Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 401:
A security analyst at a small regional bank has received an alert that nation states are attempting to infiltrate financial institutions via phishing campaigns. Which of the following techniques should the analyst recommend as a proactive measure to defend against this type of threat?
A. Honeypot
B. Location-based NAC
C. System isolation
D. Mandatory access control
E. Bastion host
-
Question 402:
A security analyst is concerned that unauthorized users can access confidential data stored in the production server environment. All workstations on a particular network segment have full access to any server in production. Which of the following should be deployed in the production environment to prevent unauthorized access? (Choose two.)
A. DLP system
B. Honeypot
C. Jump box
D. IPS
E. Firewall
-
Question 403:
A cybersecurity professional wants to determine if a web server is running on a remote host with the IP address 192.168.1.100. Which of the following can be used to perform this task?
A. nc 192.168.1.100 -1 80
B. ps aux 192.168.1.100
C. nmap 192.168.1.100 -p 80 -A
D. dig www 192.168.1.100
E. ping -p 80 192.168.1.100
-
Question 404:
Weeks before a proposed merger is scheduled for completion, a security analyst has noticed unusual traffic patterns on a file server that contains financial information. Routine scans are not detecting the signature of any known exploits or malware. The following entry is seen in the ftp server logs:
tftp -I 10.1.1.1 GET fourthquarterreport.xls
Which of the following is the BEST course of action?
A. Continue to monitor the situation using tools to scan for known exploits.
B. Implement an ACL on the perimeter firewall to prevent data exfiltration.
C. Follow the incident response procedure associate with the loss of business critical data.
D. Determine if any credit card information is contained on the server containing the financials.
-
Question 405:
A retail corporation with widely distributed store locations and IP space must meet PCI requirements relating to vulnerability scanning. The organization plans to outsource this function to a third party to reduce costs.
Which of the following should be used to communicate expectations related to the execution of scans?
A. Vulnerability assessment report
B. Lessons learned documentation
C. SLA
D. MOU
-
Question 406:
The Chief Information Security Officer (CISO) asked for a topology discovery to be conducted and verified against the asset inventory. The discovery is failing and not providing reliable or complete data. The syslog shows the following information:
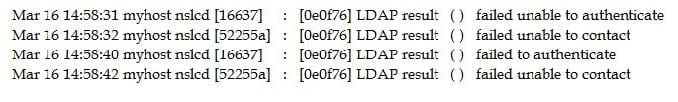
Which of the following describes the reason why the discovery is failing?
A. The scanning tool lacks valid LDAP credentials.
B. The scan is returning LDAP error code 52255a.
C. The server running LDAP has antivirus deployed.
D. The connection to the LDAP server is timing out.
E. The LDAP server is configured on the wrong port.
-
Question 407:
The primary difference in concern between remediating identified vulnerabilities found in general-purpose IT network servers and that of SCADA systems is that:
A. change and configuration management processes do not address SCADA systems.
B. doing so has a greater chance of causing operational impact in SCADA systems.
C. SCADA systems cannot be rebooted to have changes to take effect.
D. patch installation on SCADA systems cannot be verified.
-
Question 408:
A Linux-based file encryption malware was recently discovered in the wild. Prior to running the malware on a preconfigured sandbox to analyze its behavior, a security professional executes the following command:
umount -a -t cifs,nfs
Which of the following is the main reason for executing the above command?
A. To ensure the malware is memory bound.
B. To limit the malware's reach to the local host.
C. To back up critical files across the network
D. To test if the malware affects remote systems
-
Question 409:
A systems administrator is trying to secure a critical system. The administrator has placed the system behind a firewall, enabled strong authentication, and required all administrators of this system to attend mandatory training.
Which of the following BEST describes the control being implemented?
A. Audit remediation
B. Defense in depth
C. Access control
D. Multifactor authentication
-
Question 410:
Scan results identify critical Apache vulnerabilities on a company's web servers. A security analyst believes many of these results are false positives because the web environment mostly consists of Windows servers.
Which of the following is the BEST method of verifying the scan results?
A. Run a service discovery scan on the identified servers.
B. Refer to the identified servers in the asset inventory.
C. Perform a top-ports scan against the identified servers.
D. Review logs of each host in the SIEM.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.