Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 411:
A company has received the results of an external vulnerability scan from its approved scanning vendor. The company is required to remediate these vulnerabilities for clients within 72 hours of acknowledgement of the scan results.
Which of the following contract breaches would result if this remediation is not provided for clients within the time frame?
A. Service level agreement
B. Regulatory compliance
C. Memorandum of understanding
D. Organizational governance
-
Question 412:
A zero-day crypto-worm is quickly spreading through the internal network on port 25 and exploiting a software vulnerability found within the email servers.
Which of the following countermeasures needs to be implemented as soon as possible to mitigate the worm from continuing to spread?
A. Implement a traffic sinkhole.
B. Block all known port/services.
C. Isolate impacted servers.
D. Patch affected systems.
-
Question 413:
A Chief Information Security Officer (CISO) wants to standardize the company's security program so it can be objectively assessed as part of an upcoming audit requested by management.
Which of the following would holistically assist in this effort?
A. ITIL
B. NIST
C. Scrum
D. AUP
E. Nessus
-
Question 414:
A cybersecurity analyst was hired to resolve a security issue within a company after it was reported that many employee account passwords had been compromised. Upon investigating the incident, the cybersecurity analyst found that a brute
force attack was launched against the company.
Which of the following remediation actions should the cybersecurity analyst recommend to senior management to address these security issues?
A. Prohibit password reuse using a GPO.
B. Deploy multifactor authentication.
C. Require security awareness training.
D. Implement DLP solution.
-
Question 415:
An investigation showed a worm was introduced from an engineer's laptop. It was determined the company does not provide engineers with company-owned laptops, which would be subject to company policy and technical controls.
Which of the following would be the MOST secure control implement?
A. Deploy HIDS on all engineer-provided laptops, and put a new router in the management network.
B. Implement role-based group policies on the management network for client access.
C. Utilize a jump box that is only allowed to connect to clients from the management network.
D. Deploy a company-wide approved engineering workstation for management access.
-
Question 416:
An analyst has noticed unusual activities in the SIEM to a .cn domain name. Which of the following should the analyst use to identify the content of the traffic?
A. Log review
B. Service discovery
C. Packet capture
D. DNS harvesting
-
Question 417:
A cybersecurity analyst is conducting packet analysis on the following:
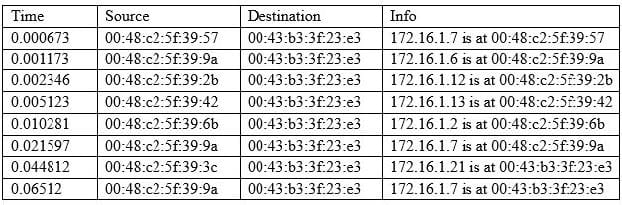
Which of the following is occurring in the given packet capture?
A. ARP spoofing
B. Broadcast storm
C. Smurf attack
D. Network enumeration
E. Zero-day exploit
-
Question 418:
A malware infection spread to numerous workstations within the marketing department. The workstations were quarantined and replaced with machines.
Which of the following represents a FINAL step in the eradication of the malware?
A. The workstations should be isolated from the network.
B. The workstations should be donated for reuse.
C. The workstations should be reimaged.
D. The workstations should be patched and scanned.
-
Question 419:
Which of the following systems would be at the GREATEST risk of compromise if found to have an open vulnerability associated with perfect forward secrecy?
A. Endpoints
B. VPN concentrators
C. Virtual hosts
D. SIEM
E. Layer 2 switches
-
Question 420:
A pharmacy gives its clients online access to their records and the ability to review bills and make payments. A new SSL vulnerability on a special platform was discovered, allowing an attacker to capture the data between the end user and
the web server providing these services. After investigating the platform vulnerability, it was determined that the web services provided are being impacted by this new threat.
Which of the following data types are MOST likely at risk of exposure based on this new threat? (Choose two.)
A. Cardholder data
B. Intellectual property
C. Personal health information
D. Employee records
E. Corporate financial data
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.