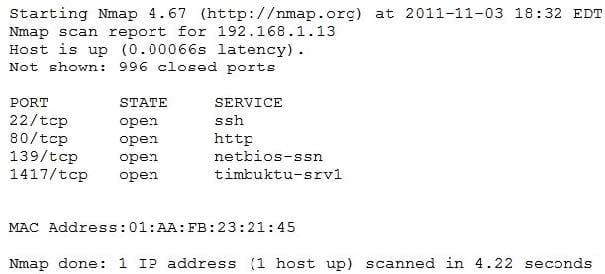
The penetration tester knows the organization does not use Timbuktu servers and wants to have Nmap interrogate the ports on the target in more detail. Which of the following commands should the penetration tester use NEXT?
A. nmap V 192.168.1.13 1417
B. nmap S 192.168.1.13 1417
C. sudo nmap S 192.168.1.13
D. nmap 192.168.1.13
-
Question 296:
A security incident has been created after noticing unusual behavior from a Windows domain controller. The server administrator has discovered that a user logged in to the server with elevated permissions, but the user's account does not follow the standard corporate naming scheme. There are also several other accounts in the administrators group that do not follow this naming scheme. Which of the following is the possible cause for this behavior and the BEST remediation step?
A. The Windows Active Directory domain controller has not completed synchronization, and should force the domain controller to sync.
B. The server has been compromised and should be removed from the network and cleaned before reintroducing it to the network.
C. The server administrator created user accounts cloning the wrong user ID, and the accounts should be removed from administrators and placed in an employee group.
D. The naming scheme allows for too many variations, and the account naming convention should be updates to enforce organizational policies.
-
Question 297:
A company's asset management software has been discovering a weekly increase in non-standard software installed on end users' machines with duplicate license keys. The security analyst wants to know if any of this software is listening on any non-standard ports, such as 6667. Which of the following tools should the analyst recommend to block any command and control traffic?
A. Netstat
B. NIDS
C. IPS
D. HIDS
-
Question 298:
A security analyst is reviewing output from a CVE-based vulnerability scanner. Before conducting the scan, the analyst was careful to select only Windows-based servers in a specific datacenter. The scan revealed that the datacenter includes 27 machines running Windows 2003 Server Edition (Win2003SE). In 2015, there were 36 new vulnerabilities discovered in the Win2003SE environment. Which of the following statements are MOST likely applicable? (Choose two.)
A. Remediation is likely to require some form of compensating control.
B. Microsoft's published schedule for updates and patches for Win2003SE have continued uninterrupted.
C. Third-party vendors have addressed all of the necessary updates and patches required by Win2003SE.
D. The resulting report on the vulnerability scan should include some reference that the scan of the datacenter included 27 Win2003SE machines that should be scheduled for replacement and deactivation.
E. Remediation of all Win2003SE machines requires changes to configuration settings and compensating controls to be made through Microsoft Security Center's Win2003SE Advanced Configuration Toolkit.
-
Question 299:
An analyst is reviewing the following log from the company web server:

Which of the following is this an example of?
A. Online rainbow table attack
B. Offline brute force attack
C. Offline dictionary attack
D. Online hybrid attack
-
Question 300:
In an effort to be proactive, an analyst has run an assessment against a sample workstation before auditors visit next month. The scan results are as follows:
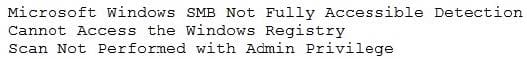
Based on the output of the scan, which of the following is the BEST answer?
A. Failed credentialed scan
B. Failed compliance check
C. Successful sensitivity level check
D. Failed asset inventory
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.