Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 591:
A company experienced a security compromise due to the inappropriate disposal of one of its hardware appliances. Sensitive information stored on the hardware appliance was not removed prior to disposal.
Which of the following is the BEST manner in which to dispose of the hardware appliance?
A. Ensure the hardware appliance has the ability to encrypt the data before disposing of it.
B. Dispose of all hardware appliances securely, thoroughly, and in compliance with company policies.
C. Return the hardware appliance to the vendor, as the vendor is responsible for disposal.
D. Establish guidelines for the handling of sensitive information.
-
Question 592:
A security analyst is reviewing WAF logs and notes requests against the corporate website are increasing and starting to impact the performance of the web server. The security analyst queries the logs for requests that triggered an alert on the WAF but were not blocked.
Which of the following possible TTP combinations might warrant further investigation? (Select TWO).
A. Requests identified by a threat intelligence service with a bad reputation
B. Requests sent from the same IP address using different user agents
C. Requests blocked by the web server per the input sanitization
D. Failed log-in attempts against the web application
E. Requests sent by NICs with outdated firmware
F. Existence of HTTP/501 status codes generated to the same IP address
-
Question 593:
Which of the following can detect vulnerable third-party libraries before code deployment?
A. Impact analysis
B. Dynamic analysis
C. Static analysis
D. Protocol analysis
-
Question 594:
A company employee downloads an application from the internet. After the installation, the employee begins experiencing noticeable performance issues, and files are appearing on the desktop.
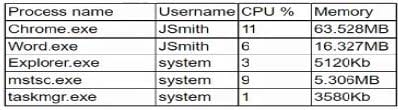
Which of the following processes will the security analyst Identify as the MOST likely indicator of system compromise given the processes running in Task Manager?
A. Chrome.exe
B. Word.exe
C. Explorer.exe
D. mstsc.exe
E. taskmgr.exe
-
Question 595:
During an Incident, it Is determined that a customer database containing email addresses, first names, and last names was exfiltrated. Which ot the following should the security analyst do NEXT?
A. Consult with the legal department for regulatory impact.
B. Encrypt the database with available tools.
C. Email the customers to inform them of the breach.
D. Follow the incident communications process.
-
Question 596:
The security team decides to meet informally to discuss and test the response plan for potential security breaches and emergency situations. Which of the following types of training will the security team perform?
A. Tabletop exercise
B. Red-team attack
C. System assessment implementation
D. Blue-team training
E. White-team engagement
-
Question 597:
An organization's Cruel Information Security Officer is concerned the proper control are not in place to identify a malicious insider.
Which of the following techniques would be BEST to identify employees who attempt to steal data or do harm to the organization?
A. Place a text file named Passwords txt on the local file server and create a SIEM alert when the file is accessed
B. Segment the network so workstations are segregated from servers and implement detailed logging on the jumpbox
C. Perform a review of all users with privileged access and monitor web activity logs from the organization's pfoxy
D. Analyze logs to determine if a user is consuming large amounts of bandwidth at odd hours ol the day
-
Question 598:
An organization has the following policies:
1.
Services must run on standard ports.
2.
Unneeded services must be disabled.
The organization has the following servers:
192.168.10.1 - web server
192.168.10.2 - database server
A security analyst runs a scan on the servers and sees the following output:
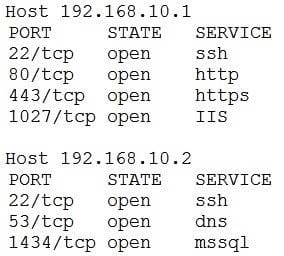
Which of the following actions should the analyst take?
A. Disable HTTPS on 192.168.10.1.
B. Disable IIS on 192.168.10.1.
C. Disable DNS on 192.168.10.2.
D. Disable MSSQL on 192.168.10.2.
E. Disable SSH on both servers.
-
Question 599:
Forming a hypothesis, looking for indicators of compromise, and using the findings to proactively improve detection capabilities are examples of the value of:
A. vulnerability scanning.
B. threat hunting.
C. red learning.
D. penetration testing.
-
Question 600:
During a review of the vulnerability scan results on a server, an information security analyst notices the following:
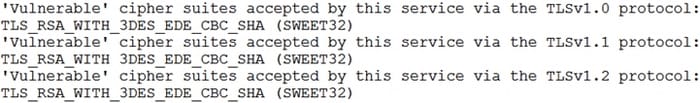
The MOST appropriate action for the analyst to recommend to developers is to change the web server so:
A. It only accepts TLSvl 2
B. It only accepts cipher suites using AES and SHA
C. It no longer accepts the vulnerable cipher suites
D. SSL/TLS is offloaded to a WAF and load balancer
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.