Exam Details
Exam Code
:AZ-104Exam Name
:Microsoft Azure AdministratorCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:361 Q&AsLast Updated
:Apr 16, 2025
Microsoft Microsoft Certifications AZ-104 Questions & Answers
-
Question 361:
You have an Azure Active Directory (Azure AD) tenant named Contoso.com that is synced to an Active Directory domain. The tenant contains the users shown in the following table.
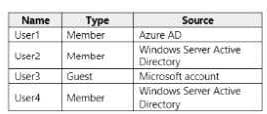
The user have the attributes shown in the following table.
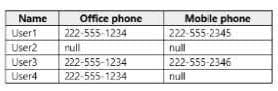
You need to ensure that you can enable Azure Multi-Factor Authentication (MFA) for all four users.
Solution: You create a new user account in Azure AD for User3.
Does this meet the goal?
A. Yes
B. No
-
Question 362:
You are deploying a containerized web application in Azure. When deploying the web app, which of the following are valid container image sources?
A. Virtual machine
B. Docker hub
C. ACR
D. On-premises
-
Question 363:
You have an Azure virtual machine named VM1.
The network interface for VM1 is configured as shown in the exhibit. (Click the Exhibit tab.)
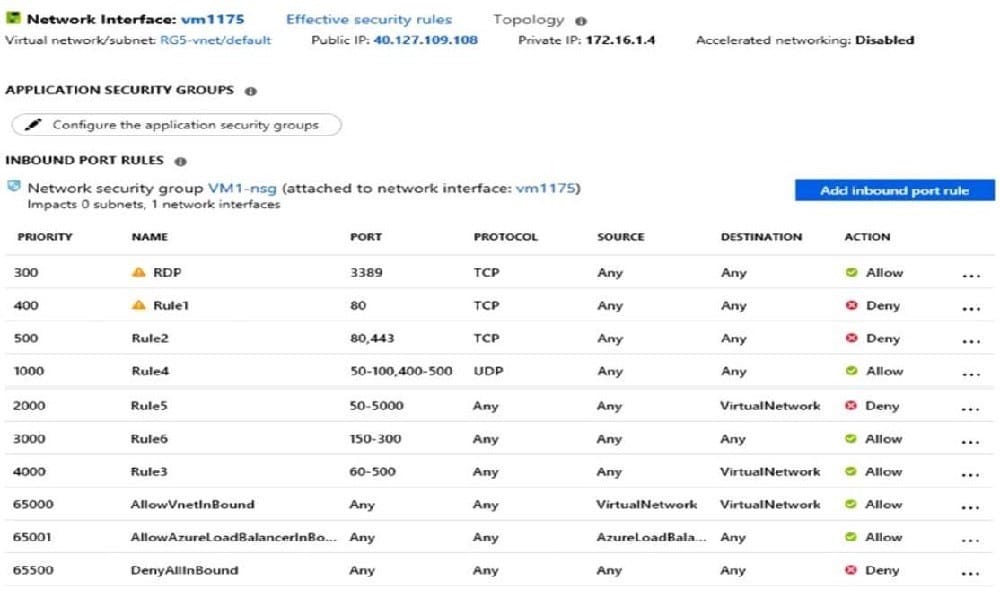
You deploy a web server on VM1, and then create a secure website that is accessible by using the HTTPS protocol. VM1 is used as a web server only.
You need to ensure that users can connect to the website from the internet. What should you do?
A. Create a new inbound rule that allows TCP protocol 443 and configure the protocol to have a priority of 501.
B. For Rule5, change the Action to Allow and change the priority to 401.
C. Delete Rule1.
D. Modify the protocol of Rule4.
-
Question 364:
Your VMware vSphere on-premises infrastructure hosts 600 virtual machines (VMs).
Your company is planning to move all of these VMs to Azure. You are asked to provide information about
the resources that will be needed in Azure to host all of the VMs.
