Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 701:
A security analyst is reviewing the following server statistics:
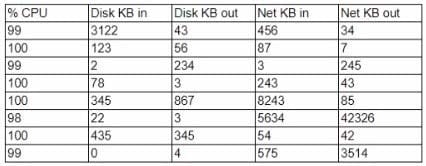
Which of the following is MOST likely occurring?
A. Race condition
B. Privilege escalation
C. Resource exhaustion
D. VM escape
-
Question 702:
A security analyst is reviewing the following Internet usage trend report:
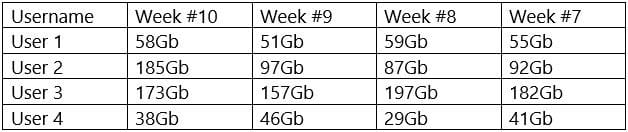
Which of the following usernames should the security analyst investigate further?
A. User1
B. User 2
C. User 3
D. User 4
-
Question 703:
An organization is experiencing security incidents in which a systems administrator is creating unauthorized user accounts. A security analyst has created a script to snapshot the system configuration each day.
Following is one of the scripts: cat /etc/passwd > daily_$(date +"%m_%d_%Y")
This script has been running successfully every day. Which of the following commands would provide the analyst with additional useful information relevant to the above script?
A. diff daily_11_03_2019 daily_11_04_2019
B. ps -ef | grep admin > daily_process_$(date +%m_%d_%Y")
C. more /etc/passwd > daily_$(date +%m_%d_%Y_%H:%M:%S")
D. la -lai /usr/sbin > daily_applications
-
Question 704:
Which of the following factors would determine the regulations placed on data under data sovereignty laws?
A. What the company intends to do with the data it owns
B. The company's data security policy
C. The type of data the company stores
D. The data laws of the country in which the company is located
-
Question 705:
An analyst is responding 10 an incident involving an attack on a company-owned mobile device that was being used by an employee to collect data from clients in the held. Maiware was loaded on the device via the installation of a third-party software package The analyst has baselined the device.
Which of the following should the analyst do to BEST mitigate future attacks?
A. Implement MDM
B. Update the maiware catalog
C. Patch the mobile device's OS
D. Block third-party applications
-
Question 706:
Which of the following BEST explains the function of a managerial control?
A. To help design and implement the security planning, program development, and maintenance of the security life cycle
B. To guide the development of training, education, security awareness programs, and system maintenance
C. To create data classification, risk assessments, security control reviews, and contingency planning
D. To ensure tactical design, selection of technology to protect data, logical access reviews, and the implementation of audit trails
-
Question 707:
An online gaming company was impacted by a ransomware attack. An employee opened an attachment that was received via an SMS attack on a company-issue firewall. Which following actions would help during the forensic analysis of the mobile device? (Select TWO).
A. Resetting the phone to factory settings
B. Rebooting the phone and installing the latest security updates
C. Documenting the respective chain of custody
D. Uninstalling any potentially unwanted programs
E. Performing a memory dump of the mobile device for analysis
F. Unlocking the device by blowing the eFuse
-
Question 708:
An IT security analyst has received an email alert regarding vulnerability within the new fleet of vehicles the company recently purchased. Which of the following attack vectors is the vulnerability MOST likely targeting?
A. SCADA
B. CAN bus
C. Modbus
D. loT
-
Question 709:
A manufacturing company uses a third-party service provider for Tier 1 security support. One of the requirements is that the provider must only source talent from its own country due to geopolitical and national security interests. Which of the following can the manufacturing company implement to ensure the third-party service provider meets this requirement?
A. Implement a secure supply chain program with governance.
B. Implement blacklisting lor IP addresses from outside the county.
C. Implement strong authentication controls for at contractors.
D. Implement user behavior analytics tor key staff members.
-
Question 710:
A SIEM analyst receives an alert containing the following URL: http:/companywebsite.com/displayPicture?filenamE=../../../../etc/passwd Which of the following BEST describes the attack?
A. Password spraying
B. Buffer overflow
C. insecure object access
D. Directory traversal
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.