Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 651:
A company's security team recently discovered a number of workstations that are at the end of life. The workstation vendor informs the team that the product is no longer supported and patches are no longer available The company is not prepared to cease its use of these workstations.
Which of the following would be the BEST method to protect these workstations from threats?
A. Deploy whitelisting to the identified workstations to limit the attack surface
B. Determine the system process cntcalrty and document it
C. Isolate the workstations and air gap them when it is feasible
D. Increase security monitoring on the workstations
-
Question 652:
Forming a hypothesis, looking for indicators of compromise, and using the findings to proactively improve detection capabilities are examples of the value of:
A. vulnerability scanning.
B. threat hunting.
C. red learning.
D. penetration testing.
-
Question 653:
Which of the following is MOST important when developing a threat hunting program?
A. Understanding penetration testing techniques
B. Understanding how to build correlation rules within a SIEM
C. Understanding security software technologies
D. Understanding assets and categories of assets
-
Question 654:
A security analyst is reviewing the following server statistics:
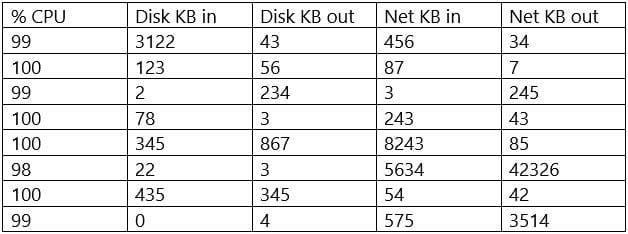
Which of the following Is MOST likely occurring?
A. Race condition
B. Privilege escalation
C. Resource exhaustion
D. VM escape
-
Question 655:
An incident response team detected malicious software that could have gained access to credit card data. The incident response team was able to mitigate significant damage and implement corrective actions. By having incident response mechanisms in place. Which of the following should be notified for lessons learned?
A. The human resources department
B. Customers
C. Company leadership
D. The legal team
-
Question 656:
An organization wants to ensure the privacy of the data that is on its systems Full disk encryption and DLP are already in use. Which of the following is the BEST option?
A. Require all remote employees to sign an NDA
B. Enforce geofencmg to limit data accessibility
C. Require users to change their passwords more frequently
D. Update the AUP to restrict data sharing
-
Question 657:
A security analyst is investigate an no client related to an alert from the threat detection platform on a host (10.0 1.25) in a staging environment that could be running a cryptomining tool because it in sending traffic to an IP address that are related to Bitcoin.
The network rules for the instance are the following:
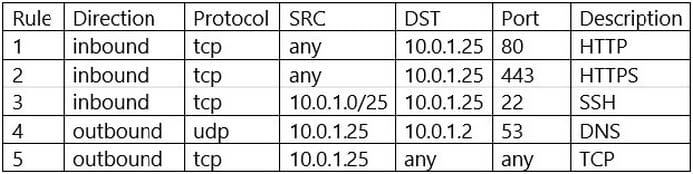
Which of the following is the BEST way to isolate and triage the host?
A. Remove rules 1.2. and 3.
B. Remove rules 1.2. 4. and 5.
C. Remove rules 1.2. 3.4. and 5.
D. Remove rules 1.2. and 5.
E. Remove rules 1.4. and 5.
F. Remove rules 4 and 5
-
Question 658:
The majority of a company's employees have stated they are unable to perform their job duties due to outdated workstations, so the company has decided to institute BYOD. Which of the following would a security analyst MOST likely recommend for securing the proposed solution?
A. A Linux-based system and mandatory training on Linux for all BYOD users
B. A firewalled environment for client devices and a secure VDl for BYOO users
C. A standardized anti-malware platform and a unified operating system vendor
D. 802.1X lo enforce company policy on BYOD user hardware
-
Question 659:
A software developer is correcting the error-handling capabilities of an application following the initial coding of the fix. Which of the following would the software developer MOST likely performed to validate the code poor to pushing it to production?
A. Web-application vulnerability scan
B. Static analysis
C. Packet inspection
D. Penetration test
-
Question 660:
Which of the following attack techniques has the GREATEST likelihood of quick success against Modbus assets?
A. Remote code execution
B. Buffer overflow
C. Unauthenticated commands
D. Certificate spoofing
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.