All VMs hosted in your on-premise infrastructure are based on Windows Server 2012 R2 or newer and RedHat Enterprise Linux 7.0 or newer.
You conduct the initial migration assessment and get a message that some virtual machines are conditionally ready for Azure.
You need to find the cause of this message.
What are two reasons why are you might get this message on some VMs? (Choose two)
Each correct answer presents part of the solution.
A. The vCenter user does not have enough permissions on affected VMs.
B. The operating system is configured as Windows Server 2003 in vCenter Server.
C. The operating system is configured as Others in vCenter Server.
D. The VMs are configured with the BIOS boot type.
E. The VMs are configured with the UEFI boot type.
-
Question 365:
You have an Azure virtual machine named VMV
The network interface for VM1 is configured as shown in the exhibit(Click the Exhibit tab.)
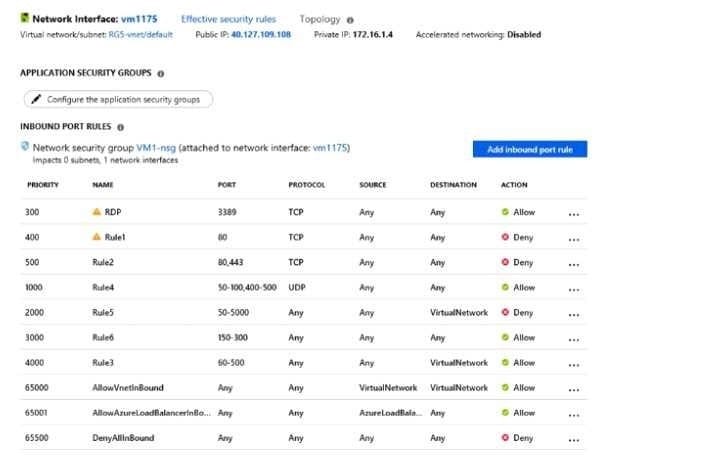
You deploy a web server on VM1. and then create a secure website that is accessible by using the HTTPS protocol. VM1 is used as a web server only.
You need to ensure that users can connect to the website from the internet.
What should you do?
A. For Rule4. change the protocol from UDP to Any
B. Modify the protocol of Rule4.
C. Modify the action of Rule1.
D. Change the priority of Rute3 to 450
-
Question 366:
You have an Azure subscription that contains the resources in the following table.
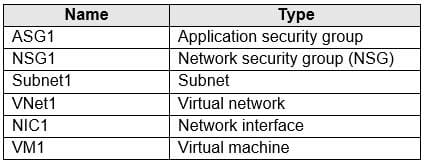
Subnet1 is associated to VNet1. NIC1 attaches VM1 to Subnet1.
You need to apply ASG1 to VM1.
What should you do?
A. Modify the properties of NSG1.
B. Modify the properties of ASG1.
C. Associate NIC1 to ASG1.
-
Question 367:
You have an Azure Active Directory (Azure AD) tenant.
All administrators must enter a verification code to access the Azure portal.
You need to ensure that the administrators can access the Azure portal only from your on- premises network.
What should you configure?
A. an Azure AD Identity Protection user risk policy.
B. the multi-factor authentication service settings.
C. the default for all the roles in Azure AD Privileged Identity Management
D. an Azure AD Identity Protection sign-in risk policy
-
Question 368:
You have an Azure subscription that contains two virtual networks named VNET1 and VNET2 and the users shown in the following table: Larger image
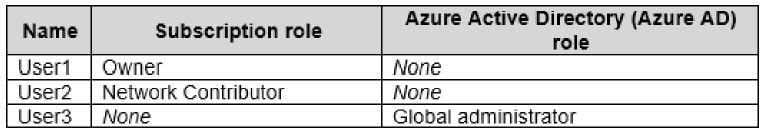
You need to identify which users can configure peering between VNET1 and VNET2. Which users should you identify?
