Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 601:
During a routine review of service restarts a security analyst observes the following in a server log:
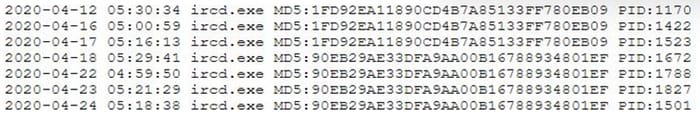
Which of the following is the GREATEST security concern?
A. The daemon's binary was AChanged
B. Four consecutive days of monitoring are skipped in the tog
C. The process identifiers for the running service change
D. The PIDs are continuously changing
-
Question 602:
When investigating a report of a system compromise, a security analyst views the following /var/log/secure log file:
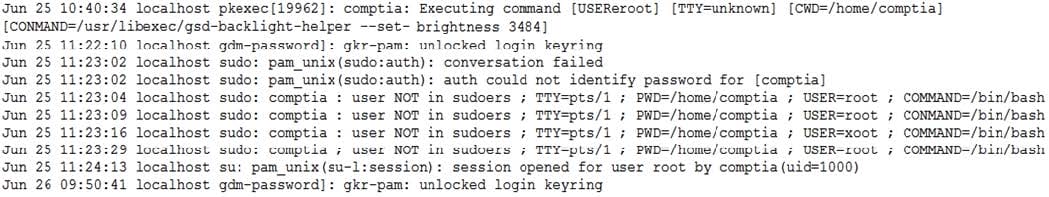
Which of the following can the analyst conclude from viewing the log file?
A. The comptia user knows the sudo password.
B. The comptia user executed the sudo su command.
C. The comptia user knows the root password.
D. The comptia user added himself or herself to the /etc/sudoers file.
-
Question 603:
During an audit several customer order forms were found to contain inconsistencies between the actual price of an item and the amount charged to the customer Further investigation narrowed the cause of the issue to manipulation of the public-facing web form used by customers to order products.
Which of the following would be the BEST way to locate this issue?
A. Reduce the session timeout threshold
B. Deploy MFA for access to the web server
C. Implement input validation
D. Run a static code scan
-
Question 604:
A security team has begun updating the risk management plan, incident response plan, and system security plan to ensure compliance with security review guidelines. Which of the following can be executed by internal managers to simulate and validate the proposed changes?
A. Internal management review
B. Control assessment
C. Tabletop exercise
D. Peer review
-
Question 605:
When of the following techniques can be implemented to safeguard the confidentiality of sensitive information while allowing limited access to authorized individuals?
A. Deidentification
B. Hashing
C. Masking
D. Salting
-
Question 606:
A cybersecurity analyst routinely checks logs, querying for login attempts. While querying for unsuccessful login attempts during a five-day period, the analyst produces the following report:
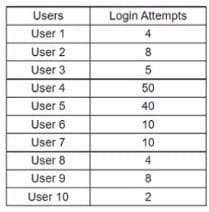
Which of the following BEST describes what the analyst Just found?
A. Users 4 and 5 are using their credentials to transfer files to multiple servers.
B. Users 4 and 5 are using their credentials to run an unauthorized scheduled task targeting some servers In the cloud.
C. An unauthorized user is using login credentials in a script.
D. A bot is running a brute-force attack in an attempt to log in to the domain.
-
Question 607:
A product security analyst has been assigned to evaluate and validate a new products security capabilities Part ot the evaluation involves reviewing design changes at specific intervals tor security deficiencies recommending changes and checking for changes at the next checkpoint.
Which of the following BEST defines the activity being conducted?
A. User acceptance testing
B. Stress testing
C. Code review
D. Security regression testing
-
Question 608:
A new vanant of malware is spreading on ihe company network using TCP 443 to contact its command- and-control server The domain name used for callback continues to change, and the analyst is unable to predict future domain name variance.
Which of the following actions should the analyst take to stop malicious communications with the LEAST disruption to service?
A. Implement a sinkhole with a high entropy level
B. Disable TCP/53 at the penmeter firewall
C. Block TCP/443 at the edge router
D. Configure the DNS forwarders to use recursion
-
Question 609:
Due to continued support of legacy applications, an organization's enterprise password complexity rules are inadequate for its required security posture. Which of the following is the BEST compensating control to help reduce authentication compromises?
A. Smart cards
B. Multifactor authentication
C. Biometrics
D. Increased password-rotation frequency
-
Question 610:
A security analyst observes a large amount of scanning activity coming from an IP address outside the organization's environment. Which of the following should the analyst do to block this activity?
A. Create an IPS rule to block the subnet.
B. Sinkhole the IP address.
C. Create a firewall rule to block the IP address.
D. Close all unnecessary open ports.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.