Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 311:
A cybersecurity analyst develops a regular expression to find data within traffic that will alarm on a hit.
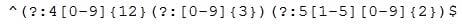
The SIEM alarms on seeing this data in cleartext between the web server and the database server.
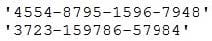
Which of the following types of data would the analyst MOST likely to be concerned with, and to which type of data classification does it belong?
A. Credit card numbers that are PCI
B. Social security numbers that are PHI
C. Credit card numbers that are PII
D. Social security numbers that are PII
-
Question 312:
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has already identified active hosts in the network and is now scanning individual hosts to determine if any are running a web server. The output from the latest scan is shown below:
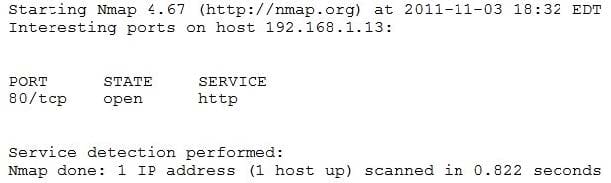
Which of the following commands would have generated the output above?
A. map V 192.168.1.13 80
B. map P 192.168.1.0/24 ALL
C. map V 192.168.1.1 80
D. map P 192.168.1.13 ALL
-
Question 313:
Which of the following describes why it is important to include scope within the rules of engagement of a penetration test?
A. To ensure the network segment being tested has been properly secured
B. To ensure servers are not impacted and service is not degraded
C. To ensure all systems being scanned are owned by the company
D. To ensure sensitive hosts are not scanned
-
Question 314:
A security analyst is performing ongoing scanning and continuous monitoring of the corporate datacenter. Over time, these scans are repeatedly showing susceptibility to the same vulnerabilities and an increase in new vulnerabilities on a specific group of servers that are clustered to run the same application. Which of the following vulnerability management processes should be implemented?
A. Frequent server scanning
B. Automated report generation
C. Group policy modification
D. Regular patch application
-
Question 315:
An analyst is preparing for a technical security compliance check on all Apache servers. Which of the following will be the BEST to use?
A. CIS benchmark
B. Nagios
C. OWASP
D. Untidy
E. Cain and Abel
-
Question 316:
A company provides wireless connectivity to the internal network from all physical locations for company-owned devices. Users were able to connect the day before, but now all users have reported that when they connect to an access point in the conference room, they cannot access company resources. Which of the following BEST describes the cause of the problem?
A. The access point is blocking access by MAC address. Disable MAC address filtering.
B. The network is not available. Escalate the issue to network support.
C. Expired DNS entries on users' devices. Request the affected users perform a DNS flush.
D. The access point is a rogue device. Follow incident response procedures.
-
Question 317:
A security analyst received an alert from the antivirus software identifying a complex instance of malware on a company's network. The company does not have the resources to fully analyze the malware and determine its effect on the system. Which of the following is the BEST action to take in the incident recovery and post-incident response process?
A. Wipe hard drives, reimage the systems, and return the affected systems to ready state.
B. Detect and analyze the precursors and indicators; schedule a lessons learned meeting.
C. Remove the malware and inappropriate materials; eradicate the incident.
D. Perform event correlation; create a log retention policy.
-
Question 318:
A logistics company's vulnerability scan identifies the following vulnerabilities on Internet-facing devices in the DMZ: SQL injection on an infrequently used web server that provides files to vendors SSL/TLS not used for a website that contains promotional information The scan also shows the following vulnerabilities on internal resources: Microsoft Office Remote Code Execution on test server for a human resources system TLS downgrade vulnerability on a server in a development network
In order of risk, which of the following should be patched FIRST?
A. Microsoft Office Remote Code Execution
B. SQL injection
C. SSL/TLS not used
D. TLS downgrade
-
Question 319:
NOTE: Question IP must be 192.168.192.123
During a network reconnaissance engagement, a penetration tester was given perimeter firewall ACLs to accelerate the scanning process. The penetration tester has decided to concentrate on trying to brute force log in to destination IP address 192.168.192.132 via secure shell.

Given a source IP address of 10.10.10.30, which of the following ACLs will permit this access?
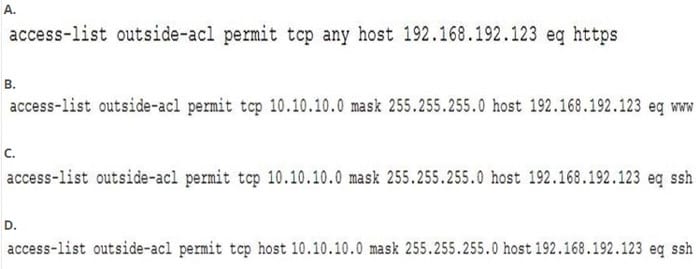
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 320:
A cybersecurity analyst is reviewing Apache logs on a web server and finds that some logs are missing. The analyst has identified that the systems administrator accidentally deleted some log files. Which of the following actions or rules should be implemented to prevent this incident from reoccurring?
A. Personnel training
B. Separation of duties
C. Mandatory vacation
D. Backup server
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.