A. User1 only
B. User3 only
C. User1 and User2 only
D. User1 and User3 only
E. User1, User2 and User3
-
Question 369:
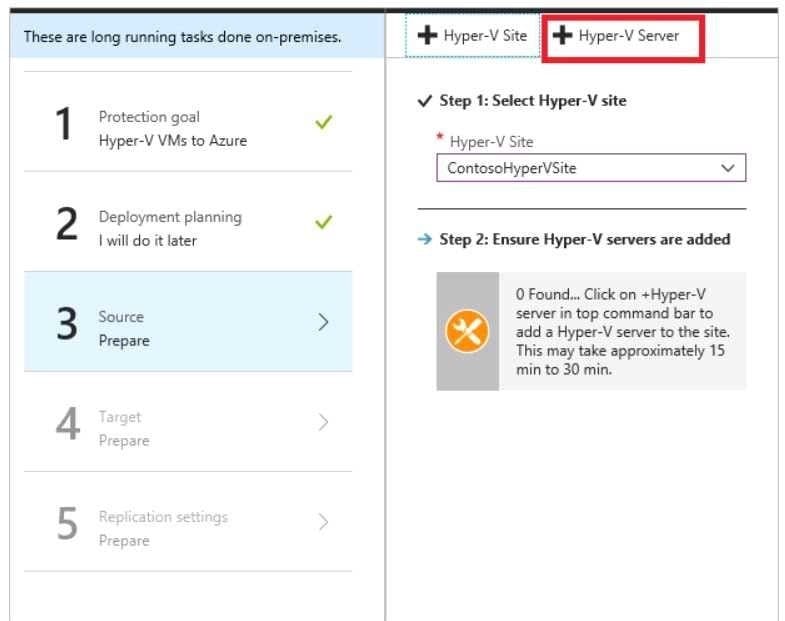
You have an on-premises network that contains a Hyper-V host named Host1. Host1 runs Windows Server 2016 and hosts 10 virtual machines that run Windows Server 2016.
You plan to replicate the virtual machines to Azure by using Azure Site Recovery.
You create a Recovery Services vault named ASR1 and a Hyper-V site named Site1.
You need to add Host1 to ASR1.
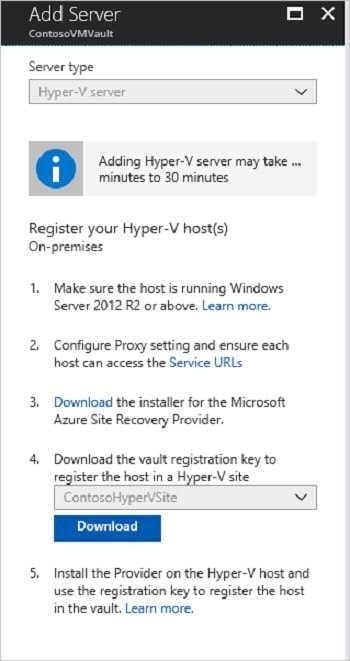
What should you do?
A. Download the installation file for the Azure Site Recovery Provider. Download the vault registration key. Install the Azure Site Recovery Provider on Host1 and register the server.
B. Download the installation file for the Azure Site Recovery Provider. Download the storage account key.
Install the Azure Site Recovery Provider on Host1 and register the server.
C. Download the installation file for the Azure Site Recovery Provider. Download the vault registration key. Install the Azure Site Recovery Provider on each virtual machine and register the virtual machines.
D. Download the installation file for the Azure Site Recovery Provider. Download the storage account key. Install the Azure Site Recovery Provider on each virtual machine and register the virtual machines.
-
Question 370:
You have an Azure Service Bus.
You need to implement a Service Bus queue that guarantees first in first-out (FIFO) delivery of messages.
What should you do?
A. Set the Lock Duration setting to 10 seconds.
B. Enable duplicate detection.
C. Set the Max Size setting of the queue to 5 GB.
D. Enable partitioning.
E. Enable sessions.
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your AZ-104 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.