Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 371:
A cybersecurity consultant found common vulnerabilities across the following services used by multiple servers at an organization: VPN, SSH, and HTTPS. Which of the following is the MOST likely reason for the discovered vulnerabilities?
A. Leaked PKI private key
B. Vulnerable version of OpenSSL
C. Common initialization vector
D. Weak level of encryption entropy
E. Vulnerable implementation of PEAP
-
Question 372:
A recent audit included a vulnerability scan that found critical patches released 60 days prior were not applied to servers in the environment. The infrastructure team was able to isolate the issue and determined it was due to a service being disabled on the server running the automated patch management application. Which of the following would be the MOST efficient way to avoid similar audit findings in the future?
A. Implement a manual patch management application package to regain greater control over the process.
B. Create a patch management policy that requires all servers to be patched within 30 days of patch release.
C. Implement service monitoring to validate that tools are functioning properly.
D. Set services on the patch management server to automatically run on start-up.
-
Question 373:
A medical organization recently started accepting payments over the phone. The manager is concerned about the impact of the storage of different types of data. Which of the following types of data incurs the highest regulatory constraints?
A. PHI
B. PCI
C. PII
D. IP
-
Question 374:
An organization wants to remediate vulnerabilities associated with its web servers. An initial vulnerability scan has been performed, and analysts are reviewing the results. Before starting any remediation, the analysts want to remove false positives to avoid spending time on issues that are not actual vulnerabilities. Which of the following would be an indicator of a likely false positive?
A. Reports indicate that findings are informational.
B. Any items labeled `low' are considered informational only.
C. The scan result version is different from the automated asset inventory.
D. `HTTPS' entries indicate the web page is encrypted securely.
-
Question 375:
During an investigation, a computer is being seized. Which of the following is the FIRST step the analyst should take?
A. Power off the computer and remove it from the network.
B. Unplug the network cable and take screenshots of the desktop.
C. Perform a physical hard disk image.
D. Initiate chain-of-custody documentation.
-
Question 376:
A security analyst has determined the security team should take action based on the following log:
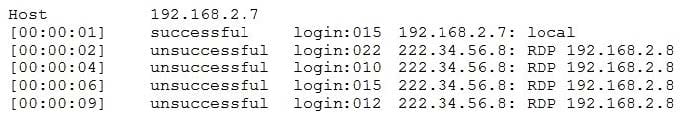
Which of the following should be used to improve the security posture of the system?
A. Enable login account auditing.
B. Limit the number of unsuccessful login attempts.
C. Upgrade the firewalls.
D. Increase password complexity requirements.
-
Question 377:
An organization has recently experienced a data breach. A forensic analysis confirmed the attacker found a legacy web server that had not been used in over a year and was not regularly patched. After a discussion with the security team, management decided to initiate a program of network reconnaissance and penetration testing. They want to start the process by scanning the network for active hosts and open ports. Which of the following tools is BEST suited for this job?
A. Ping
B. Nmap
C. Netstat
D. ifconfig
E. Wireshark
F. L0phtCrack
-
Question 378:
A staff member reported that a laptop has degraded performance. The security analyst has investigated the issue and discovered that CPU utilization, memory utilization, and outbound network traffic are consuming the laptop's resources. Which of the following is the BEST course of actions to resolve the problem?
A. Identify and remove malicious processes.
B. Disable scheduled tasks.
C. Suspend virus scan.
D. Increase laptop memory.
E. Ensure the laptop OS is properly patched.
-
Question 379:
A security analyst has discovered that an outbound SFTP process is occurring at the same time of day for the past several days. At the time this was discovered, large amounts of business critical data were delivered. The authentication for this process occurred using a service account with proper credentials. The security analyst investigated the destination IP for this transfer and discovered that this new process is not documented in the change management log. Which of the following would be the BEST course of action for the analyst to take?
A. Investigate a potential incident.
B. Verify user permissions.
C. Run a vulnerability scan.
D. Verify SLA with cloud provider.
-
Question 380:
A company has implemented WPA2, a 20-character minimum for the WiFi passphrase, and a new WiFi passphrase every 30 days, and has disabled SSID broadcast on all wireless access points. Which of the following is the company trying to mitigate?
A. Downgrade attacks
B. Rainbow tables
C. SSL pinning
D. Forced deauthentication
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.