Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 831:
An organization has the following risk mitigation policies
Risks without compensating controls will be mitigated first it the nsk value is greater than $50,000 Other nsk mitigation will be pnontized based on risk value.
The following risks have been identified:
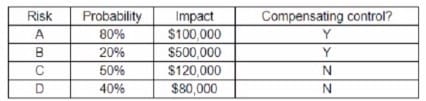
Which of the following is the ordei of priority for risk mitigation from highest to lowest?
A. A, C, D, B
B. B, C, D, A
C. C, B, A, D
D. C. D, A, B
E. D, C, B, A
-
Question 832:
Which of the following is the BEST option to protect a web application against CSRF attacks?
A. Update the web application to the latest version.
B. Set a server-side rate limit for CSRF token generation.
C. Avoid the transmission of CSRF tokens using cookies.
D. Configure the web application to only use HTTPS and TLS 1.3.
-
Question 833:
A security analyst responds to a series of events surrounding sporadic bandwidth consumption from an endpoint device. The security analyst then identifies the following additional details:
Bursts of network utilization occur approximately every seven days.
The content being transferred appears to be encrypted or obfuscated.
A separate but persistent outbound TCP connection from the host to infrastructure in a third-party cloud is in place.
The HDD utilization on the device grows by 10GB to 12GB over the course of every seven days.
Single file sizes are 10GB.
Which of the following describes the most likely cause of the issue?
A. Memory consumption
B. Non-standard port usage
C. Data exfiltration
D. System update
E. Botnet participant
-
Question 834:
A risk assessment concludes that the perimeter network has the highest potential for compromise by an attacker, and it is labeled as a critical risk environment. Which of the following is a valid compensating control to reduce the volume of valuable information in the perimeter network that an attacker could gain using active reconnaissance techniques?
A. A control that demonstrates that all systems authenticate using the approved authentication method
B. A control that demonstrates that access to a system is only allowed by using SSH
C. A control that demonstrates that firewall rules are peer reviewed for accuracy and approved before deployment
D. A control that demonstrates that the network security policy is reviewed and updated yearly
-
Question 835:
A technician working at company.com received the following email:
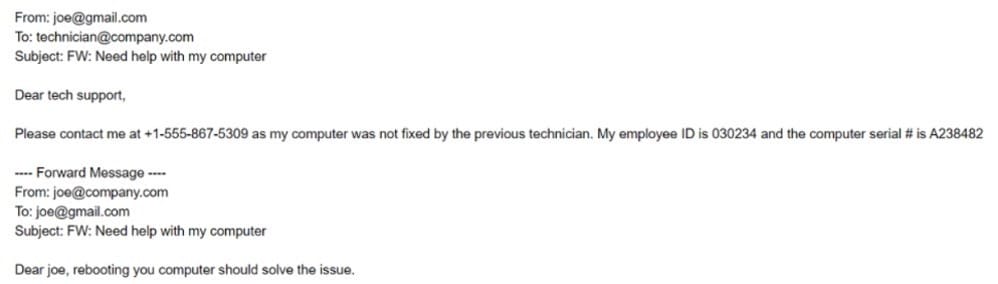
After looking at the above communication, which of the following should the technician recommend to the security team to prevent exposure of sensitive information and reduce the risk of corporate data being stored on non-corporate assets?
A. Forwarding of corporate email should be disallowed by the company.
B. A VPN should be used to allow technicians to troubleshoot computer issues securely.
C. An email banner should be implemented to identify emails coming from external sources.
D. A rule should be placed on the DLP to flag employee IDs and serial numbers.
-
Question 836:
Members of the sales team are using email to send sensitive client lists with contact information to their personal accounts The company's AUP and code of conduct prohibits this practice. Which of the following configuration changes would improve security and help prevent this from occurring?
A. Configure the DLP transport rules to provide deep content analysis.
B. Put employees' personal email accounts on the mail server on a blocklist.
C. Set up IPS to scan for outbound emails containing names and contact information.
D. Use Group Policy to prevent users from copying and pasting information into emails.
E. Move outbound emails containing names and contact information to a sandbox for further examination.
-
Question 837:
The following output is from a tcpdump al the edge of the corporate network:
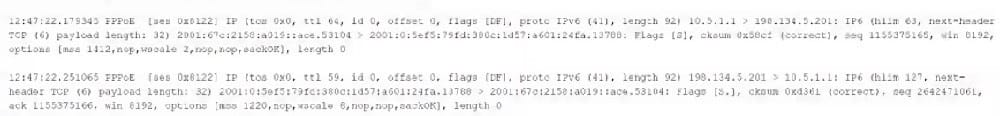
Which of the following best describes the potential security concern?
A. Payload lengths may be used to overflow buffers enabling code execution.
B. Encapsulated traffic may evade security monitoring and defenses
C. This traffic exhibits a reconnaissance technique to create network footprints.
D. The content of the traffic payload may permit VLAN hopping.
-
Question 838:
An organization wants to consolidate a number of security technologies throughout the organization and standardize a workflow for identifying security issues prioritizing the severity and automating a response.
Which of the following would best meet the organization's needs'?
A. MaaS
B. SIEM
C. SOAR
D. CI/CD
-
Question 839:
A forensic analyst is conducting an investigation on a compromised server. Which of the following should the analyst do first to preserve evidence?
A. Restore damaged data from the backup media
B. Create a system timeline
C. Monitor user access to compromised systems
D. Back up all log files and audit trails
-
Question 840:
A company is aiming to test a new incident response plan. The management team has made it clear that the initial test should have no impact on the environment. The company has limited resources to support testing. Which of the following exercises would be the best approach?
A. Tabletop scenarios
B. Capture the flag
C. Red team vs. blue team
D. Unknown-environment penetration test
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.