Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 361:
A security analyst notices PII has been copied from the customer database to an anonymous FTP server in the DMZ. Firewall logs indicate the customer database has not been accessed from anonymous FTP server. Which of the following departments should make a decision about pursuing further investigation? (Choose two.)
A. Human resources
B. Public relations
C. Legal
D. Executive management
E. IT management
-
Question 362:
A security analyst received several service tickets reporting that a company storefront website is not accessible by internal domain users. However, external users are accessing the website without issue. Which of the following is the MOST likely reason for this behavior?
A. The FQDN is incorrect.
B. The DNS server is corrupted.
C. The time synchronization server is corrupted.
D. The certificate is expired.
-
Question 363:
A security analyst is creating ACLs on a perimeter firewall that will deny inbound packets that are from internal addresses, reversed external addresses, and multicast addresses. Which of the following is the analyst attempting to prevent?
A. Broadcast storms
B. Spoofing attacks
C. DDoS attacks
D. Man-in-the-middle attacks
-
Question 364:
A server contains baseline images that are deployed to sensitive workstations on a regular basis. The images are evaluated once per month for patching and other fixes, but do not change otherwise. Which of the following controls should be put in place to secure the file server and ensure the images are not changed?
A. Install and configure a file integrity monitoring tool on the server and allow updates to the images each month.
B. Schedule vulnerability scans of the server at least once per month before the images are updated.
C. Require the use of two-factor authentication for any administrator or user who needs to connect to the server.
D. Install a honeypot to identify any attacks before the baseline images can be compromised.
-
Question 365:
Organizational policies require vulnerability remediation on severity 7 or greater within one week. Anything with a severity less than 7 must be remediated within 30 days. The organization also requires security teams to investigate the details of a vulnerability before performing any remediation. If the investigation determines the finding is a false positive, no remediation is performed and the vulnerability scanner configuration is updates to omit the false positive from future scans:
The organization has three Apache web servers:

The results of a recent vulnerability scan are shown below:
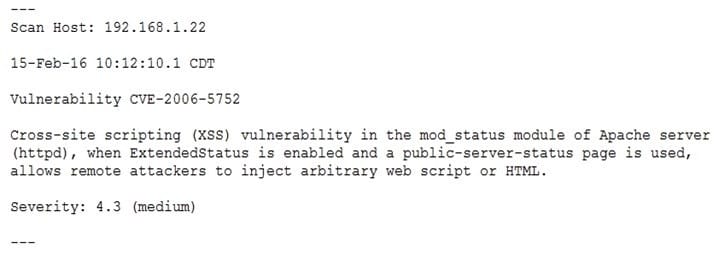
The team performs some investigation and finds a statement from Apache:
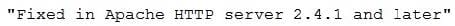
Which of the following actions should the security team perform?
A. Ignore the false positive on 192.168.1.22
B. Remediate 192.168.1.20 within 30 days
C. Remediate 192.168.1.22 within 30 days
D. Investigate the false negative on 192.168.1.20
-
Question 366:
The Chief Security Officer (CSO) has requested a vulnerability report of systems on the domain, identifying those running outdated OSs. The automated scan reports are not displaying OS version details, so the CSO cannot determine risk exposure levels from vulnerable systems. Which of the following should the cybersecurity analyst do to enumerate OS information as part of the vulnerability scanning process in the MOST efficient manner?
A. Execute the ver command
B. Execute the nmap -p command
C. Use Wireshark to export a list D. Use credentialed configuration
-
Question 367:
Which of the following could be directly impacted by an unpatched vulnerability in vSphere ESXi?
A. The organization's physical routers
B. The organization's mobile devices
C. The organization's virtual infrastructure
D. The organization's VPN
-
Question 368:
A security analyst performed a review of an organization's software development life cycle. The analyst reports that the life cycle does not contain in a phase in which team members evaluate and provide critical feedback on another developer's code. Which of the following assessment techniques is BEST for describing the analyst's report?
A. Architectural evaluation
B. Waterfall
C. Whitebox testing
D. Peer review
-
Question 369:
A newly discovered malware has a known behavior of connecting outbound to an external destination on port 27500 for the purposes of exfiltrating data. The following are four snippets taken from running netstat n on separate Windows workstations:
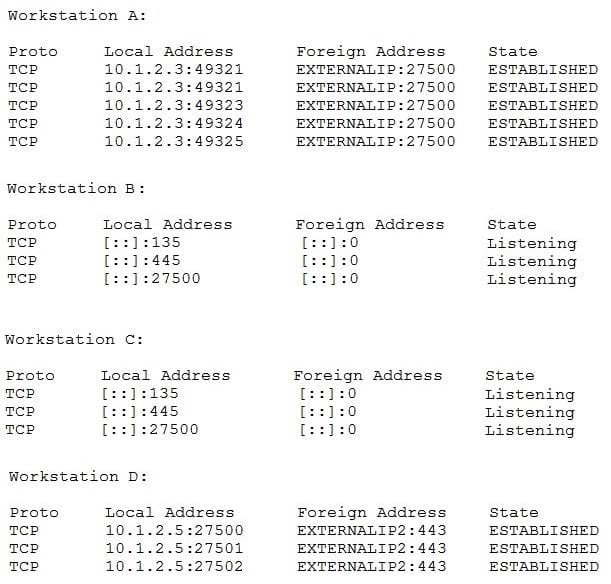
Based on the above information, which of the following is MOST likely to be exposed to this malware?
A. Workstation A
B. Workstation B
C. Workstation C
D. Workstation D
-
Question 370:
An insurance company employs quick-response team drivers that carry corporate-issued mobile devices with the insurance company's app installed on them. Devices are configuration-hardened by an MDM and kept up to date. The employees use the app to collect insurance claim information and process payments. Recently, a number of customers have filed complaints of credit card fraud against the insurance company, which occurred shortly after their payments were processed via the mobile app. The cyber-incident response team has been asked to investigate. Which of the following is MOST likely the cause?
A. The MDM server is misconfigured.
B. The app does not employ TLS.
C. USB tethering is enabled.
D. 3G and less secure cellular technologies are not restricted.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.