Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 571:
A security analyst received a compromised workstation. The workstation's hard drive may contain evidence of criminal activities. Which of the following is the FIRST thing the analyst must do to ensure the integrity of the hard drive while performing the analysis?
A. Make a copy of the hard drive.
B. Use write blockers.
C. Run rm -R command to create a hash.
D. Install it on a different machine and explore the content.
-
Question 572:
Which of the following best practices is used to identify areas in the network that may be vulnerable to penetration testing from known external sources?
A. Blue team training exercises
B. Technical control reviews
C. White team training exercises
D. Operational control reviews
-
Question 573:
Which of the following BEST describes the offensive participants in a tabletop exercise?
A. Red team
B. Blue team
C. System administrators
D. Security analysts
E. Operations team
-
Question 574:
After analyzing and correlating activity from multiple sensors, the security analyst has determined a group from a high-risk country is responsible for a sophisticated breach of the company network and continuous administration of targeted attacks for the past three months. Until now, the attacks went unnoticed. This is an example of:
A. privilege escalation.
B. advanced persistent threat.
C. malicious insider threat.
D. spear phishing.
-
Question 575:
A system administrator who was using an account with elevated privileges deleted a large amount of log files generated by a virtual hypervisor in order to free up disk space. These log files are needed by the security team to analyze the health of the virtual machines. Which of the following compensating controls would help prevent this from reoccurring? (Select two.)
A. Succession planning
B. Separation of duties
C. Mandatory vacation
D. Personnel training
E. Job rotation
-
Question 576:
A security analyst is reviewing port scan data that was collected over the course of several months. The following data represents the trends:
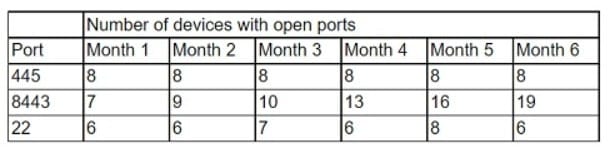
Which of the following is the BEST action for the security analyst to take after analyzing the trends?
A. Review the system configurations to determine if port 445 needs to be open.
B. Assume there are new instances of Apache in the environment.
C. Investigate why the number of open SSH ports varied during the six months.
D. Raise a concern to a supervisor regarding possible malicious use Of port 8443.
-
Question 577:
A systems administrator believes a user's workstation has been compromised. The workstation's performance has been lagging significantly for the past several hours. The administrator runs the task list
/ v command and receives the following output:
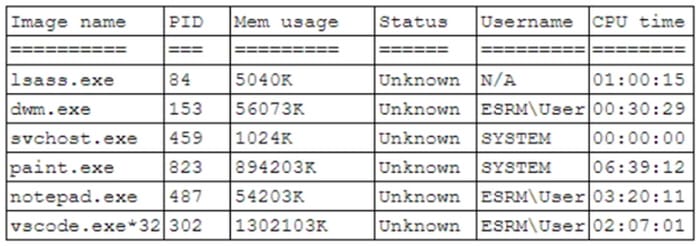
Which of the following should a security analyst recognize as an indicator of compromise?
A. dwm.exe being executed under the user context
B. The high usage of vscode. exe * 32
C. The abnormal behavior of paint.exe
D. svchost.exe being executed as SYSTEM
-
Question 578:
Ensuring that all areas of security have the proper controls is a primary reason why organizations use:
A. frameworks.
B. directors and officers.
C. incident response plans.
D. engineering rigor.
-
Question 579:
An email analysis system notifies a security analyst that the following message was quarantined and requires further review.
From: [email protected]
Subject: [EXTERNAL] Gift card purchase ASAP
Body:
Please purchase gift cards to any major electronics store and reply with pictures of them to this email!
Which of the following actions should the security analyst take?
A. Release the email for delivery due to its importance
B. Immediately contact a purchasing agent to expedite.
C. Delete the email and block the sender.
D. Purchase the gift cards and submit an expense report.
-
Question 580:
Which ol the following provides an automated approach 10 checking a system configuration?
A. SCAP
B. CI/CD
C. OVAL
D. Scripting
E. SOAR
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.