Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 641:
An organization has the following policy statements:
1.
AlI emails entering or leaving the organization will be subject to inspection for malware, policy violations, and unauthorized coolant.
2.
AM network activity will be logged and monitored.
3.
Confidential data will be tagged and tracked
4.
Confidential data must never be transmitted in an unencrypted form. Confidential data must never be stored on an unencrypted mobile device.
Which of the following is the organization enforcing?
A. Acceptable use policy
B. Data privacy policy
C. Encryption policy
D. Data management, policy
-
Question 642:
Due to a nse m cyberattackers seeking PHI, a healthcare company that collects highly sensitive data from millions of customers is deploying a solution that will ensure the customers' data is protected by the organization internally and externally.
Which of the following countermeasures can BEST prevent the loss of customers' sensitive data?
A. Implement privileged access management
B. Implement a nsk management process
C. Implement multifactor authentication
D. Add more security resources to the environment
-
Question 643:
During a review of recent network traffic, an analyst realizes the team has seen this same traffic multiple times in the past three weeks, and it resulted in confirmed malware activity The analyst also notes there is no other alert in place for this traffic After resolving the security incident, which of the following would be the BEST action for the analyst to take to increase the chance of detecting this traffic in the future?
A. Share details of the security incident with the organization's human resources management team
B. Note the secunty incident so other analysts are aware the traffic is malicious
C. Communicate the secunty incident to the threat team for further review and analysis
D. Report the security incident to a manager for inclusion in the daily report
-
Question 644:
The Chief Information Security Officer (CISO) of a large financial institution is seeking a solution that will block a predetermined set of data points from being transferred or downloaded by employees. The CISO also wants to track the data assets by name, type, content, or data profile.
Which of the following BEST describes what the CIS wants to purchase?
A. Asset tagging
B. SIEM
C. File integrity monitor
D. DLP
-
Question 645:
Which of the following types of controls defines placing an ACL on a file folder?
A. Technical control
B. Confidentiality control
C. Managerial control
D. Operational control
-
Question 646:
A forensics investigator is analyzing a compromised workstation. The investigator has cloned the hard drive and needs to verify that a bit-level image copy of a hard drive is an exact clone of the original hard drive that was collected as evidence. Which of the following should the investigator do?
A. Insert the hard drive on a test computer and boot the computer.
B. Record the serial numbers of both hard drives.
C. Compare the file-directory "sting of both hard drives.
D. Run a hash against the source and the destination.
-
Question 647:
A security analyst notices the following entry while reviewing the server togs
OR 1=1' ADD USER attacker' PW 1337password' ---
Which of the following events occurred?
A. CSRF
B. XSS
C. SQLi
D. RCE
-
Question 648:
A company has alerted planning the implemented a vulnerability management procedure. However, to security maturity level is low, so there are some prerequisites to complete before risk calculation and prioritization. Which of the following should be completed FIRST?
A. A business Impact analysis
B. A system assessment
C. Communication of the risk factors
D. A risk identification process
-
Question 649:
A security analyst is correlating, ranking, and enriching raw data into a report that will be interpreted by humans or machines to draw conclusions and create actionable recommendations.
Which of the following steps in the intelligence cycle is the security analyst performing?
A. Analysis and production
B. Processing and exploitation
C. Dissemination and evaluation
D. Data collection
E. Planning and direction
-
Question 650:
An organization has the following risk mitigation policies
Risks without compensating controls will be mitigated first if the risk value is greater than $50,000.
Other risk mitigation will be prioritized based on risk value.
The following risks have been identified:
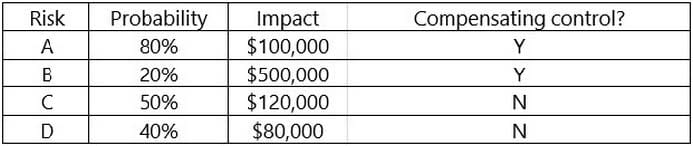
Which of the following is the order of priority for risk mitigation from highest to lowest?
A. A, C, D, B
B. B, C, D, A
C. C, B, A, D
D. C. D, A, B
E. D, C, B, A
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.