Exam Details
Exam Code
:EC0-349Exam Name
:Computer Hacking Forensic InvestigatorCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:304 Q&AsLast Updated
:Apr 13, 2025
EC-COUNCIL EC-COUNCIL Certifications EC0-349 Questions & Answers
-
Question 151:
Item 2If you come across a sheepdip machine at your client site, what would you infer?
A. A sheepdip coordinates several honeypots
B. A sheepdip computer is another name for a honeypot
C. A sheepdip computer is used only for virus-checking.
D. A sheepdip computer defers a denial of service attack
-
Question 152:
In a computer forensics investigation, what describes the route that evidence takes from the time you find it until the case is closed or goes to court?
A. rules of evidence
B. law of probability
C. chain of custody
D. policy of separation
-
Question 153:
How many characters long is the fixed-length MD5 algorithm checksum of a critical system file?
A. 128
B. 64
C. 32
D. 16
-
Question 154:
When reviewing web logs, you see an entry for resource not found in the HTTP status code field. What is the actual error code that you would see in the log for resource not found?
A. 202
B. 404
C. 606
D. 999
-
Question 155:
What stage of the incident handling process involves reporting events?
A. Containment
B. Follow-up
C. Identification
D. Recovery
-
Question 156:
While looking through the IIS log file of a web server, you find the following entries:
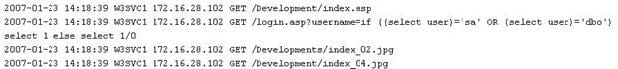
What is evident from this log file?
A. Web bugs
B. Cross site scripting
C. Hidden fields
D. SQL injection is possible
-
Question 157:
Why would you need to find out the gateway of a device when investigating a wireless attack?
A. The gateway will be the IP of the proxy server used by the attacker to launch the attack
B. The gateway will be the IP of the attacker computer
C. The gateway will be the IP used to manage the RADIUS server
D. The gateway will be the IP used to manage the access point
-
Question 158:
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd.
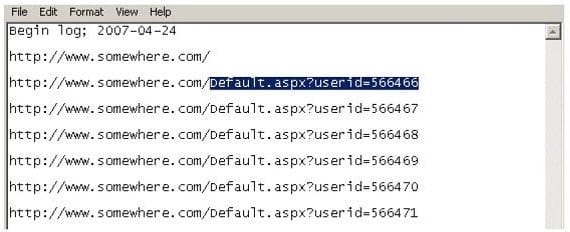
From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
A. Parameter tampering
B. Cross site scripting
C. SQL injection
D. Cookie Poisoning
-
Question 159:
Why would a company issue a dongle with the software they sell?
A. To provide source code protection
B. To provide wireless functionality with the software
C. To provide copyright protection
D. To ensure that keyloggers cannot be used
-
Question 160:
What feature of Windows is the following command trying to utilize?
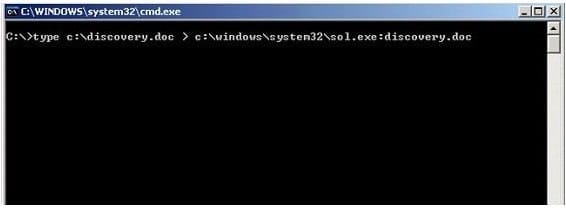
A. White space
B. AFS
C. ADS
D. Slack file
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your EC0-349 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.